- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: android 11 can't authentication 802.1X with ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2020 10:14 PM - edited 01-03-2021 03:11 AM
as title,user authentication fail,because android 11 need to fill CA domain
does anyone have some solution?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2021 02:46 PM
Hi
This is not the job of any radius server, because it's a chicken and egg problem. The best you can do is to use a public CA signed certificate in your Radius server (ISE) and apply it to the EAP Role. This will ensure that any EAP supplicant that connects to the network will receive the ISE EAP cert (signed by a public CA) and hopefully (if your client device has all the Root CA certs installed of the most commonly used CAs from factory) then your client device will not have any issues establishing the TLS tunnel. If however your Radius server uses an EAP cert that was signed by a CA that is unknown to your client device, then you will get the security warning. That is by design and it's good.
If your EAP cert was signed by a CA, whose CA Root cert is not known to the client device, then you can try to manually add the CA cert to the client device. How you do that depends on the client device (e.g. MDM, Apple Configurator, etc.)
If you manually put the Radius EAP cert into your client devices (not advised) then you can also achieve that trust - probably only a good idea for a quick and dirty lab test.
It seems to be a common practice these days to get an EAP Server certificate signed by a public CA (like GoDaddy, DigiCert, etc) because that allows devices to connect easily to your Radius server. You should still configure your supplicant to be as secure as possible (e.g. only trust the radius server with a specific FQDN, or if the cert was signed by a specific CA, etc - common options found in the Windows supplicant for example)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2021 01:19 PM
Can you please give a bit more detail?
Are you doing EAP-PEAP on an Android 11 device - and the issue is the ISE EAP certificate?
or
Are you doing EAP-TLS and ISE it not accepting the client certificate that the Android 11 device is supplying to ISE?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2021 03:57 AM
hi sir,
use EAP-GTC on Android 11 device and the CA certificate Field must be filled in,but not needed before,
so authentication fail
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2021 01:31 PM - edited 01-07-2021 01:37 PM
In the past, Android supplicants have never cared about trusting the Authenticating Server (e.g. ISE) - this was seen as a blessing (ease of use) and a curse (bad security for the end user, since you don't know who you're talking to ... could be a rogue Radius server)
So I guess Android 11 is now handling this in a bit more grown up manner.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2021 05:05 AM
Hi Arne Bier,
Is there a solution providing by Cisco for an automatic enrollment of Android devices for server certificate validation? Any recommended on-boarding solution is there to push a local CA public key to client (Android 11) device root certificate store.
If any one have a solution please update .
Regards
Vinay
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2021 02:46 PM
Hi
This is not the job of any radius server, because it's a chicken and egg problem. The best you can do is to use a public CA signed certificate in your Radius server (ISE) and apply it to the EAP Role. This will ensure that any EAP supplicant that connects to the network will receive the ISE EAP cert (signed by a public CA) and hopefully (if your client device has all the Root CA certs installed of the most commonly used CAs from factory) then your client device will not have any issues establishing the TLS tunnel. If however your Radius server uses an EAP cert that was signed by a CA that is unknown to your client device, then you will get the security warning. That is by design and it's good.
If your EAP cert was signed by a CA, whose CA Root cert is not known to the client device, then you can try to manually add the CA cert to the client device. How you do that depends on the client device (e.g. MDM, Apple Configurator, etc.)
If you manually put the Radius EAP cert into your client devices (not advised) then you can also achieve that trust - probably only a good idea for a quick and dirty lab test.
It seems to be a common practice these days to get an EAP Server certificate signed by a public CA (like GoDaddy, DigiCert, etc) because that allows devices to connect easily to your Radius server. You should still configure your supplicant to be as secure as possible (e.g. only trust the radius server with a specific FQDN, or if the cert was signed by a specific CA, etc - common options found in the Windows supplicant for example)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2021 07:07 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2024 05:47 AM
Hello Sir, I have same issue for EAP-PEAP method can you guide please. I am getting disabled message while connecting the SSID.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2024 06:00 AM
disabled.
Also need to have a connection request policy with the user group added
that allows the user to connect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2021 09:36 AM
I had this problem also and it drove me nuts. Here's how I fixed it. FYI Android and iPhone are ok with wildcard certs but Windows 10 no dice. It won't work don't bother. I spent a good portion of 3 days and wildcard certs just don't work with Windows 10.
We have Meraki Wireless Access points and Windows 2016 and 2019 NPS Radius servers but the issue all lies with the NPS server and your certificate.
Our NPS policy is EAP with MSChapv2
EAP was using the self-signed cert which Android no longer accepts.
For demonstration purposes, I'll use fictitious public domain and private domain names.
Public Domain lets say it is jabbathehut.org and private domain or local domain is jabbathehut.int
Solution:
On one of the NPS servers, I installed IIS then opened IIS - Click Server Certificates icon.. far right side clicked Create a Certificate Request. I used jabbathehut.int as the common name. I then went to SSL.com and got a 90day free SSL cert to prove this concept before buying one. I used the CSR or "certificate request" I created on the NPS server mentioned above and created a certificate at ssl.com for jabbathehut.org "which is the email domain name we use publicly" and also what the users will be using to authenticate against the nps servers locally. Yes we added an additional suffix to all users in Active Directory. We added the .org so our servers will authenticate you with either .int or .org. This is done in Active Directory Domains and Trusts. Just right-click AD Domains and Trusts and add whatever suffix you want. Once ssl.com completed the certificate creation I downloaded it to the NPS server where I created the CSR on.
In IIS same place as where I clicked Create CSR I clicked "Complete a CSR" and used the downloaded SSL.com cert I just mentioned. "You may have to change the dropdown to show "all files" so you can choose your downloaded .cer"
I then went into the Network Policy on the NPS server and edited the EAP certificate from the server using self-signed to the ssl.com certificate I just mentioned. I did not need to restart NPS services. Simply click OK and it applies.
Then on the android 11 phone I attempted to connect to the wifi. I entered a user account jabbaminion1@jabbathehut.org as the username and jabbathehut.org as the domain. I set it to EAP and MSChapv2, I set the certificate to "Use system certificate" on Android 10 and on Android 11 I chose any of the available options and entered the user's regular domain password. Viola. It connected straight away.
Once this was proven, I repeated the same steps with our regular goDaddy certificate provider and bought one. Exactly the same steps.
Now since we have 2 NPS servers, I exported the working certificate on the 1st nps server. Easy pz. Just open certificate manager on the nps server that has it. Open the personal store, right click the certificate and chose Export. Say yes to the private key, Set a password on it or it won't work and make it something at least 7 characters long or it may not work. Tick the box Include all certificates in the path if possible.
Now on the other NPS server, same thing. Open the certificate manager, right-click the Personal store and choose Import. Chose your exported cert, "change dropdown to show All files" enter your password and done. Then open that NPS server's network policy or policies that you have and edit the EAP to use the new cert. Now all byod devices should be good to go. iPhones will still prompt you to Trust the certificate. It's just an apple thing.
Now for Windows machines, you need to edit your group policy that it has your trusted certificates and add this new certificate so that all windows domain-joined machines get this cert installed locally. This is done in Group Policy in Computer Configuration - Windows Settings - Security Settings - Public Key Policies / Trusted Root Certification Authorities - Certificates -Add your cert here
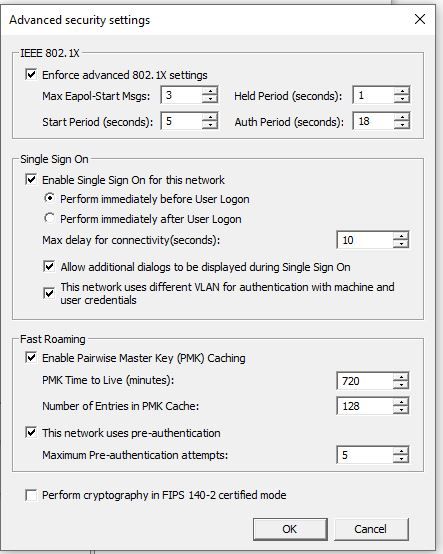
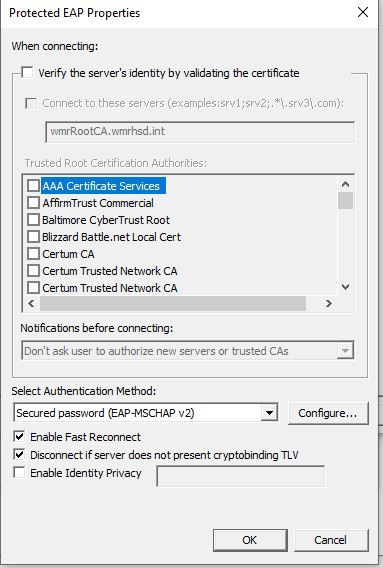
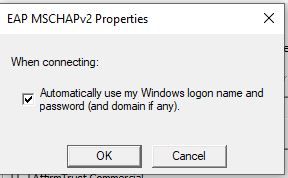
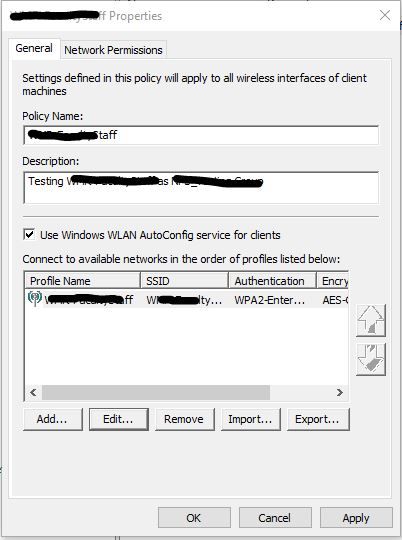
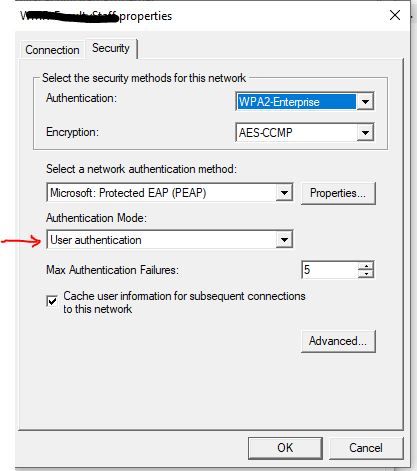
Then if you're doing what we do, we set the Wifi to be at the user's domain login and it connects them to the wifi then logs them into the domain / laptops at the same time. This is done in Group Policy at Computer Configuration - Policies - Windows Settings - Security Settings - Wireless Network 802.11 Policies - Create a new SSID wifi policy here and set the settings to: WPA2-Enterprise - AES-CCMP - Microsoft Protected EAP (PEAP) - User Authentication - (Checkbox Cache user information for subsequent connections = Yes) Advanced section. Single Sign On check box yes to Perform immediately before user logon, allow additional dialogs to be displayed = yes, This network uses different vlan for authenticate = yes | For the Protected EAP properties uncheck the box Verify the server's identity by validating the certificate. (for this to work, yes you need to tell Windows not to validate - counter-intuitive I know but if you don't, Windows still needs to prompt you and confirm that you want to accept this cert and that will break the single sign-on flow. This is why you need Do not validate checked off) For the configure button next to Secure password (EAP-MSChapV2) Click the box to enable Automatically use my Windows logon name and password"
Windows laptops should connect to this wifi and sign into it at the same time. I uploaded some pics of this below to help.
I hope this guide helps someone or many in dealing with the inevitable certificate issue imposed by Android 11 change and save you some grief.
Good Luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2023 11:24 PM
Thanks for your explaining post. I'm in the same situation - just about to order a certificate from well known public CA. Do you remember what were the attributes have did you use for the CSR? I understand you used jabbathehut.org as a Common Name. Did you specify any Subject Alterntive Names or any Key Usage or Extended Key Usage attributes? I'm asking to avoid to pay for a couple of publicly signed certificates before I find a working one.
Thanks in advance for your hint.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide