- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ACS 5.4 and Juniper J-Web
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 05:42 AM - edited 03-10-2019 08:29 PM
Hi
I have set up an ACS 5.4 box and have some test devices connected to it.
Cisco and Juniper, both working fine using TACACS
I can connect to both using SSH or Telnet but my problem is the J-Web Juniper GUI
I can access the J-web no problem with the root account.
I can not seem to get it to work, no matter what I try. Here is my shell from the ACS box
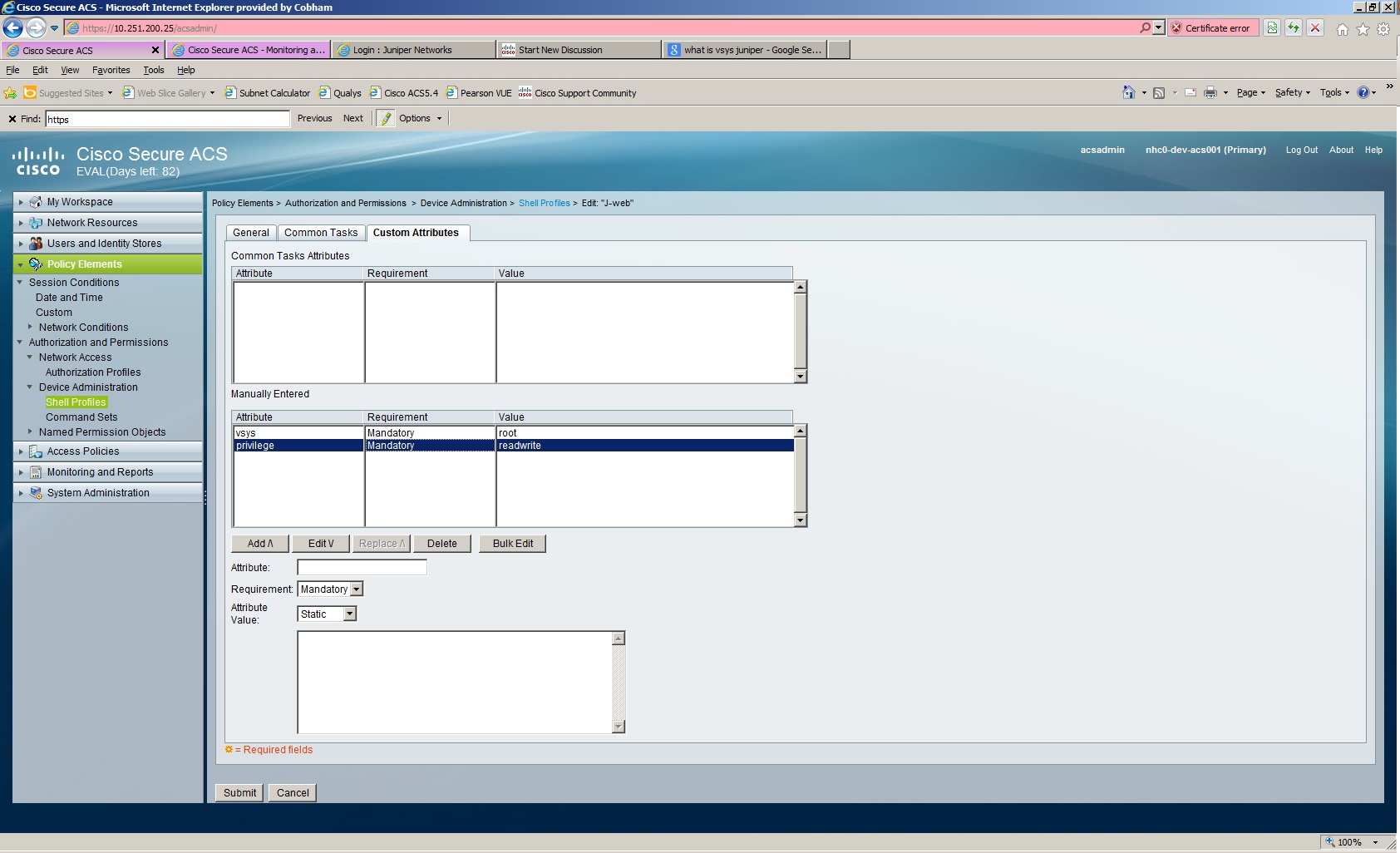
And the following Juniper configuration. I have tried binding the local-user-name attribute to both the remote and remoteadmin with no luck. Anyone have any ideas how I can resolve this??? Or if its even possible?
version 9.6R1.13;
system {
host-name Juniper-Firewall;
authentication-order [ tacplus password ];
root-authentication {
encrypted-password "$1$1tRuy9o2$LwSPxNwe4XGNMOMIMo1pd1"; ## SECRET-DATA
}
tacplus-server {
10.251.200.25 {
secret "$9$zaUL6/AtuOIRS5QF/CuEhws2"; ## SECRET-DATA
timeout 10;
single-connection;
}
}
accounting {
events [ login change-log interactive-commands ];
destination {
tacplus;
}
}
login {
user admin {
uid 2001;
class super-user;
authentication {
encrypted-password "$1$MNUZBLFW$X2sJL/UTgRYcgBNV4RLe.0"; ## SECRET-DATA
}
}
user remote {
full-name "Remote User";
uid 2025;
class operator;
}
user remoteadmin {
full-name "Remote Admin";
uid 2026;
class super-user;
}
}
services {
ssh;
telnet;
web-management {
https {
system-generated-certificate;
interface fe-0/0/0.0;
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2013 05:11 PM
I was working on a almost similar issues today and he confirmed that he is able to access J-WEB with the tacacs credentials.You may check his config here: https://supportforums.cisco.com/message/3953224#3953224
Going through your config it seems you have not defined/created classes like he did:
for example:
login {
class RO-CLASS {
permissions [ view view-configuration ];
}
class RW-CLASS {
permissions all;
}
user JUNOS-RO {
uid 2000;
Jatin Katyal
- Do rate helpful posts -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 06:03 AM
What do you see in acs/tacacs logs while authenticating for J-web?
Is that possible we can run the packet capture on the ACS 4.2 ( in case it is windows)?
Jatin Katyal
- Do rate helpful posts -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 07:25 AM
Hi Jatin
I am running ACS 5.4, so I am not sure what you mean when you say packet capture on 4.2 (I don't have this)
Which logs should I access? And is there an issue with windows?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 07:40 AM
sorry, my bad. I was helping someone on ACS 4.2 as well.
Look at tacacs authorization under logging and monitoring. I mentioned windows because in case of appliance either we have to take tcpdump or span the switch port to take packet capture.
Jatin Katyal
- Do rate helpful posts -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 07:51 AM
I am not seeing any recent entries in the tacacs authorization. I can see the SSH highlighted below. I am not seeing any http logging, not sure if I have to turn something on in ACS?
My Juniper is stating, failure with the Tacacs user and success with the root user?
root@Juniper-Firewall> show log messages
May 30 15:41:32 Juniper-Firewall clear-log[11338]: logfile cleared
May 30 15:37:00 Juniper-Firewall last message repeated 2 times
May 30 15:41:45 Juniper-Firewall checklogin[11346]: WEB_AUTH_FAIL: Unable to authenticate httpd client (username Jweb)
May 30 15:47:01 Juniper-Firewall checklogin[11358]: WEB_AUTH_SUCCESS: Authenticated httpd client (username root)
May 30 15:48:26 Juniper-Firewall checklogin[11399]: WEB_AUTH_FAIL: Unable to authenticate httpd client (username Jweb)
May 30 15:48:55 Juniper-Firewall sshd[11402]: Accepted password for jweb from x.x.x.x port 54501 ssh2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 09:04 AM
have you gone through this
http://kb.juniper.net/InfoCenter/index?page=content&id=KB24437
Jatin Katyal
- Do rate helpful posts -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 09:08 AM
OR
You may try this:
- In the J-Web user interface, select Configure>System Properties>User Management.
- Click Edit. The Edit User Management dialog box appears.
- Select the Authentication Method and Order tab.
Just make sure the first authentication method is tacacs and fallback is local.
Jatin Katyal
- Do rate helpful posts -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 10:59 AM
I had seen that post and it is exactly the same as what I am seeing but my settings were already configured correctly.
I have doubled checked the settings via Jweb and they are as expected.
I have no idea why this doesn't work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 11:03 AM
I could only see the below listed error.
May 30 15:48:26 Juniper-Firewall checklogin[11399]: WEB_AUTH_FAIL: Unable to authenticate httpd client (username Jweb)
Is there any detailed debbuging or logging related to tacacs or aaa that we can run and further isolate this issue.
We can also run the packet capture on the ACS side and take a look.
Jatin Katyal
- Do rate helpful posts -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 11:16 AM
how do i run the packet capture on the acs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2013 11:22 AM
Well you can take tcpdump and that can only be done via bash shell/root access. I may not be able to help you here as there is a special patch that need to be applied on the ACS before we run tcpdump. For now, would it be possible for you to span the switch port where acs is connected.
do share the tacacs key so that we can decode it.
Jatin Katyal
- Do rate helpful posts -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2013 06:21 AM
I spanned the Juniper connected port and then attempted to connect to the GUI
I could see my https sessions within wireshark but there was no inidication of any Tacacs authentication occuring. I'd at least expect some TCP traffic on port 49?
I repeated the logon via the root account and saw exactly the same thing, except that the root acount successfully logged into the device
I am sure that this is a mapping issue in that my user (jweb) is not mapping correctly within the command set.
I have vsys set as mandatory root and privilege as mandatory but this is isn't working (in my opinion)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2013 06:49 AM
since ssh is working with tacacs there should not be a port tco 49 issue.
The below listed config confirms that https is enabled using self-signed certificate.
services {
ssh;
telnet;
web-management {
https {
system-generated-certificate;
interface fe-0/0/0.0;
If I am not wrong, you don't even see passed or failed authentication on ACS under tacacs authentication.
Jatin Katyal
Do rate helpful posts -
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2013 06:57 AM
Hi Jatin
Good point about the SSH, I have been looking at this too long
You are correct, I see nothing in the ACS tacas authentication report for my HTTPS connections
This is a SSH test followed by a Telnet test, which always work
May 31,13 1:55:49.256 PM | May 31,13 1:55:49.230 PM |
| jweb | Juniper Firewall | Vendor:Vendor:Juniper, Device Type:All Device Types:Firewall, Location:All Locations:Marlow | J-Web | Internal Users | All Groups:Jweb | nhc0-dev-acs001 | ||
May 31,13 1:55:32.216 PM | May 31,13 1:55:32.186 PM |
| jweb | Juniper Firewall | Vendor:Vendor:Juniper |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2013 07:08 AM
Is there any specific section on juniper where you need to point the J-WEB authentication towards tacacs first and then local. I feel that section is still checking the tacacs user against the local database and getting failed.
Jatin Katyal
- Do rate helpful posts -
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

