- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Hi EdUnfortunately I don't
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ACS 5.3 with intermediate certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2014 03:47 AM - edited 03-10-2019 09:51 PM
Hi
Is there a way to provide all the necessary intermediate certificates to an ACS v5.3 so that it can provide the full chain to the client during a 802.1x PEAP authentication?
Already tried to install the EAP certificate with the chain and also installed the issuing CA as trusted root. I know that installing it as trusted root shouldn't have any effect but that's the way how Cisco solved it on the ASA platforms.
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-03-2014 12:25 PM
Hi,
ACS will never supply certificates to clients on a PEAP certificate challenege.
It will only propose the ACS certificate for verification (not for install).
The client should have the intermediate and root installed beforehand to make this work.
Rate if Useful :)
Sharing knowledge makes you Immortal.
Regards,
Ed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2014 06:54 AM
Hi Ed
If you get a certificate e.g. from Verisign it will be issued from a subordinate and not from the root itself. So if you want to do PEAP-MS-CHAP with an unmanaged client who has only the root certificates installed and is configured to verify the server certificate during the PEAP TLS tunnel establishment you will need to provide the whole cert chain to the client, so it can establish the trust link up to the root. So there must be a way of providing the whole chain. Otherwise the ACS is useless for authentication with unmanaged clients who verify the server certificate.
Kind regards
Roberto
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2014 10:58 AM
Unfortunately, any radius server (not just the ACS) will be not be able to supply the certificate (intermediate or root) for installation to the client during the PEAP tunnel process as that is not as per RFC.
There is some additional feature to facilitate this on Cisco ISE, but only an ISE expert can comment on that.
Could you elaborate, on unmanaged client?
What type of client would this be, is this a BYOD environment?
Rate if Useful :)
Sharing knowledge makes you Immortal.
Regards,
Ed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2014 07:22 AM
Hi Ed
It's not about INSTALLING a certificate. It's about providing the whole chain during authentication so that the client can establish itself the link to the responsible root. As any well managed webserver should do who runs on HTTPS.
Here the wireshark example of a TLS tunnel to https://supportforums.cisco.com/
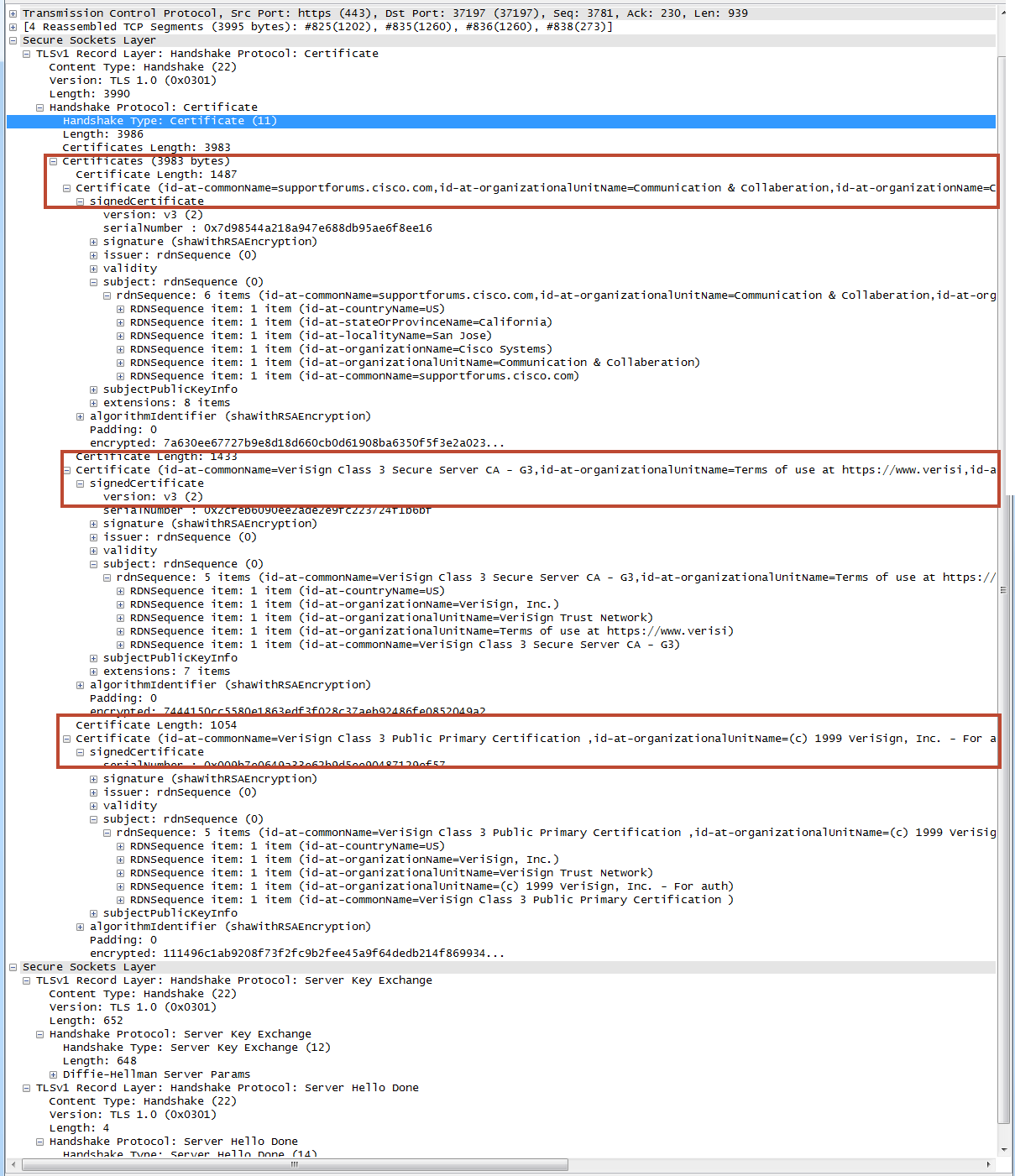
And we need the ACS to behave the same during the establishment of the TLS tunnel during a PEAP authentication.
Regards
Roberto
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2014 05:06 PM
Roberto,
Do you have a capture with ACS?
If not, I will test it out.
Regards
Ed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2014 06:58 AM
Hi Ed
Unfortunately I don't have a capture, as I don't have access to the network infrastructure between the ACS and the WLC. And Wireshark doesn't capture the PEAP authentication on my wireless NIC during the connection phase.
If you can give it a try it would be great. But from my current tests the ACS doesn't seem to do that, as the clients without the intermediates refuse to talk to the "RADIUS server", as they can't verify it's identity against a trusted root. With the intermediate cert locally installed they work well and trust the "RADIUS Server".
Regards
Roberto
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2014 01:52 AM
The ICA will be only provided if the ICA is added to the CA list under:
Users and Identity Stores --> Certificate Authorities
After that the correct cert chain will be present in the PEAP process.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide