- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Authentication Problem Cisco ISE with RSA SecurId Server
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2017 03:05 AM
Hello, everyone,
The following Device Admin Policy rejects access to a test switch:
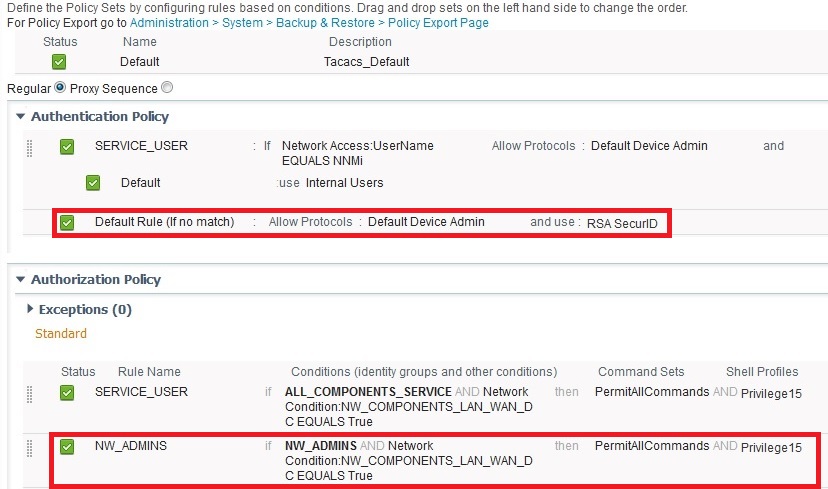
The following error message appears in the TACACS Live LOG:
see : error_msg.pdf
However, this Device Admin Policy works with a request for user data from the Internal User Store.
If you insert the following rule (TEST_RULE) then it also works.
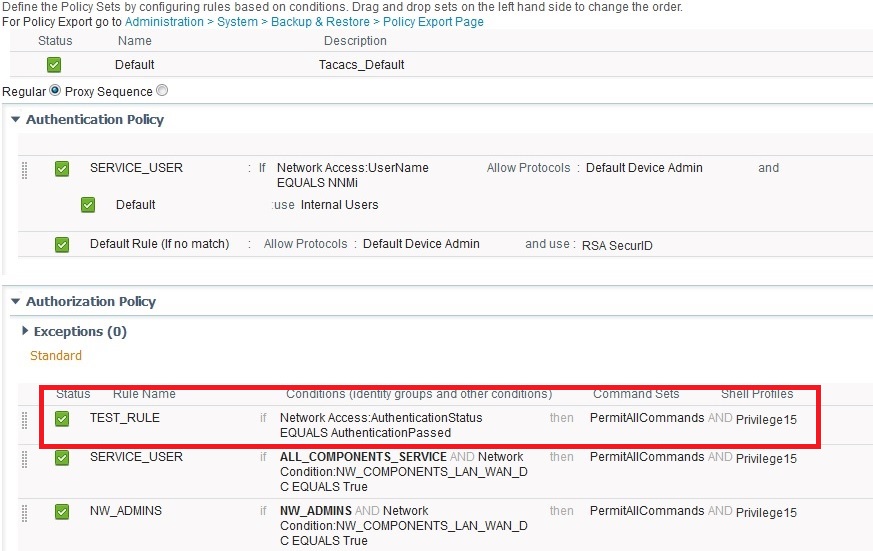
However, as soon as an Identity Group is usually available, the registration fails.
If you query a user name instead of the Identity Group, it works as well.
Does anyone have an idea why the authorization rule in collaboration
does not work with authentication via an RSA server?
Greeting Mario
Note:
The test environment is:
Cisco ISE 2.2.0.470 with Patch 1,2 and 3
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2017 03:55 AM
Hello hslai ,
This condition you suggest works with the RSA server:
InternalUser:IdentityGroup EQUALS "User Identity Groups:Group_Name"
Thanks for your help! ![]()
Greeting Mario
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2017 09:32 AM
In ISE 2.2, you need to create an internal user to use RSA as the password type, if using the internal user group to match. Or, instead of an internal user group, use an other condition as
InternalUser:IdentityGroup EQUALS "User Identity Groups:Group_Name"
(Do not include quotes, but must include the prefix 'User Identity Groups:' in name.)
Later, when you upgrade to ISE 2.3, you may use IdentityGroup:Name. And, ISE 2.3 is currently unable to use InternalUser:IdentityGroup due to CSCvf43341
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2017 01:43 AM
Hello, hslai,
There is the user once Internally on the ISE and with the same user name on the RSA server.
The reason for this is the 2 Factor Authentication, as described here:
https://communities.cisco.com/message/267427#267427
And thank you, this suggestion of yours works; -)
If I change the password type of the internal user to RSA it works also.
Then, however, the 2 Factor Authentication would no longer be
because the 2 passwords (TACACS ENABLE) will then no longer work
is available.
I'll test it with your suggested condition and get back to you.
Thanks for your help.
Greeting Mario
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2017 03:55 AM
Hello hslai ,
This condition you suggest works with the RSA server:
InternalUser:IdentityGroup EQUALS "User Identity Groups:Group_Name"
Thanks for your help! ![]()
Greeting Mario
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2018 07:16 PM
hslai,
I have a similar issue im experiencing with ISE and RSA. Im running ISE 2.3.
I have internal users (identity) and i want to use RSA to authenticate these users. In fact, I have it setup that RSA is used for authentication and if no RSA profile is found it then attempts to use the internal ISE user password for authentication.
My issue is, RSA doesnt seem to be working. The TACACS live logs shows its going out and making a connection with the RSA server, but then comes back and either fails at finding the pass code cache, or doesnt find the user in RSA. Im not sure which is the issue. Ive also noticed a 25K latency which i think might be part of my issue too...
I then found this post
I'm stumped on your comment "Later, when you upgrade to ISE 2.3, you may use IdentityGroup:Name."
I currently have ACS deployed and authenticating with RSA. Im attempting to migrate from ACS to ISE and i have a decent handle on the migration, but i cant seem to get RSA working. Any suggestions or help would be much appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2018 02:44 PM
@mpbaker82: Your issue looks rather different so I do not think the same solution applies.
I would suggest you to focus on the authentication requests to the RSA SecurID server and ensure it returning Access-Accept. In a troubleshooting session with a partner, I remembered him using a RSA admin interface similar to ISE RADIUS livelog to search and get the details on authentications. This RSA doc might be of interest to you -- 000028896 - Troubleshooting RSA Authentication ... | RSA Link
In case you are still stuck, please engage Cisco TAC support and RSA support.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide