- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE BYOD: certificate generation failed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE BYOD: certificate generation failed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 03:47 AM
Hi.
I followed the directions stated on the Youtube link "ISE 2.2 Android Provisioning with EST Authentication (Certificate Generation Failed) - YouTube" but despite the mentioned configuration, again I get the same "Certificate Generation Failed" message during BYOD onboarding with single-SSID on my test Android 7.0 device. Also I'm using ISE 2.4 patch 1.
AS seen I've created a new condition and used it in a new Authz rule and put it before other rules. But I got no match hint and the same error message was and is still there!
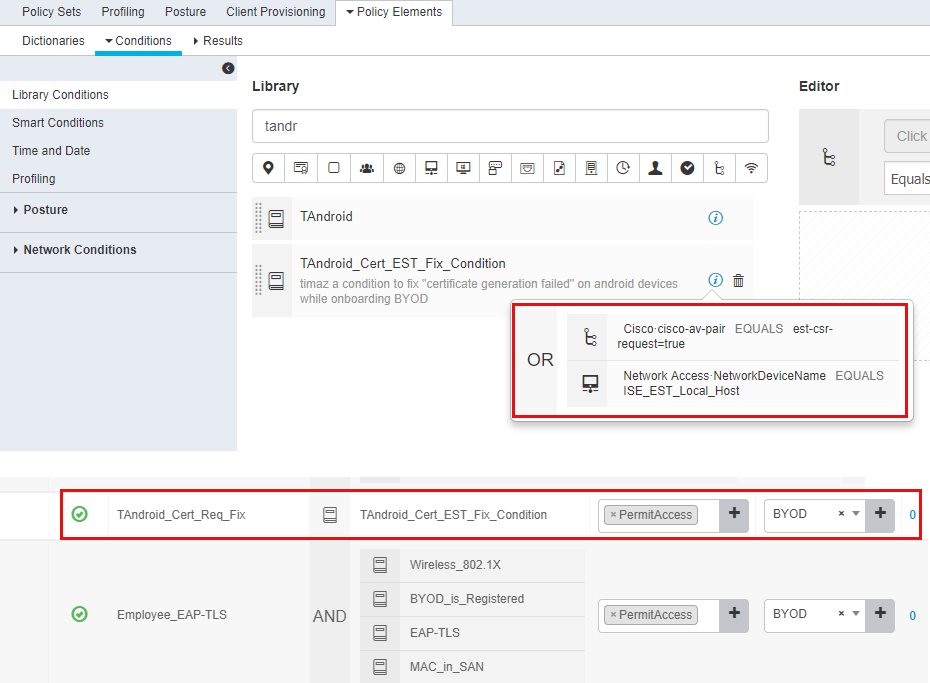
I have a firewall between clients and ISE server, but permitted all traffic from those clients destined everywhere; So it could not be considered a firewall-related issue.
How can I fix this? And I don't understand why this is necessary? I've not seen such recommendation or configuration on regular admin guides, videos or even on Cisco press books!
Thanks in advanced.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 04:37 PM
Hossein, are you using EST as opposed to SCEP? If not, the suggestions in the video is irrelevant. I suggest configuring basic BYOD using the wireless setup wizard and make sure it works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 11:07 PM
Hi;
No I configured SCEP in my lab. I hadn't heard anything about EST till this week. Actually I followed BYOD instructions stated on Cisco Community and double checked it with ISE Admin Guide and Cisco Press BYOD (2nd edition) book.If EST is irrelevant while SCEP is configured, then it would called normal if I hadn't heard anything about it in official guides.
Do you have any idea of what would be the reason behind error "Certificate Generation Failed"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2018 04:09 AM
I delete the NSA from the Android device but after being redirected to the BYOD portal and clicking on the icon to download NSA app from Google Play, a message pops up asking me to login again to that SSID, which takes me to the first page of the BYOD portal and this loops continues. I get this error on the Android browser.
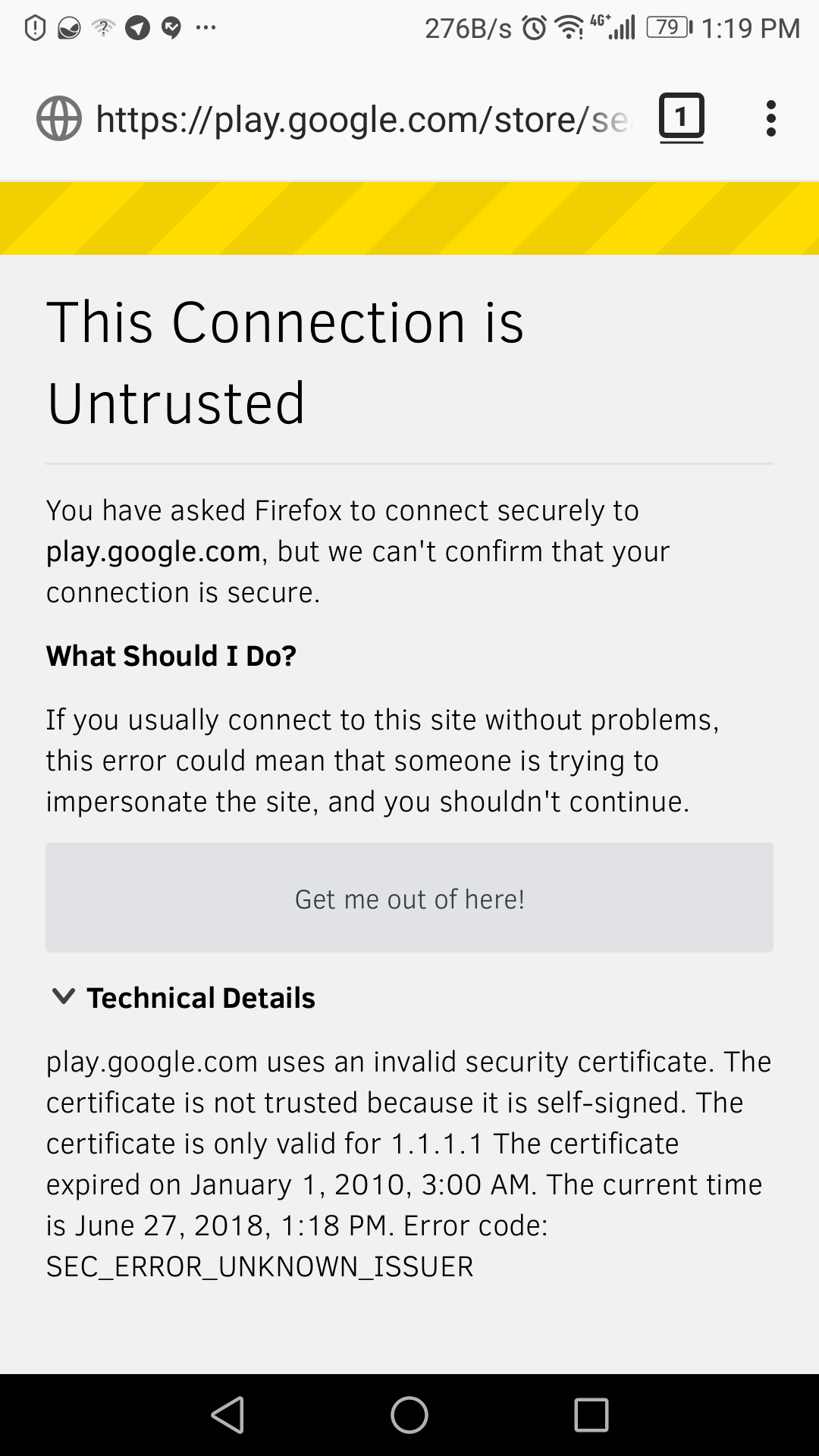
I tested it with other browsers but got the same type of error regarding SSL certificate of the webpage.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2018 05:11 AM
That’s because you’re not using a valid certificate that the endpoints know about
If you’re a Cisco partner would recommend using our dCloud setup our Deploying ISE POV kit to understand how it works with proper setup as these come with a well known certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2018 08:20 AM
So it's impossible to use Internal CA (without purchasing from a public well-known CA) along with BYOD. Did I get that right?
I checked the BYOD on my iPAD but it was unsuccessful too! I get redirected to the BYOD portal on ISE, but despite that I click on Trust and it shows the name of the certificate (as shown on the image), downloading the certificate fails.
I really got stuck.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2018 08:29 AM
Please follow the instruction here to trust the ISE certificate:
Trust manually installed certificate profiles in iOS - Apple Support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2018 11:16 PM
Hi.
The problem is I cannot download the certificate at the first place (The displayed certificate on the image above "TLABSERVER-CA.cer" is my internal Root CA certificate that includes my root ca public key), so there is no any certificate listed on the General > About > Certificate Trust Settings page. It shows only the first line which is "Trust Store Version" on that page. When I touch Download Now link at the image above, it says "Download Failed".
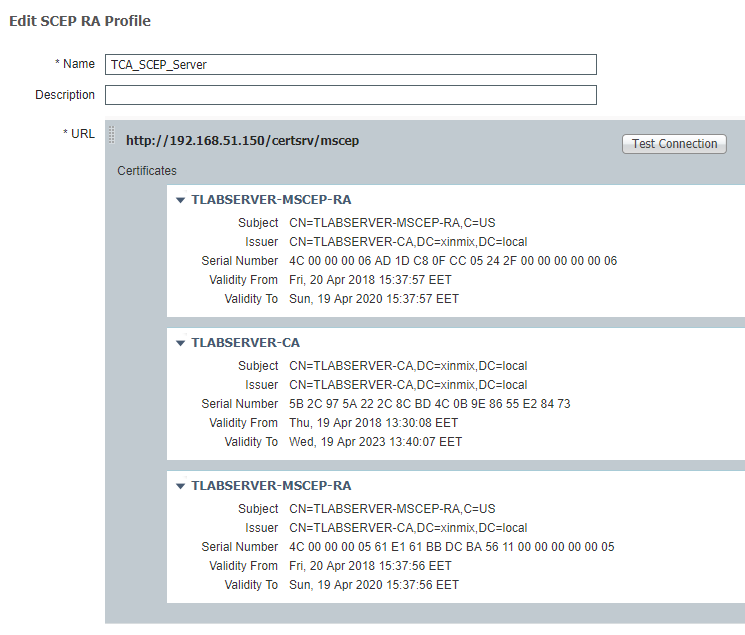
This image shows Administration > System > Certificates > Certificate Authority > External CA settings page on ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2018 03:22 PM
It looks like you are doing SCEP to external CA, is that what you are trying to do? If so have you configured MS CA to work with ISE? If this is not your intent or just to make sure onboarding is working, I suggest just leveraging internal CA instead.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2018 11:38 PM
Hi.
Yes I'm using SCEP and configured MS ADCS exactly as stated on the various Cisco Community documents created for BYOD. I used these documents:
How To: ISE & BYOD: Onboarding, Registering & Provisioning
How To: ISE & BYOD: Using Certificates For Differentiated Access
The certificate template is created on ADCS server based on these Cisco guides. I double-checked the configs but it seems there is no difference between what I did and the docs. You can take a look at the configs by clicking on this link, if you want. https://1drv.ms/u/s!AtnSgqfSTcPBgYZJcYdKJApOoy_DsQ
I'm using:
- ISE 2.4 patch 1
- 2 Windows server 2012 R2 computer (one as ADDC and another one as ADCS, which is not member of the internal domain)
- Cisco WLC 2504 software version 8.0.121.0
- Android 7.0
- iOS 11.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2018 06:21 AM
Hi;
Regarding your recommendations, I started using the ISE built-in root CA in my BYOD lab. It worked on Android this time. But iOS downloads the first certificate profile (which I think it is ISE root CA) and successfully verifies that, but it prompts to install another certificate (which I think it is BYOD cert for iPAD) and it is fails on that points, displaying an error message stating that the server certificate is invalid! There is only one certificate (which is installed and verified) on General > Profiles page on my iPad.
You see on the background that the root CA (ise1.xinmix.com) has been installed and verified before on my iPad.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2018 06:37 AM - edited 10-02-2018 07:48 AM
Do you have a well-known root certificate installed on the box. Otherwise iOS on boarding is not gonna work correctly. Also have you followed the BYOD guide mentioned in the post
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2018 07:30 AM - edited 10-03-2018 03:55 AM
What do you mean by "route certificate"?
Update:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 01:05 PM
On this Apple iPad, you are using FireFox app instead of the regular mobile Safari. Firefox is not opening the certificate, even if it downloaded, and installing it under Settings > General > Profiles.
First, ensure that the ACL is properly allowing access to the ISE PSN. And, then use Apple iOS mobile Safari, instead of Firefox app.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2018 01:10 PM
The fact that the connection is untrusted to Google play store appears either due to the connection not permitted by your ACL or intercepted by a web proxy server.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide




