- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Adding a dedicated PSN for guest to a standalone deployment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Adding a dedicated PSN for guest to a standalone deployment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2020 05:24 AM
I have an existing standalone deployment with 2 ISE nodes each running all personas (PAN, MNT, PSN). We want to add a dedicated PSN to service guest traffic and will sit in the DMZ. It looks adding a dedicated PSN to this deployment type is not supported? Is there documentation which confirms this is not supported?
How can I move from my current deployment to one that will support a single PSN's in the DMZ with minimal VM's? Do I really need to have two ISE nodes running PAN/MnT in internal network, and another two nodes in Internal network as PSN, and 5th node as PSN in DMZ?
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2020 05:53 AM
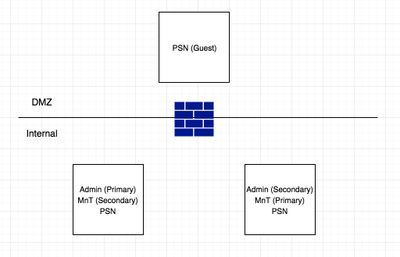
There are only 3 supported models for deployment:
- Stand-alone with redundancy
- Hybrid- PAN and M&T on same nodes with up to 5 PSNs
- Dedicated- PAN on its own nodes, M&T on its own nodes and up to 50 PSNs
It will work to add a guest PSN in your setup but not a supported model. To be supported you would have to add 3 more nodes. Move the PSN functionality inside to dedicated nodes and then your guest PSN.
One alternative that I use frequently now is proxy your guest portal traffic through a DMZ load balancer (F5, Netscaler, etc.). The load balancer can perform the following functions:
- SSL termination so you don't need a public CA cert on your ISE deployment for guest services.
- URL inspection to ensure the guest traffic is only going to the portal.
- Host header inspection to direct the guest traffic to the correct ISE node.
- SSL reencryption with no certificate validation so the ISE deployment can run whatever certificate you want for the guest portal.
- Optionally, you can use the load balancer to securely expose the sponsor portal approval process to the Internet to allow employees to single click approve guests from their mobile phones.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2020 06:51 AM
Hi @paul thanks for your response. This is what I thought, minimum 5 nodes required. It's a big jump from 2 nodes to 5 nodes, especially because this deployment is for less than 100 users. We just wanted to have guest traffic be more secure. At the moment guest traffic is on a separate vnic that sits in the dmz on the internal ISE nodes - looks like that is officially supported and recommended by Cisco. But any concerns for security in this regard?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 04:01 AM
Having the ISE portals running on their own interfaces (in a DMZ) is probably the best thing you can do. You should also make your WLC ACLs as tight as you can by specifying the direction (ingress/egress) and protocol and port numbers - only allow the bare minimum.
If a hacker were to compromise an ISE node, I would suspect they could run a DOS attack on the node and cause it to run slow. But I have never tried that myself. I don't believe that ISE runs the ssh daemon on any interface other than gig0 - so that should be some comfort.
To be frank ... if you have a small shop with some Guest requirement, then spin up a 3rd ISE VM and dedicate that box just for guest. If some hackers plan to annihilate the guest portal then they won't affect your other services. I have implemented this for customers and it's never been an issue with TAC. An ISE node that only runs a guest portal has zero impact on the running system
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide