- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Add authentication policy for external clients in ISE TACACS 3.0
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2023 10:42 AM
We have ISE TACACS 3.0 in our company. I am new to administering the environment. We have an external AD environment that clients can authenticate against. In our authentication Policy we have MAB, Dot1X and Default. Would a new policy be added prior to Default to allow clients to authenticate against the external AD environment?
Solved! Go to Solution.
- Labels:
-
Cisco Cafe
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2023 02:01 PM
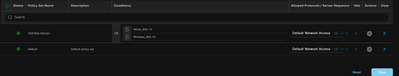
hello @sbartelt62 , within the scenario that you are describing you need to create a policy in which you will be using dot1x , depends mostly on the design you want to do with your policies sets , you can place , as you mention, a policy set above the default one where you might indicate that devices doing this protocol will be hitting the rule , as the following example shows
The rules on ISE are evaluated from top to bottom so the rules that you have above will be evaluated first , you can add multiple more conditions within the rules that adapt to the authentication you want to achieve , or you can also work within the default rule and create a condition that is specific for dot1x within the "Authentication policy" section of that policy set , for ISE 3.0 also you need to have essential licensing to perform RADIUS AAA and web authentication .
Kindly refer to the following links that may help you in this new configuration
Let me know if that helped you .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2023 04:31 AM
Thank you. I will look over all the information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2023 02:01 PM
hello @sbartelt62 , within the scenario that you are describing you need to create a policy in which you will be using dot1x , depends mostly on the design you want to do with your policies sets , you can place , as you mention, a policy set above the default one where you might indicate that devices doing this protocol will be hitting the rule , as the following example shows
The rules on ISE are evaluated from top to bottom so the rules that you have above will be evaluated first , you can add multiple more conditions within the rules that adapt to the authentication you want to achieve , or you can also work within the default rule and create a condition that is specific for dot1x within the "Authentication policy" section of that policy set , for ISE 3.0 also you need to have essential licensing to perform RADIUS AAA and web authentication .
Kindly refer to the following links that may help you in this new configuration
Let me know if that helped you .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2023 04:31 AM
Thank you. I will look over all the information.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide