- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Hi Priya and thanks for your
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ACS 5.8.0.32 not matching Active Directory Authorization Rules for TACACS after upgrade from 5.6
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2016 06:09 AM - edited 03-10-2019 11:28 PM
Hi Guys;
We had a primary/secondary ACS 5.6 deployment working beautifully with all of our switches authenticating (TACACS) with our Active Directory accounts.
We decided to upgrade to version 5.8.0.32. Both virtual machines upgraded successfully (at least that was the message form each vm after upgarded).
But, after the upgrade, bot ACS were disconnected form the AD. We rejoined both of them successfully, but now, after the upgrade, all of the authorization rules referencing AD (active directory accounts) are being ignored and it goes directly to the default deny rule.
The local accounts existing on the ACS authenticate successfully. It is the Rules referencing AD accounts.
All diagnostic tests pass successfully., ecen in the ACS logs, the users from AD gets authenticated, but in the authorization rules the ACS ignores the existing AD rules and uses the Default deny Rule.
Any ideas?
Thanks in advanced Guys!
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2016 02:08 AM
Hi,
Can you please confirm whether Binary certificate comparison is enabled in Certificate Authentication Profile object?
I mean the whether following check box is enabled?
"Perform Binary Certificate Comparison with Certificate retrieved from LDAP or Active Directory"
This configuration is available in GUI "Users and Identity Stores > Certificate Authentication Profile"
If yes, can you please disable and try.
If not, Can you please share the list of steps shown in the report in failed case.
Thanks
Radhakrishna
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2016 06:16 AM
Hi and thanks for your reply;
It was disabled. I proceeded to enabled it, but same result. The rules related to AD1 authentication are ignored and authorization is denied by ACS.
Below the steps of a failed authentication attempt of my AD Account on a Cisco switch:
StepData=19=c191341 : StepData=20=na.am.lilly.com : StepData=21=corp.lilly.com : StepData=23=C191341@na.am.lilly.com : StepData=26=C191341@na.am.lilly.com : IdentityAccessRestricted=false
Thanks again.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2016 10:54 AM
Did you access ACS 5.8 via Chrome as a browser? The Reason I am asking because no version of ACS supports Chrome browser - ACS browser Support and we have a very severe defect on this where it corrupts all the authz rules and no matter how authorization works for an user, it always take you to default policy that is set to deny in majority of the cases. In order to fix the issue do this:
Use supported browser and check whether all policies and its rules and conditions are displayed correctly and resubmit all of them. Restart ACS services to get the latest changes into effect.
~ Jatin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2016 11:00 AM
Hello and thanks for the information.
I am using Mozilla Firefox 43.0.4.
What does resubmiting the policies refers to?
Thanks again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2016 11:07 AM
so basically it messed up all the operators that we use to create conditions with external AD groups. I would like you to review all the authz rules and ensure the and/or operators are still intact. Once done - save changes again. Restart the ACS services from the ACS CLI and test again.
~ Jatin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2016 11:11 AM
Hi;
Basically, I deleted and recreated the AD rules, but still no authorization is being allowed but the default deny rule.
Even the Authorization rule for administering the ACS is being bypassed into the default rule.
Thanks again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2016 11:58 PM
Hi,
We need more details on the issue. For example as i mentioned "Steps" in the Authentication/Authorization reports. The step details you have shared are not useful here.
For specific authorization failure, please click on "Details" icon which will open new window. In the new page, please go to end and there are steps mentioned. please take the screenshot and attach here.
Thanks
Radhakrishna
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2016 05:43 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2016 10:39 PM
Hi fuhresk8,
Could you please configure "AD1:memberOf" instead of "AD1:ExternalGroups" to check whether the authorization is working fine.
We suspect that this is the permission issue to fetch the "TokenGroups" attribute.
Please let us know the results after configuring "AD1:memberOf" attribute.
Thanks,
Priya.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2016 10:48 AM
Hi Priya and thanks for your support;
Did as you mentioned, but same result.
Thanks again.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2016 01:15 AM
Hi,
I've the same problem. On 5.7 there was no problem, see screendump. You see the external groups

On the 5.8, same config & access policies, there is no AD group matching.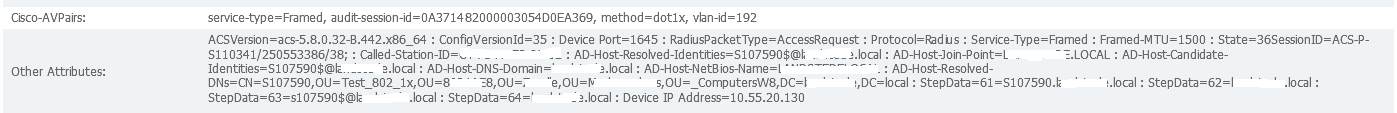
As you see, there are (the same) directory groups, with Group SID. I've checked the SIDs and are correct.

Anybody a hint?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-21-2016 02:17 AM
Hi,
Can any one of you please raise SR, so that DE team can analyze logs and confirm the issue.
OR
please attach the support bundle here.
Thanks
Radhakrishna
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2016 11:36 AM
SR638838907
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2016 09:20 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

