- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Conditions missing for authentication policy in 2.3
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2017 10:39 AM
Hi everyone,
I am working on a POC for ISE using version 2.3. I'm new to ISE so I apologize if this is an obvious question. I couldn't find anything in the forum or docs either. Ok to the question.
I am following Katherine McNamara's blog post ISE - Dot1x Policy Configuration
In the post she uses a network access condition that matches certificate attributes that then results in specific identity sequences. I like this approach as it would allow us to collapse our corporate and byod SSIDs into one and assign different roles and VLANs starting with which certificate the client has. This is one of our goals with moving to a full NAC solution such as ISE.
My issue is when I go to add this condition in my authentication policy the condition is missing. Are there limitations on which conditions can be used where? Was there a change in how conditions work in 2.3? I've skimmed through documentation and the forums and I can't find any mention of this.
Screenshot of the condition:
Thanks!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2017 11:17 AM
You can use it in authorization policy rules only. [Correction] We can't use it in any policy set conditions but we can use it in authentication policy conditions inside a policy set.
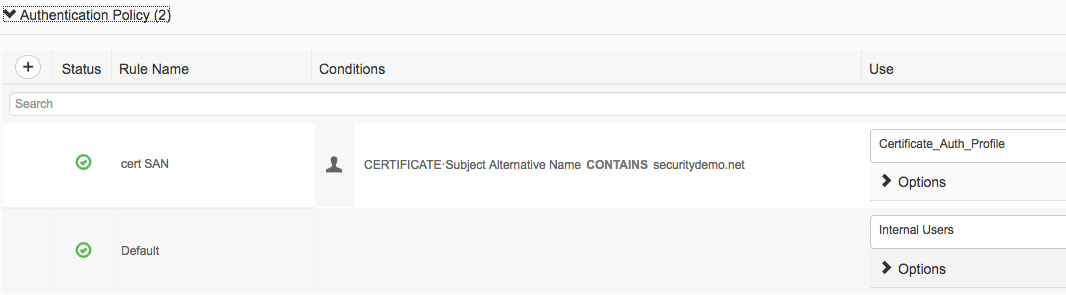
Certificate attributes are not yet available at that point in determining which protocols to use. It's removed to resolve CSCvc98033.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2017 10:52 AM
The right-hand-side (RHS) in this instance is a text input so we simply type in the text string.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2017 10:59 AM
See also the video walk-through of the policy UI in What's New in ISE 2.3?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2017 11:15 AM
Hi. The issue isn't creating the condition. I had our TLD in there, I just blacked it out. The issue is when I try and use the condition in a authentication policy. It doesn't show up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2017 11:17 AM
You can use it in authorization policy rules only. [Correction] We can't use it in any policy set conditions but we can use it in authentication policy conditions inside a policy set.

Certificate attributes are not yet available at that point in determining which protocols to use. It's removed to resolve CSCvc98033.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2017 11:26 AM
Ok, I think that was the answer I was looking for. Is there a doc I can reference that shows which condition types can be used where in a policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2017 11:37 AM
Please note that I revised my last response. AFAIK it's documented in CSCvc98033 only.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide