- Cisco Community
- Technology and Support
- Security
- Endpoint Security
- Re: iexplorer.exe Exploit Prevention Detections? - Cisco AMP 6.2.9
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 12:51 PM - edited 02-20-2020 09:08 PM
Hello,
We're seeing the below Cisco AMP detection pop up around our company at different locations (differing countries). All locations are running IE 11.3. Alert details show VBScript executions detected. Has anyone experienced this as well? I'm curious if it's a bug/false alert. Can't seem to track down a root cause as the event details point only to Internet Explorer. Any insight would be greatly appreciated!
- Event Type: Exploit Prevention
- Computer: *********
- Hostname: *********
- IP: *********
- User: *********
- File: IEXPLORE.EXE
- File path: C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE
- Detection SHA-256: 74561199a186d36a6169d753bb88886be326e63416e75930f8ff929e93dd12ea
- By Application: iexplore.exe
- Application SHA-256: 7ccf5cf491eca6fb2d4178b86547f2fb88aca108927f1743962e14dbac2d9455
- Timestamp: 2019-03-27 15:34:26 +0000 UTC
Solved! Go to Solution.
- Labels:
-
Endpoint Security
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2019 06:22 AM - edited 04-25-2019 06:23 AM
Hi @rhussain,
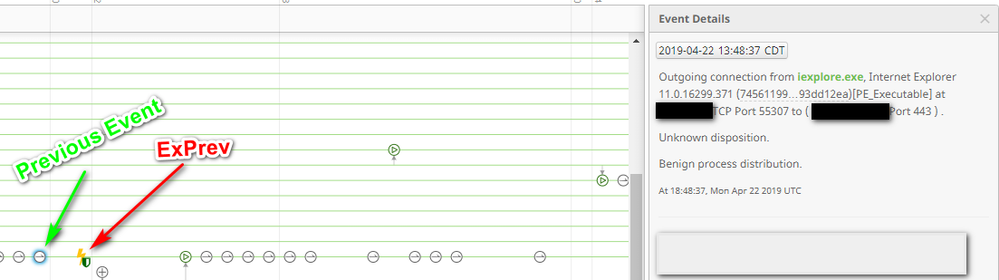
Working with TAC yesterday afternoon we were able to find a resolution for this issue. The technician mentioned seeing this frequently with logon pages for various websites. In our case, our company HR portal site was triggering the exploit prevention detections. This was discovered via viewing the device trajectory of one of the affected machines. Specifically, looking at the event just before the exploit prevention - an outgoing IE connection. Using the IP address we discovered it was connecting to the HR portal site.
The technician said adding that site to our trusted sites list will stop the detections - haven't had a chance to do that yet. Hope this helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2019 07:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 01:59 PM
I suggest collecting a diagnostic file from one of the endpoints and opening a TAC case for further investigation. I don't see any information on the hash provided at first glance but the diagnostic file may provide more information.
bbc95cfe1847b32123dfd6c4d3ef5dd8709ff03297b692fc4f31a9991c9290
Thanks,
Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2019 05:30 AM
Hi there,
We are having similar issues with iexplore exprev alerts and wondered if you managed to find a resolution in the end ??
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2019 08:13 AM
Hey @rhussain,
We're still seeing this occasionally but not as frequently. We just upgraded workstation connectors to 6.2.19 and it hasn't reappeared - I can let you know if this resolves the issue. If it does not I plan on opening a TAC case.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2019 07:27 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2019 03:52 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2019 06:22 AM - edited 04-25-2019 06:23 AM
Hi @rhussain,
Working with TAC yesterday afternoon we were able to find a resolution for this issue. The technician mentioned seeing this frequently with logon pages for various websites. In our case, our company HR portal site was triggering the exploit prevention detections. This was discovered via viewing the device trajectory of one of the affected machines. Specifically, looking at the event just before the exploit prevention - an outgoing IE connection. Using the IP address we discovered it was connecting to the HR portal site.
The technician said adding that site to our trusted sites list will stop the detections - haven't had a chance to do that yet. Hope this helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2019 07:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2019 07:29 AM
Thanks for the confirmation @orbT!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2019 03:32 AM
Hi @ITandCoffee
Thank you so much for the update. The problem for us is that we have machines connecting to many different sites which trigger the iexplore alerts and to have them individually added to the trusted sites will be quite a challenge.
The other thing we noted is not all our machines trigger the iexplore exprev alerts and this maybe due to the fact we have varying factors in our environment i.e. machines running different OS builds since machines failing Windows updates through GPO and therefore not consistent and we are seeing this issue.
I have come across following article which advises VBScript is deprecated in Internet Explorer 11 but for compatibility, VBScript execution is still permitted for websites in legacy document modes:
So I have tried disabling VBScript execution in Internet Explorer 11 for websites via Internet Zone and Restricted Sites Zone on a few machines and notice that iexplore alertings have stopped, but then I have also seen machines in our environment that already have these settings applied yet do not trigger the alerts.
I'm in the process of having all our machines updated to the same OS build and apply where necessary the Security Update for Internet Explorer 4014661 (https://support.microsoft.com/en-gb/help/4014661/cumulative-security-update-for-internet-explorer-april-11-2017) to confirm if that is the answer to fixing these iexplore issues we are seeing in AMP.
I will update in due course.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2019 10:00 PM
We are also seeing this issue. AMP keeps reporting that EXPrv blocked a BVScript execution in Internet Explorer but no signs of the script.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2019 08:05 AM
I am seeing a lot of these events most of them are vbscript execution which i believe are false positives. I have case open with TAC as to how am i supposed to investigate these and what type of remediation is needed. i have about 154 now on machines running 6.2.3 we will be upgrading our 6.1.7 endpoints to 6.2.3 so i expect to see even more. we have close to 200k endpoints
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide