- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ACS 5.1 - tacacs+ issue witch "network access" access services
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2010 03:43 AM - edited 03-10-2019 05:19 PM
hi everyone,
can anyone explain why tacacs+ can't be used with network access services?
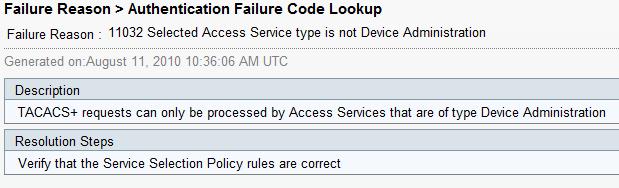
I know that main purpose of tacacs is command authorization but as I remember with ACS 4.2 it was possible. For example for PPP purpose.
thx and regards
Przemek
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2010 11:54 PM
TACACS+ requests can only be handled by access services with the Service Type set to "Device Administration".
If type is NetworkAccess it will fail. Please check the Service Type defined for the Access Service "VPM-access"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2010 01:45 PM
On ACS 5.x
Default Device Admin = Tacacs+
Default Network Access = Radius
This is determined by the service selection rules. Without other information it appears that you tried to process a Tacacs request with the Default Network Access somehow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2010 11:48 PM
thx for reply
I think this is not the case that Default Network Access is selected in response to TACACS request cause I have other "Access Services" created and default one is even deactivated.
even in log there is my vpn-access-rule selected

In your opinion this should work? I mean using Tacacs+ with Network Access service.
Can anyone confirm it?
regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-11-2010 11:54 PM
TACACS+ requests can only be handled by access services with the Service Type set to "Device Administration".
If type is NetworkAccess it will fail. Please check the Service Type defined for the Access Service "VPM-access"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2010 12:07 AM
thx for explaination
I was afraid that this was the case. So if ASA need to control command authorization and verify user credentials in vpn policy (with attributes for that vpn policy) I need to define 2 seperate AAA servers? First as tacacs and 2nd as RADIUS?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2010 12:29 AM
Not sure if I follow the question. However, a single ACS server can be used to process both RADIUS and TACACS+ requests
This is in fact the sample services and selection rules that are provide upon product installation. Performs service selection according to the protocol and then selects either: "Default Device Admin" and "Default Network Access" accordingly
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2010 12:51 AM
I meant that in ASA I needed to define 2 aaa servers (one for tacacs and one for radius).
When integrating ASA with ACS4.2 I could use only tacacs server (for command authorization and vpn policy as well).
thx and regards
P
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide