- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Android Devices unable to download BYOD profile
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2017 07:46 PM
Hi ISE experts
I'm currently facing an issue with the BYOD provisioning for Android devices.
Background: The supplicant policies have already been configured under the authorization policy in ISE. So far, the other devices are provisioning and onboarding without any issue. The Android devices are able to download the Cisco Network Setup Assistant however when trying to download the supplicant profile, an error message stating "Unable to detect Server. Please ensure your network access device is configured to redirect enroll.cisco.com to ISE" On the NSP_GOOGLE_ACL, i have already permitted 72.163.0.0 but still the issue persists.
WLC - 8.0.133
ISE - 2.2 Patch 2
Based on the Android workflow which was published in Using Certificates for Differentiate Access with Cisco Identity Services Engine, the flow stopped as shown in the image below.

When checking the spw.log on the android device, it shows that the gateway is unreachable.
2017.08.29 10:27:16 ERROR:java.net.SocketTimeoutException: failed to connect to /10.8.12.1 (port 80) after 2000ms
2017.08.29 10:27:16 ERROR:failed to connect to /10.8.12.1 (port 80) after 2000ms
2017.08.29 10:27:19 ERROR:DiscoverAsynchTask
2017.08.29 10:27:19 ERROR:java.net.SocketTimeoutException: failed to connect to enroll.cisco.com/72.163.1.80 (port 80) after 2000ms
2017.08.29 10:27:19 ERROR:failed to connect to enroll.cisco.com/72.163.1.80 (port 80) after 2000ms
2017.08.29 10:27:19 ERROR:Unable to discover ISE Server
2017.08.29 10:27:19 INFO:Internal system error.
I would like to know if we are actually suppose to use the NSP-ACL-GOOGLE to download the supplicant profile and certificate.
Somehow if the device is on the CWA Redirection ACL , it's able to download the supplicant profile without any issues.
Has anyone experienced this issue before?
Thanks
Regards
Ryan
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2017 08:16 AM
Ryan, I would suggest removing the ACE permitting traffic to enroll.cisco.com or 72.163.0.0/16 from the NSP_GOOGLE_ACL. I know it sounds counter intuitive, but when it reads 'Please ensure your network access device is configured to redirect enroll.cisco.com to ISE', it is asking you to configure the ACL so the traffic to enroll.cisco.com gets denied by the redirect ACL and gets redirected to the ISE per redirect process on the network device. By removing the line, you are letting the implicit deny take care of it. As you can see that is why the CWA ACL works as it is denying the traffic to the enroll.cisco.com. This is how client application like NSP or AnyConnect posture module finds the correct ISE node.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2017 08:16 AM
Ryan, I would suggest removing the ACE permitting traffic to enroll.cisco.com or 72.163.0.0/16 from the NSP_GOOGLE_ACL. I know it sounds counter intuitive, but when it reads 'Please ensure your network access device is configured to redirect enroll.cisco.com to ISE', it is asking you to configure the ACL so the traffic to enroll.cisco.com gets denied by the redirect ACL and gets redirected to the ISE per redirect process on the network device. By removing the line, you are letting the implicit deny take care of it. As you can see that is why the CWA ACL works as it is denying the traffic to the enroll.cisco.com. This is how client application like NSP or AnyConnect posture module finds the correct ISE node.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2017 07:53 PM
Hi Howon
Thanks for your response. I've tried the following and I was able to obtain the supplicant profile from ISE after that. ![]()
Best regards
Ryan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 02:52 AM
Hi;
I get the same "Unable to detect Server. Please ensure your network access device is configured to redirect enroll.cisco.com to ISE" message. But my ACL on WLC has already denied everything, including traffic to "enroll.cisco.com".
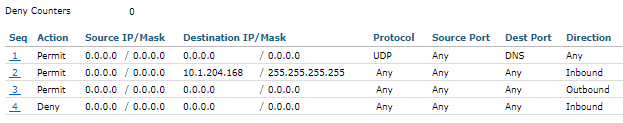
I Also permitted every traffic between that network destined everywhere. So why do I get this message on my Android device?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 06:43 AM
Hello @ciscoworlds - did you ever solve the issue with the Android BYOD onboarding not working?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



