- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: [4Juniors] Implementation of authentication RADIUS and DOT1X.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
[4Juniors] Implementation of authentication RADIUS and DOT1X.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2023 03:13 AM
- ISO: c3745-adventerprisek9-mz.124-25d.image, c3745-adventerprisek9_ivs-mz.124-15.T8.image, linux-microcore-6.4.img
This 'littleguy' have some configs to do it:

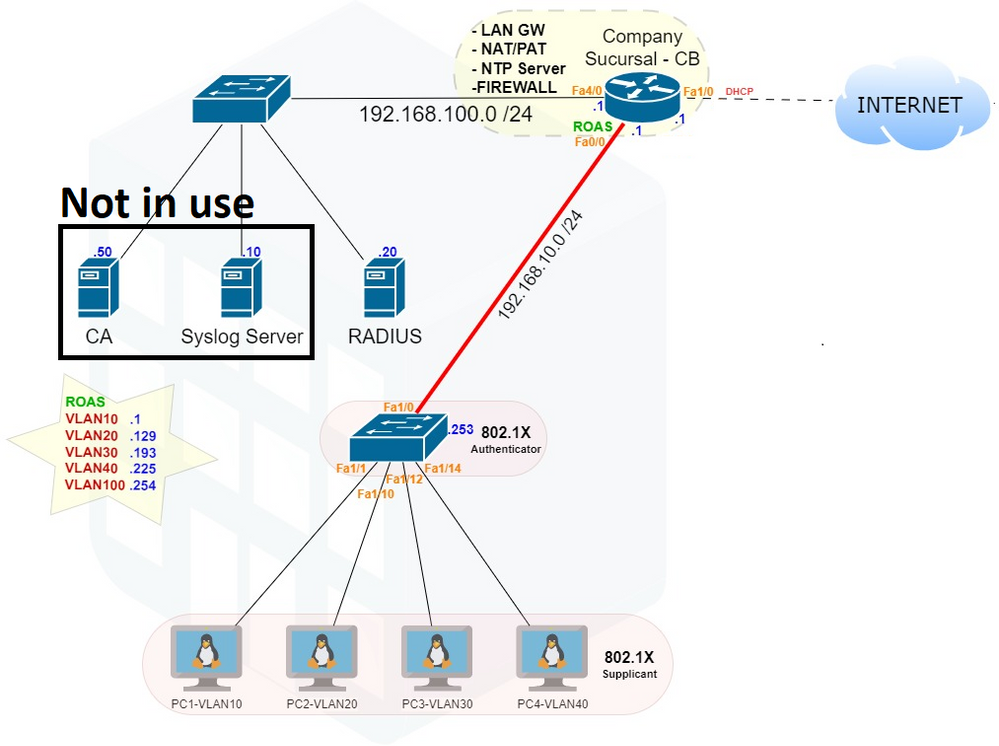
a: basic config -> Router
interface FastEthernet INT/ID
ip address IP-ADDR MASK-ID
no shutdown
% R _CB : 0/0 – 192.168.10.1 255.255.255.0 ; 1/0 – dhcp %Public IP ; 4/0 - 192.168.100.1 255.255.255.0
!
ip nat inside source list 10 interface FastEthernet1/0 overload
access-list 10 permit 192.168.10.0 0.0.0.255 %All private addr are translated for fa1/0
!
interface range FastEthernet0/0, f4/0 %private interfaces
ip nat inside
!
interface FastEthernet 1/0 %external interface
b: RADIUS login -> Routers & Switches
username backup password backup %local credentials if AAA offline
aaa new-model
aaa authentication login default group radius local %%RADIUS server authenticates login
radius-server host 192.168.100.20 auth-port 1812 acct-port 1813 key gns3 %RADIUS addr & ports + validation key
c: DOT1X -> Switch
aaa authentication dot1x default group radius %%%
aaa authorization network default group radius
dot1x system-auth-control
!
int range FastEthernet1/1 – 9
dot1x port-control auto
dot1x pae-authenticator %ports are authenticated by this device (the authenticator)
MY GOAL: help as much as I can, because this simple application help prove this concept
But for more expert colleagues, I want to receive opinions and improve this post (for future ones).
And, with this topology it's possible to un-configure VLAN and give the RADIUS server the ability to atribute a respective VLAN (after given VLAN, DHCP will give IP accordingly)? NOTE: assuming the GNS3 AAA docker.
Thanks you all.
(If similar post already exists, please tag me!)
Portuguese tags: Segurança em Redes, Autenticação RADIUS (AAA), Exemplo simples.
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2023 08:42 PM
Hi. Nice one! That's a great initiative for someone wanting to play with 802.1X using GNS3.
I would only add one thing - the IOS images are very old and things have changed quite a lot in IOS-XE (IBNS 2.0 etc.) - while the MAB/802.1X concepts are mostly unchanged since those old IOS images, the commands for newer IOS and IOS-XE are quite drastic. And this GNS lab setup does assume that the user has a (legit) image of IOS (or IOSvl2 etc.) - there is an IOS-XE image available as part of Cisco CML - but it's very resource hungry and it's quite new.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2023 07:52 AM
@Arne Bier big thanks for your appreciation and recommendations the goal is to keep simple and focus on learning protocols. In my college it is a harsh reality, everything must be virtualize. The given 'official images' are indeed old (c3745), but for a free and educational purpose we use what is available (tried to ask Cisco Portugal for some images, but no luck hahah).
Discussing this with a colleague, who sent me this: Introduction to Cisco IOS XE (networklessons.com) and suggested the Cisco CSR1000v (available for free to GNS3), but it cost at a bit RAM on LAB PCs of 4GB (maybe next year the school will have a workstation or, maybe, CML). Once again thanks for the heads up!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2023 05:17 PM
I've had CML subscription for a number of years and the images that come with the CML work quite well - each update to CML contains newer images. So, I would recommend scraping together a few Pennies and buying a CML subscription.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



