- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Check logs on Cisco ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Check logs on Cisco ISE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 04:12 AM
Hi all and sorry if this question has been already asked.
In a new environment I'm working at the moment I would like to check on Cisco ISE some logs for RADIUS authentication, authorization for EAP-PEAP authentication (not Live RADIUS Logs).
The problem is that in the GUI (2.0.0.306, I know very old!) I see many places where to configure logs or syslog servers but no way to look at them though the Cisco ISE itself is configured to retain the logs for one day.
Another weird setting I saw is that the Cisco ISE cluster is configured to send logs (type UDP SysLog [non standard port], TCP SysLog [non standard port] and SysLog [non standard port]) to each of the units like the Cisco ISE was a syslog server.
Is there anyone who may give some hints? Once I identify the meaningful logs for the EAP-PEAP (by the way it's related to govroam a sibling of eduroam) by tuning the log level I will forward them to the proper syslog servers.
Thanks a lot in advance,
Alex
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 09:20 AM - edited 05-14-2019 09:21 AM
Please note that ISE Live logs is the best way to check authentication issues.
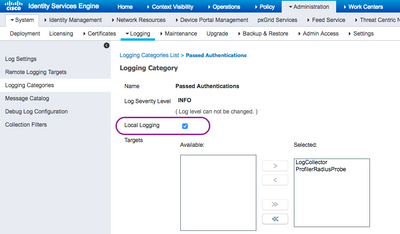
ISE has local logging although it disabled by default for Passed Authentications. We may go to ISE Admin Web UI > Administration > System > Logging > Logging Categories. Select Passed Authentications and put a check mark on [ V ] Local Logging.
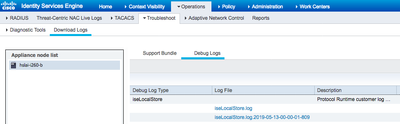
Then, we may either download the file(s) at ISE Admin WebUI > Operations > Troubleshoot > Download Logs > [ISE node name] > Debug logs.
Or, use ISE Admin CLI to tail on it.
myISE/admin# terminal length 0 myISE/admin# show logging application localStore/iseLocalStore.log tail ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 09:20 AM
ISE has local logging although it disabled by default for Passed Authentications. We may go to ISE Admin Web UI > Administration > System > Logging > Logging Categories. Select Passed Authentications and put a check mark on [ V ] Local Logging.
Then, we may either download the file(s) at ISE Admin WebUI > Operations > Troubleshoot > Download Logs > [ISE node name] > Debug logs.
Or, use ISE Admin CLI to tail on it.
myISE/admin# terminal length 0 myISE/admin# show logging application localStore/iseLocalStore.log tail ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2019 07:36 PM
In my view, the Operational Reports are the only method that you can use in ISE to view historical data. Live Logs is great, but it's limited to the last 24 hours and last 100 rows. Use the Reports to go back in time.
As for SYSLOGs - I find this is a challenging topic because first of all you often end up guessing which category to enable to get the data you want (Cisco documentation needs to be improved) and at which logging level to enable it to give just enough visibility. But once that is done, you need a decent SIEM like Splunk or Graylog (or whatever) to crunch the data. This is not a job for ISE.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide