- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Can't Connect to Endpoint when user logs off
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 09:21 AM
We are in the process of deploying ISE 2.6 Patch 3 and are using Cisco AnyConnect Network Access Manager for EAP Chaining. We have ran into a a situation where whenever no user is logged into the machine it becomes unreachable (no ping, VNC, etc.). I have attached screenshots of our NAM configuration from the AnyConnect Profile Editor. Are there additional settings in ISE that could be causing this behavior? We currently have a rule in our Policy in ISE that is Temp Roll Out rule that basically allows anything that is profiled as a Workstation, etc. to connect. I have a TAC case open as well but they aren't being very responsive.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
-
Wired
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 10:56 AM
Can you share that interface config as well please
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 09:40 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 09:58 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 10:07 AM
Hi,
The required three authorisation policies seem to be in place. Ensure that the configuration is correct though, following this guide. When only the machine is authenticated, what is the status on ISE (what is the currently pushed policy) and on the switch "show authentication session" for the interface.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 10:22 AM
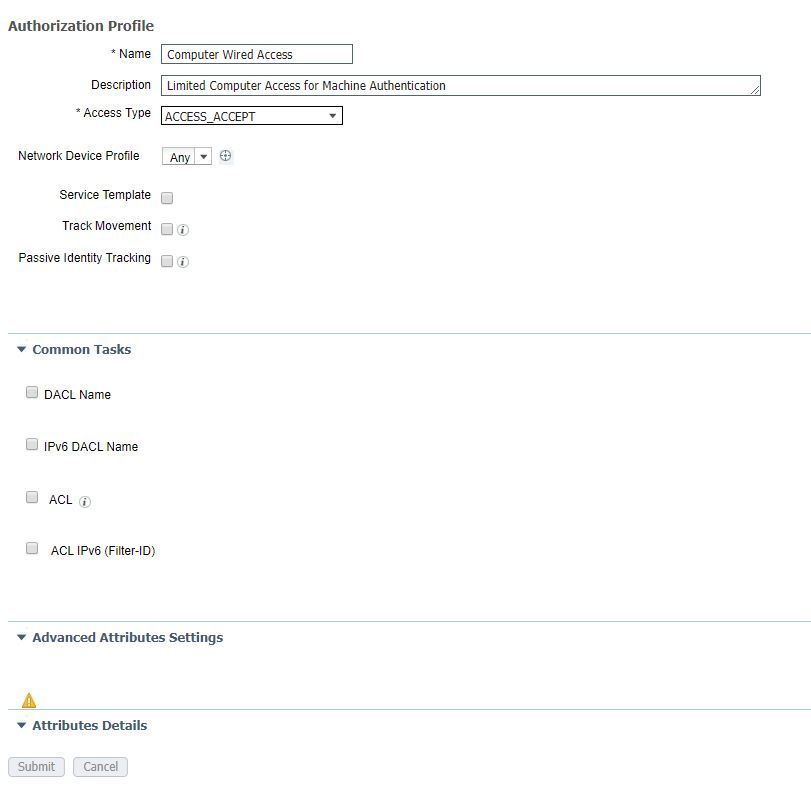
Authz policy is configured as expected (right). Can you share what is configured in this authz profile (Computer Wired Access)? It looks like you have a few hundred hits on that authz policy. As @Cristian Matei mentioned see what the switch is showing for auth detail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 10:27 AM
I can't seem to find the Computer Wired Access auth profile to be able to check the configuration. I'll be glad to provide some screenshots but I seem to only be able to find it listed in the Policy Set
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 10:36 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 10:44 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 10:45 AM
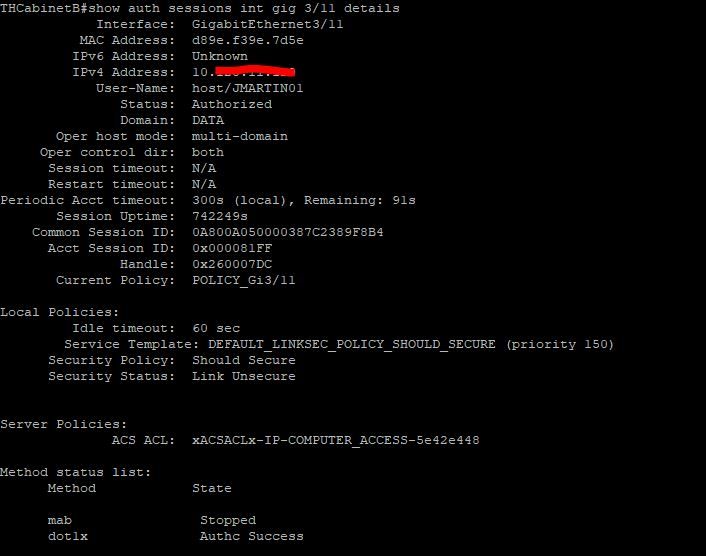
This is what the switch port shows: sh auth sessions | i Gi3/11
Gi3/11 d89e.f39e.7d5e dot1x DATA Auth 0A800A050000387C2389F8B4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 10:50 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 10:52 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 10:56 AM
Can you share that interface config as well please
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 10:58 AM
switchport access vlan 11
switchport mode access
switchport voice vlan 64
switchport port-security maximum 5
authentication event server dead action authorize vlan 254
authentication event server dead action authorize voice
authentication event server alive action reinitialize
authentication host-mode multi-domain
authentication open
authentication order mab dot1x
authentication priority dot1x mab
authentication port-control auto
authentication timer reauthenticate server
authentication timer inactivity 60
authentication violation restrict
mab
snmp trap mac-notification change added
snmp trap mac-notification change removed
auto qos voip cisco-phone
dot1x pae authenticator
dot1x timeout tx-period 10
qos trust device cisco-phone
spanning-tree portfast edge
spanning-tree bpduguard enable
service-policy input AutoQos-4.0-Cisco-Phone-Input-Policy
service-policy output AutoQos-4.0-Output-Policy
ip dhcp snooping trust
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 11:02 AM
permit udp any eq 68 any eq 67
permit udp any any eq 53
permit ip any host <DNS SERVER IP>
permit ip any host <DC IP>
deny ip any any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 11:11 AM
I would take a peek at an admin guide: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_8021x/configuration/xe-3se/3650/sec-user-8021x-xe-3se-3650-book/sec-ieee-open-auth.html#GUID-65E5A890-B7C0-43AC-976D-D76BF6135085
Also, for future reference I recommend starting with less configs, get it working, then slowly add things back. May help with identifying root cause. Check out labminutes.com/sec as well for free config tutorials. HTH!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide