- Cisco Community
- Technology and Support
- Security
- Network Access Control
- BYOD Network Setup Assistant Failed to discover ISE Reconnect...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
BYOD Network Setup Assistant Failed to discover ISE Reconnect...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2023 09:52 PM - edited 08-01-2023 10:18 PM
I have a problem in BYOD when "Network Setup Assistant" run on Wired_802.1x Windows 10 Client, I got the error message "Failed to discover ISE Reconnect to network and try again", after troubleshooting and searching for the cause of the problem, I found in spwProfileLog file that it discovering ISE using a default gateway, how do I prevent or change it so that it doesn't use the default gateway for discovering ISE
you will find below the spwProfileLog file and attached snapshot of the error message
[Wed Aug 02 03:45:54 2023] Logging started
[Wed Aug 02 03:45:54 2023] SPW Version: 3.0.0.3
[Wed Aug 02 03:45:54 2023] System locale is [en]
[Wed Aug 02 03:45:54 2023] Loading messages for english...
[Wed Aug 02 03:45:54 2023] Initializing profile
[Wed Aug 02 03:45:55 2023] Found 1 interfaces
[Wed Aug 02 03:45:56 2023] Found 0 interfaces
[Wed Aug 02 03:45:56 2023] SPW is running as High integrity Process - 12288
[Wed Aug 02 03:45:56 2023] GetProfilePath: searched path = C:\Users\user\AppData\Local\Temp\ for file name = spwProfile.xml result: 0
[Wed Aug 02 03:45:56 2023] GetProfilePath: searched path = C:\Users\user\AppData\Local\Temp\Low for file name = spwProfile.xml result: 0
[Wed Aug 02 03:45:59 2023] Profile xml not found Downloading profile configuration...
[Wed Aug 02 03:45:59 2023] Downloading profile configuration...
[Wed Aug 02 03:45:59 2023] Discovering ISE using default gateway
[Wed Aug 02 03:46:00 2023] Identifying wired and wireless network interfaces, total active interfaces: 1
[Wed Aug 02 03:46:00 2023] Network interface - mac:50-00-00-04-00-00, name: Ethernet, type: unknown
[Wed Aug 02 03:46:00 2023] Identified default gateway: 192.168.0.1
[Wed Aug 02 03:46:00 2023] Identified default gateway: 192.168.0.1, mac address: 50-00-00-04-00-00
[Wed Aug 02 03:46:00 2023] DiscoverISE - start
[Wed Aug 02 03:46:00 2023] DiscoverISE input parameter : strUrl [http://192.168.0.1/auth/discovery]
[Wed Aug 02 03:46:00 2023] [HTTPConnection] CrackUrl: host = 192.168.0.1, path = /auth/discovery, user = , port = 80, scheme = 3, flags = 0
[Wed Aug 02 03:46:00 2023] [HTTPConnection] HttpSendRequest: header = Accept: */*
headerLength = 12 data = dataLength = 0
[Wed Aug 02 03:46:00 2023] HTTP Response header: [HTTP/1.1 404 Not Found
Date: Thu, 01 Jan 1970 00:00:00 GMT
Server: webserver
Connection: close
X-Download-Options: noopen
X-Frame-Options: deny
X-XSS-Protection: 1; mode=block
Strict-Transport-Security: max-age=31536000; includeSubdomains
Content-Length: 0
Cache-Control: no-cache
Content-Type: text/html
] HTTP Content: []
[Wed Aug 02 03:46:00 2023] DiscoverISE - server sent an unsupportted response.
[Wed Aug 02 03:46:00 2023] DiscoverISE - end
[Wed Aug 02 03:46:00 2023] DiscoverISE - start
[Wed Aug 02 03:46:00 2023] DiscoverISE input parameter : strUrl [http://enroll.cisco.com/auth/discovery/]
[Wed Aug 02 03:46:00 2023] [HTTPConnection] CrackUrl: host = enroll.cisco.com, path = /auth/discovery/, user = , port = 80, scheme = 3, flags = 0
[Wed Aug 02 03:46:00 2023] [HTTPConnection] HttpSendRequest: header = Accept: */*
headerLength = 12 data = dataLength = 0
[Wed Aug 02 03:46:22 2023] Warning - [HTTPConnection:RetrySendRequest] InternetOpen() failed with code: [12029], msg: [A connection with the server could not be established
]
[Wed Aug 02 03:46:22 2023] Exiting with RetrySendRequest value = 0
[Wed Aug 02 03:46:22 2023]
[Wed Aug 02 03:46:22 2023] DiscoverISE - end
[Wed Aug 02 03:46:22 2023] DiscoverISE - start
[Wed Aug 02 03:46:22 2023] DiscoverISE input parameter : strUrl [http://1.1.1.1/auth/discovery/]
[Wed Aug 02 03:46:22 2023] [HTTPConnection] CrackUrl: host = 1.1.1.1, path = /auth/discovery/, user = , port = 80, scheme = 3, flags = 0
[Wed Aug 02 03:46:22 2023] [HTTPConnection] HttpSendRequest: header = Accept: */*
headerLength = 12 data = dataLength = 0
[Wed Aug 02 03:46:22 2023] HTTP Response header: [HTTP/1.1 301 Moved Permanently
Server: cloudflare
Date: Wed, 02 Aug 2023 03:46:22 GMT
Content-Type: text/html
Content-Length: 167
Connection: keep-alive
Location: https://1.1.1.1/auth/discovery/
CF-RAY: 7f03555b78bcbacd-MXP
] HTTP Content: [<html>
<head><title>301 Moved Permanently</title></head>
<body>
<center><h1>301 Moved Permanently</h1></center>
<hr><center>cloudflare</center>
</body>
</html>
]
[Wed Aug 02 03:46:22 2023] Discover ise - failed to parse ise server. Response: [https://1.1.1.1/auth/discovery/]
[Wed Aug 02 03:46:22 2023] DiscoverISE - end
Regards
Omran Mohamed
- Labels:
-
AAA
-
BYOD
-
Identity Services Engine (ISE)
-
Wired
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2023 02:10 PM
What is the layer 3 setup you're using? Is the client on a different VLAN to that of ISE? If so, then how else do you expect the client to reach ISE? Does the client get an IP address, and can it ping ISE from the command line? Is there an ACL on the session preventing the client from reaching ISE portal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2023 03:03 PM
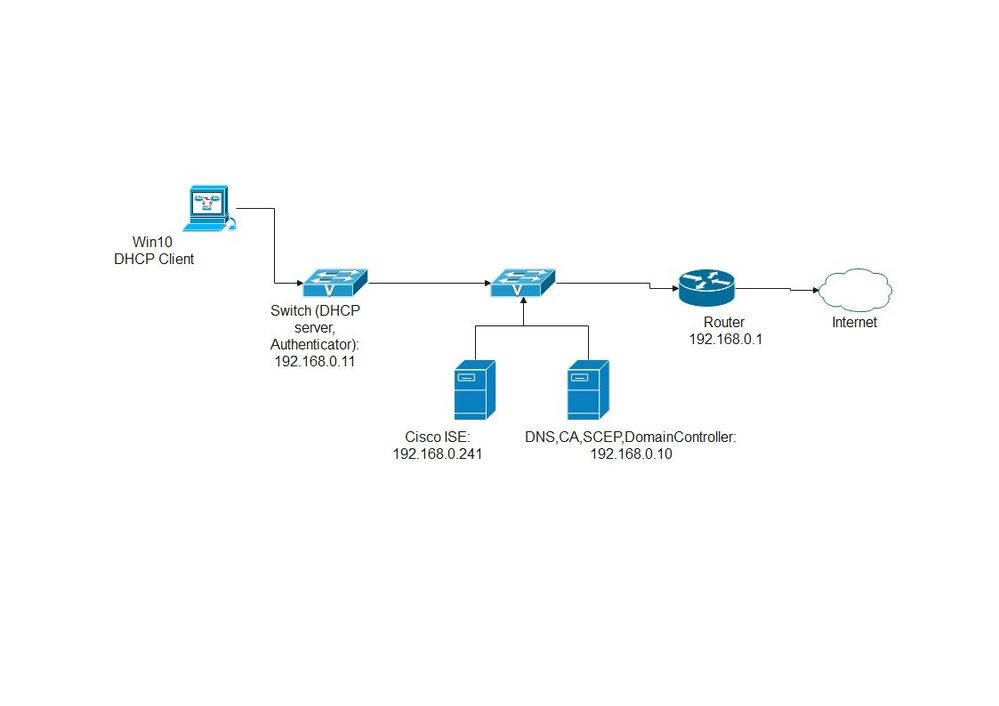
I'm doing only Layer 2 in untagged traffic, all Cisco ISE, Client PC Win10, WinServer2016 (running DNS, CA, SCEP RA, Active Directory), and the Switch in the same subnet 192.168.0.0/24,
For testing, I made the ACL to permit all traffic, and all nodes have ping reachability
permit ip any any
the main issue is that Network Setup Assistant trying to discover ISE using the default gateway (Router)
DiscoverISE input parameter: strUrl [http://192.168.0.1/auth/discovery]
check the topology
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2023 03:25 PM - edited 08-02-2023 03:26 PM
The http request by the client is just a simple trigger that should cause the switch to perform http interception, and re-directing the client to the ISE URL. This happens via ACLs on the switch. If I recall, with IOS switches the redirect logic is a bit counter intuitive - the goal is to tell the switch WHAT to redirect - and the WHAT traffic is a permit, and the rest is deny - but the counter intuitive logic is that you deny stuff that the client is allowed to send (e.g. DNS requests and access to the ISE portal).
When you open the port for this client, ISE must download an ACL that contains a reject for all the client traffic (DNS and ISE portal) and then permit for tcp/80 (http). And the switch must also have the command "ip server http" to allow the http interception to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2023 04:27 PM - edited 08-02-2023 04:34 PM
regarding redirection by the Switch, the client was actually directed to the Cisco ISE BYOD Portal and was able to access the web page and download the Network Setup Assistant.exe smoothly, also I tried to use Wireshark to analyze the packets but when the Network Setup Assistant starts no packets are flow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2024 10:49 PM
We are experiencing a very similar issue. How did you resolve it? Thank you for any feedback.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide