- Cisco Community
- Technology and Support
- Security
- Network Access Control
- authorization policy based on Machine cert,(SAN Value) and Also User Authentication with Any connect...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 10:13 AM
authorization policy based on Machine cert,(SAN Value) and Also User Authentication with Any connect NAM Module ?
As Machine Authentications with always happen first, and then User Authentication, can we authorize policies based on machine Cert ? and also wants to do user Authentication ?
we will have two Type of machine Cert Differentiated with SAN Valve and single AD Group, and we want to authorize based on Machine cert(SAN Valve) and also user authentication, is this Possible ? if yes , how it will work ?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 02:33 PM
Please start with this guide -- How To: Deploy EAP Chaining with AnyConnect NAM and ISE
And, try it out in your lab. I have no existing setup for EAP Chaining so it would take me some time to do it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
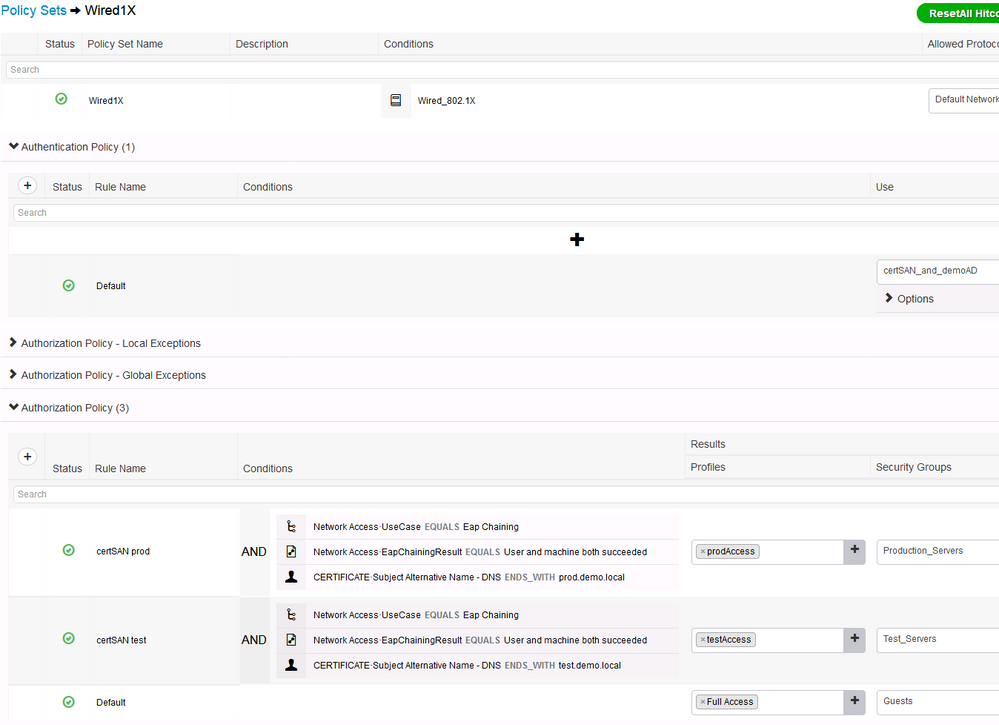
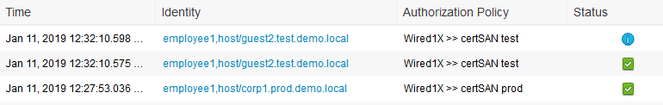
01-10-2019 03:00 PM - edited 01-11-2019 05:31 AM
I am not in the community support duty this week so I am not monitoring the forum.
Assuming you meant the Windows computers have a DNS entry in the certificate SAN field, such as
corp1.prod.demo.local or guest2.test.demo.local
And, the users authenticate via password.
Below is a sample policy set and results.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2018 02:33 PM
Please start with this guide -- How To: Deploy EAP Chaining with AnyConnect NAM and ISE
And, try it out in your lab. I have no existing setup for EAP Chaining so it would take me some time to do it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2018 11:53 AM
i dont have home lab set up for This, can you Please check from your Cisco Colleges ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2018 01:39 PM
So, we didn't do this exact thing, but we did try EAP Chaining to verify the system was domian joined, and the user was authenticated.We ran into issues with the NAM module and ended up scrapping it due to the issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2018 03:57 PM
Please give a good example how you would like ISE authorization rule to match on the SAN value of a machine certificate to differentiate two different types of certificates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2019 07:31 AM
we have 2 different type of Cert based on SAN Valve.
1- Prod.xyz.com
2-Test.XYZ.com
and one AD domain group. so we want that if end user has 'Prod.xyz.com' cert and valid ad cerdential, it should have Access to Prod envirement only.
and if end user has 'Test.xyz.com' cert and valid ad cerdential, it should have Access to Test envirement only.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2019 01:49 PM
From what i can see the only way to do that would be EAP chaining, other wise perhaps rely on supplicant to do machine cert plus sending to portal for CWA chaining? @hslai any other ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2019 03:00 PM - edited 01-11-2019 05:31 AM
I am not in the community support duty this week so I am not monitoring the forum.
Assuming you meant the Windows computers have a DNS entry in the certificate SAN field, such as
corp1.prod.demo.local or guest2.test.demo.local
And, the users authenticate via password.
Below is a sample policy set and results.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide