- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: AnyConnect VPN using Smart Card and ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 05:33 AM
I'm preparing for a potential smart card requirement for VPN access and I'm struggling to figure out how it should work.
Currently I have the ASAs sending RADIUS to ISE, which then authenticates against RSA SecurID. ISE is there for the compliance aspect to ensure patches are applied, etc. before the VPN client can connect.
Can smart card be used in this type of scenario? I don't understand what the traffic flow would then be. I know ASA can do smart card authentication and then use LDAP to validate Active Directory group memberships and such, but I'm not sure how this works with ISE in play. Can the ASA still send RADIUS to ISE and ISE use Active Directory as the external identity source? Will that even work with certificates?
Assuming this can work with ISE querying Active Directory, do I have to set it as an Active Directory type, or can it use simple LDAP?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2018 09:10 AM
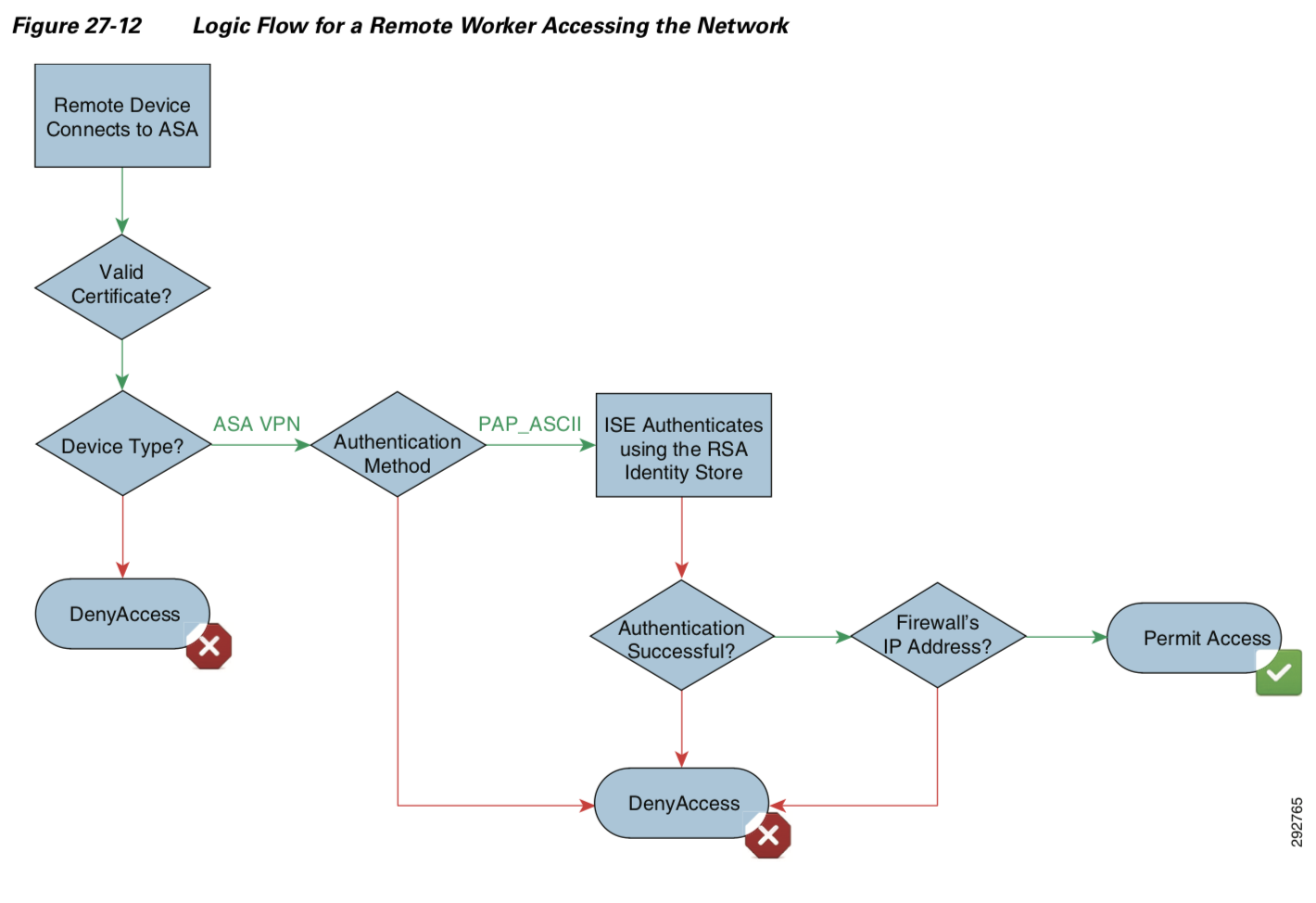
Smart card is usually used for certificate auth. ASA with ISE using user certificate and RSA secure ID for authentication in the link provided by Krish should be helpful to you.
Basically, we would take advantage of multiple authentications available in ASA SSL VPN. It could work without using ISE, but then we lose things like centralized management for the auth policies and reporting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 11:19 AM
2FA on ISE options include Smart card (& RSA SecureID). Please see all the options described in this document.Two Factor Authentication on ISE – 2FA on ISE
- Krish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2018 07:13 AM
I have read this document and found that it doesn't answer my specific questions. Does the flow look like ASA -> RADIUS -> ISE -> LDAP/AD? And can this work with LDAP only and not joining ISE to the Active Directory?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2018 09:10 AM
Smart card is usually used for certificate auth. ASA with ISE using user certificate and RSA secure ID for authentication in the link provided by Krish should be helpful to you.
Basically, we would take advantage of multiple authentications available in ASA SSL VPN. It could work without using ISE, but then we lose things like centralized management for the auth policies and reporting.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2018 12:08 AM
So the ASA MUST perform ONE of the authentications for 2F solution? Or can ISE simply do both 2Fs - AD and THEN prompt the user for RSA token after and ONLY use ASA as proxy here.
In the flow - you're checking certificate on the ASA, what if you like to do AD validation and then RSA token?
The document is referencing Anyconnect 3.x - any new document on this type of integration?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2018 05:28 AM
When it comes to RSA Everything is done through ISE. You configure the RSA server as a token server in the external ID sources.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2018 07:16 AM
Yup - I'm with you on that - I'm just not 100% when you want to do DUAL AD+RSA or even Machine Cert/AD/RSA - what pieces should be done by ASA and what by ISE if it ALL can be done on ISE while user is getting prompted to enter info.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide