- Cisco Community
- Technology and Support
- Security
- Network Access Control
- 802.1X Authentication with restricted Vlan : re-authentication attempts not happening
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2020 05:26 AM
Hi all,
I have some doubts regarding the real behavoiur of Cisco IOS and IOS XE when a device that failed dot1x authentication is put in the fail vlan.
From documentation I see that :
Users who fail authentication remain in the restricted VLAN until the next re-authentication attempt. A port
in the restricted VLAN tries to re-authenticate at configured intervals (the default is 60 seconds). If
re-authentication fails, the port remains in the restricted VLAN. If re-authentication is successful, the port
moves either to the configured VLAN or to a VLAN sent by the RADIUS server. You can disable
re-authentication.
But what I see is that the reauthentication never happen; to force re-authentication I have to configure local reauthentication timers ( authentication timer reauthenticate …. ) , but this solution is not feasible in general because it ovverrides the timers pushed by radius in case device is authenticated.
The scope is that the device in restricted vlan after it is checked and fixed need to be reauthenticated and put the correct vlan.Is it possible ?
Thanks for all feedbacks !!
This is our typical config :
Building configuration...
!
interface GigabitEthernet1/0/19
description verso presa Lan Telefono IP + PC
switchport access vlan 22
switchport mode access
switchport voice vlan 122
srr-queue bandwidth share 10 10 20 60
queue-set 2
priority-queue out
authentication control-direction in
authentication event fail action authorize vlan 22
authentication event server dead action authorize vlan 22
authentication event server dead action authorize voice
authentication event no-response action authorize vlan 22
authentication event server alive action reinitialize
authentication host-mode multi-domain
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
mab
mls qos trust device cisco-phone
mls qos trust cos
dot1x pae authenticator
dot1x timeout tx-period 3
spanning-tree portfast edge
spanning-tree bpduguard disable
service-policy input PC-SoftPhone+HardPhone
end
Interface: GigabitEthernet1/0/19
MAC Address: 2c41.38b0.d37b
IPv6 Address: Unknown
IPv4 Address: 10.69.123.128
User-Name: host/IUSP9X3Z.hd00.UNICREDITGROUP.EU
Status: Authorized
Domain: DATA
Oper host mode: multi-domain
Oper control dir: in
Session timeout: N/A
Restart timeout: N/A
Periodic Acct timeout: N/A
Common Session ID: 0A4578850000003705DCBF6B
Acct Session ID: 0x0000004C
Handle: 0x7A00001D
Current Policy: POLICY_Gi1/0/19
Service Template: AUTH_FAIL_VLAN_Gi1/0/19 (priority 150)
Vlan Group: Vlan: 22
Method State
Solved! Go to Solution.
- Labels:
-
AAA
-
Guest
-
Multi-Domain
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2020 10:04 PM - edited 11-07-2020 10:06 PM
According to ISE Secure Wired Access Prescriptive Deployment Guide ,
authentication timer reauthenticate server
Should allow any reauthentication timers assigned by ISE / RADIUS to override any local settings.
You did not show any ISE LiveLog details so it's unclear what you assigned the port from ISE and why.
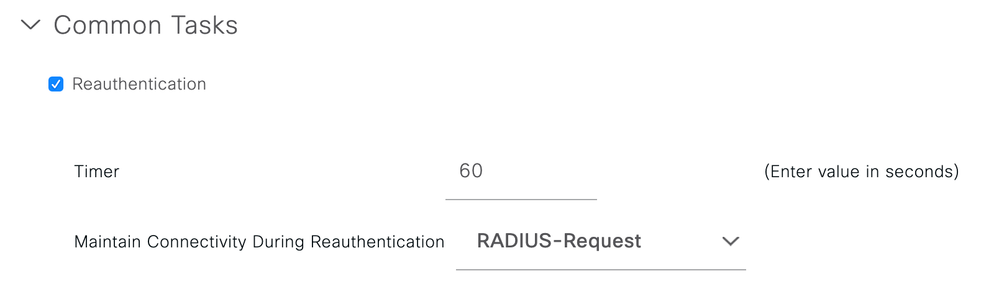
Verify you are downloading reauthentication timers from ISE in your Authorization Profile under
Policy > Policy Elements > Results > Authorization > Authorization Profiles :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2020 10:04 PM - edited 11-07-2020 10:06 PM
According to ISE Secure Wired Access Prescriptive Deployment Guide ,
authentication timer reauthenticate server
Should allow any reauthentication timers assigned by ISE / RADIUS to override any local settings.
You did not show any ISE LiveLog details so it's unclear what you assigned the port from ISE and why.
Verify you are downloading reauthentication timers from ISE in your Authorization Profile under
Policy > Policy Elements > Results > Authorization > Authorization Profiles :
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide