- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Check Point Identity Collector integration with Cisco ISE 2.4 PxGrid
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Check Point Identity Collector integration with Cisco ISE 2.4 PxGrid
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2020 05:09 AM
Hi,
I have a distributed ISE deployment with 2 PAN (PxGrid enabled) nodes, 2 MNT and 5 PSNs. I have integrated Check Point Identity Collector with ISE PxGrid Node. While integrating I exported Internal CA certificate from 'Primary PxGrid Node' which was used along with Root Certificate (domain) to generate 'Server certificate' in .jks format.
My concern is, what if the 'Primary PxGrd Node' breaks ? Will the Identity Collector still be ale to communicate with 'Secondary PxGrid Node'? Note that I used internal CA cert of Primary PxGrid Node to generate Server Certificate which was used while integrating Check Point Identity Collector.
Regards,
N
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2020 11:42 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2020 11:47 PM
This is probably something you need to confirm with Checkpoint as their whitepaper does not address distributed deployments.
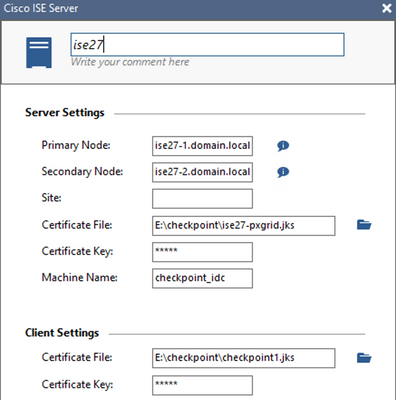
The IDC version I have in my lab (version R80.10) does have an optional 'Secondary Node' setting (see the below screenshot) in the ISE Server Settings configuration. It's unclear, however, if the IDC will automatically trust the certificate trust chain in the JKS certificate file or if it only trusts the identity certificate.
Each ISE node has pxGrid certificate so, if it is the latter, there might be two options (again, this would need to be confirmed by Checkpoint for their validated design and best practice).
- Add the two pxGrid nodes into the IDC as separate ISE servers using their own individual certificates. Add both ISE servers to your Query Pool.
- Ensure you have both pxGrid node FQDNs in the SAN for your pxGrid cert on the Primary node. Export that pxGrid certificate with the private key and import it into the Secondary node for the pxGrid usage. This would ensure that both nodes use the same identity certificate. You would then use this certificate in IDC with a single ISE server that has the Primary and Secondary nodes defined.
Note that the integration with IDC uses pxGrid version 1, which I believe only functions in an Active/Standby capacity. If you validate with Checkpoint and/or test this scenario, please update this post for others that might be looking at this integration.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide