- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Cisco ISE 2.X version and External Identity Source As Cloud Azure AD ? Will it support
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 03:34 AM - edited 02-21-2020 11:09 AM
Hi Team, Please let me is there any document: Integrate Cisco ISE with Micosoft Azure(Cloud) server for 802.1x authetication/ like AD groups etc . is there any alternative method we can use Azure Ad for Authentication of users? Does Cisco ISE support this ? or not - Please confirm
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 04:28 AM
Put that one on your "Dear Santa", Christmas list for Cisco :-) The short answer is 'no'. Azure cannot be an external identity source. ISE expects to join a real domain controller.
In my own experience I have used Azure AD Connector on our on-premise Microsoft Server to allow us to sync our employee's AD credentials with Office365/Azure. It works really well - but this stuff is not even native in Windows Server 2012 for example. You have to download an agent to link these two worlds together. But it doesn't help your cause because ISE can't talk to Azure directly - maybe if we could install "plug-ins" into ISE to add these features, then my analogy might make some sense.
Have you had a look at secure LDAP to Azure AD instead? ISE supports Secure LDAP - that might be the answer:
https://docs.microsoft.com/en-us/azure/active-directory-domain-services/tutorial-configure-ldaps
You get the same benefits with LDAP as you would by joining ISE to AD. Setting up LDAP in ISE can be a bit painful at first, but it's perfectly good for user/machine authentication.
let us know how you get on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 09:55 PM - edited 09-05-2019 09:56 PM
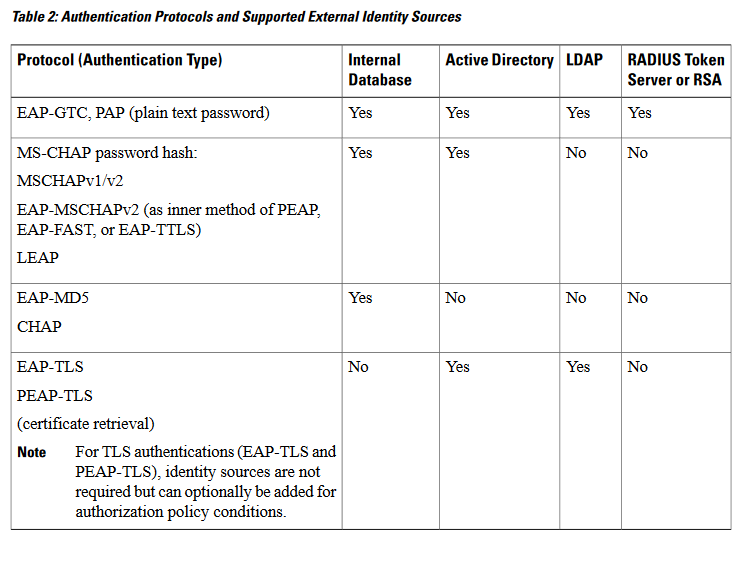
I was just reminded of the limitations of LDAP as an external identity source. It has limitations based on the inner EAP method due to how passwords are handled.
So, e.g. EAP-PEAP (using MS-CHAPv2) and LDAP is not a workable combination.
If you have simpler forms of auth like PAP, then LDAP is fine.
So I take back what I said earlier about LDAP being equivalent to AD - it's not ideal at all when doing advanced Password (challenged/hash) operations (as used in CHAP/MSCHAP etc) and all the others shown below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 04:28 AM
Put that one on your "Dear Santa", Christmas list for Cisco :-) The short answer is 'no'. Azure cannot be an external identity source. ISE expects to join a real domain controller.
In my own experience I have used Azure AD Connector on our on-premise Microsoft Server to allow us to sync our employee's AD credentials with Office365/Azure. It works really well - but this stuff is not even native in Windows Server 2012 for example. You have to download an agent to link these two worlds together. But it doesn't help your cause because ISE can't talk to Azure directly - maybe if we could install "plug-ins" into ISE to add these features, then my analogy might make some sense.
Have you had a look at secure LDAP to Azure AD instead? ISE supports Secure LDAP - that might be the answer:
https://docs.microsoft.com/en-us/azure/active-directory-domain-services/tutorial-configure-ldaps
You get the same benefits with LDAP as you would by joining ISE to AD. Setting up LDAP in ISE can be a bit painful at first, but it's perfectly good for user/machine authentication.
let us know how you get on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 03:17 PM
Hi @Arne Bier ,
Thank you , i will review Secure LDAP option,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 09:55 PM - edited 09-05-2019 09:56 PM
I was just reminded of the limitations of LDAP as an external identity source. It has limitations based on the inner EAP method due to how passwords are handled.
So, e.g. EAP-PEAP (using MS-CHAPv2) and LDAP is not a workable combination.
If you have simpler forms of auth like PAP, then LDAP is fine.
So I take back what I said earlier about LDAP being equivalent to AD - it's not ideal at all when doing advanced Password (challenged/hash) operations (as used in CHAP/MSCHAP etc) and all the others shown below:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide