- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE BYOD: certificate generation failed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE BYOD: certificate generation failed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 03:47 AM
Hi.
I followed the directions stated on the Youtube link "ISE 2.2 Android Provisioning with EST Authentication (Certificate Generation Failed) - YouTube" but despite the mentioned configuration, again I get the same "Certificate Generation Failed" message during BYOD onboarding with single-SSID on my test Android 7.0 device. Also I'm using ISE 2.4 patch 1.
AS seen I've created a new condition and used it in a new Authz rule and put it before other rules. But I got no match hint and the same error message was and is still there!
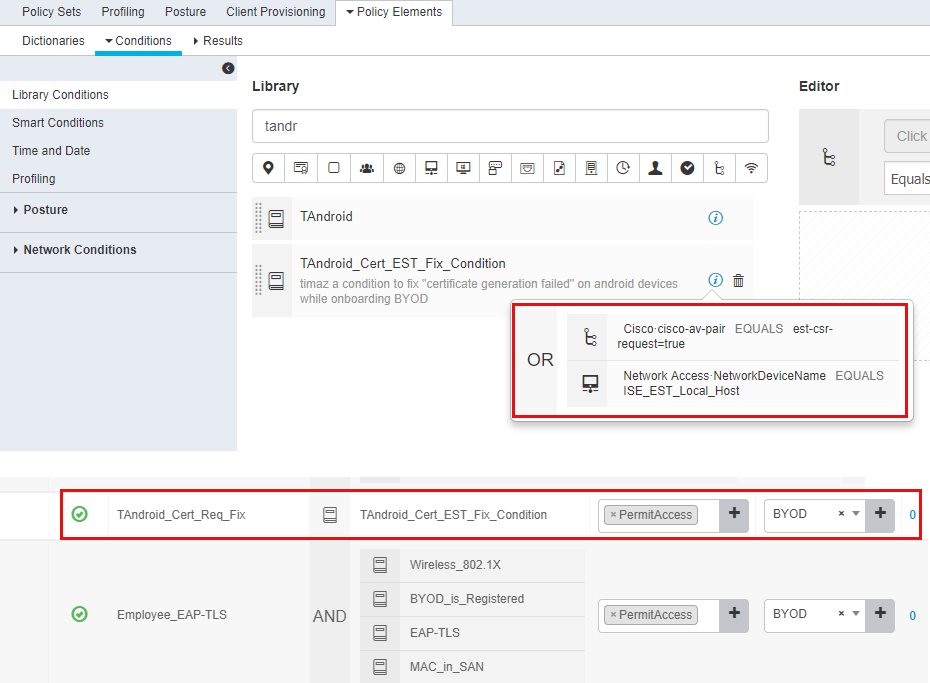
I have a firewall between clients and ISE server, but permitted all traffic from those clients destined everywhere; So it could not be considered a firewall-related issue.
How can I fix this? And I don't understand why this is necessary? I've not seen such recommendation or configuration on regular admin guides, videos or even on Cisco press books!
Thanks in advanced.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2018 06:45 AM
Looking at your Android screenshot again, it says the certificate is only valid for 1.1.1.1. Although no longer a recommended value for WLC virtual interface, 1.1.1.1 is likely what your WLC has for its virtual interface. If so, then it's an indication that the WLC ACL is not allowing the connection to play.google.com and that the WLC is enabled for HTTPS redirection.
If this is not helping, please engage Cisco TAC to troubleshoot further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2018 08:58 AM
I have 2 different ACLs on WLC, one for Android and one for iOS. (My ISE IP address is 10.1.204.168).
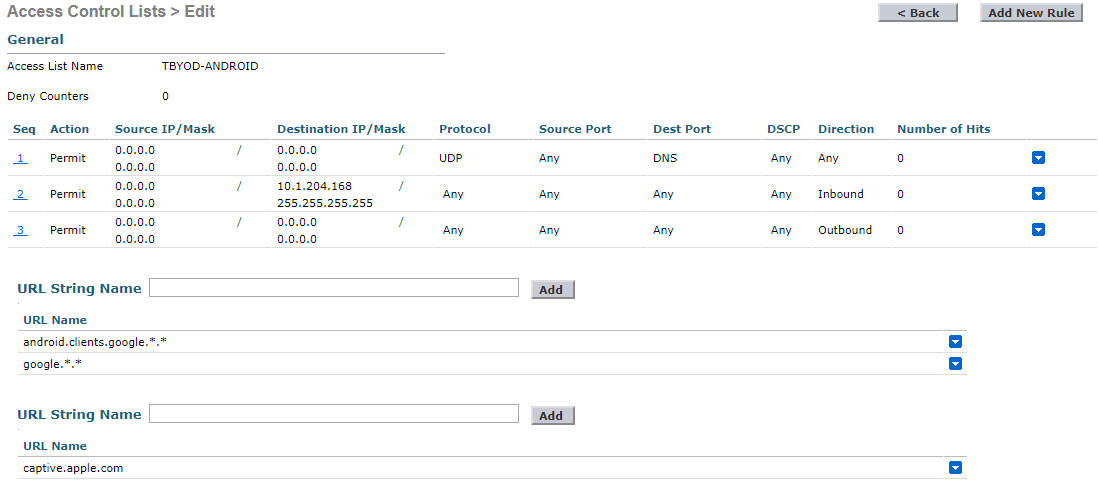
The only difference between 2 of them is URLs. Based on the docs I enabled HTTPS redirect on WLC. Shouldn't it be that way?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2018 05:09 PM
The thing with Android ACL is that it keeps changing. I do not think your DNS ACL really working. Unfortunately, the one worked in our alpha network 1.5 years ago is no longer working to access Android Play store.
It would be easier to restrict the internal network access but to allow Internet or use a separate network to download the Cisco NSW app from the store.
Here is an ACL to restrict internal access from one of our test setups, where the internal network is 10.0.0.0/8, DNS is 10.1.100.10, and ISE 10.1.100.21:
(Cisco Controller) >show acl detailed PERMIT-Internet
Source Destination Source Port Dest Port
Index Dir IP Address/Netmask IP Address/Netmask Prot Range Range DSCP Action Counter
------ --- ------------------------------- ------------------------------- ---- ----------- ----------- ----- ------- -----------
1 In 0.0.0.0/0.0.0.0 10.1.100.10/255.255.255.255 17 0-65535 53-53 Any Permit 207
2 In 0.0.0.0/0.0.0.0 10.1.100.21/255.255.255.255 Any 0-65535 0-65535 Any Permit 1586
3 In 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0 1 0-65535 0-65535 Any Permit 0
4 In 0.0.0.0/0.0.0.0 10.0.0.0/255.0.0.0 Any 0-65535 0-65535 Any Deny 43
5 Any 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0 Any 0-65535 0-65535 Any Permit 34780
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2018 07:44 PM
Following Hosuk's Using DNS-Based ACL for Chromebooks and Android Devices, it's working for my Nexus 5X/Android 8.1 on a WLC 5520 running AireOS 8.5.131.0 and AP 2702i.
Earlier it was not working on vWLC running 8.0.120.0, due to CSCus61445.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2018 03:47 AM
I pinged the various Google sites and created ACL entries on the WLC with those IP addresses and again it didn't work.
I tested on my iPAD, this time with Safari browser instead of Firefox, and this time I redirected a little further. It asked me to install a profile and after I accept the prompt, it installed the root CA, but it asked me to install the profile second time, but at this point I got an error message like this.
you can see that my root CA certificate has been verified at the first step. but the 2nd step failed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2018 08:57 AM
Since your domain is .local, I believe either your root CA is a private enterprise PKI or the server certificate is self-signed. In that case, please read how to Trust manually installed certificate profiles in iOS - Apple Support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2018 12:10 PM
For Google Android, I would suggest you to try the ACL PERMIT-Internet that I posted in comment 14. Or, get the NSW app first using another WLAN or some other means.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2018 03:16 PM
I just worked with someone who had .local and apple doesn’t like that even if you manually install cert
You Will need to move away from using the TLD of .local
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-10-2018 12:34 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2024 03:28 AM
Hi @ciscoworlds,
were you able to solve the issue?
I have the same issue with ISE v3.2p4 using WLC 3500 v8.10.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

