- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2022 05:43 AM
Hi,
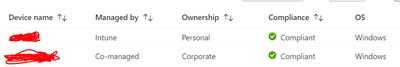
We wanted to use MDM (MS Intune) Attributes to build authorization policy and permit access to network only for the corporate assets.
As per the "Cisco Identity Services Engine Administrator Guide, Release 3.1" We see that the following attributes are configurable on ISE 3.1
Refer (Table 15. MDM Attributes and Values)
DaysSinceLastCheckin
Supported from MDM API Version 3
DeviceCompliantStatus
DeviceRegisterStatus
DiskEncryptionStatus
IMEI
JailBrokenStatus
MDMFailureReason
MDMServerName
MDMServerReachable
MEID
Manufacturer
Model
OsVersion
PhoneNumber
PinLockStatus
SerialNumber
ServerType
UDID
UserNotified
GUID
Supported from MDM API Version 3
Macaddresses
Supported from MDM API Version 3
However, in the Intune we have allowed to enroll both corporate and personal devices.
Question: Is there way to write a custom attribute in ISE 3.1 to pull the information of "Ownership" detail from Intune?. If so, then we can create a authorization policy in the ISE 3.1 to permit access to network for the corporate assets only.
Please give me some direction on this.
Regards,
Puru
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2022 03:24 PM
Roadmap is not discussed on this public forum. Any updates to the MDM API would require moderate development effort not only from Cisco but from all 3rd party vendors that use the API. The API is generic across multiple vendors, so I'm not that updates specific to one vendor (Microsoft, in this case) would be likely.
You can use the Make A Wish form to provide feedback and suggest feature enhancements.
You should also be aware of this field notice. If you intend to continue using the Intune MDM check, you will need to move to certificate-based authentication to use the GUID for MDM lookups.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2022 03:31 PM
No, the Ownership attribute is not communicated via the MDM API so ISE cannot use it as a policy condition.
If your Corporate Windows 10+ endpoints are Hybrid AD Joined, the best option I can think of would be to use TEAP(EAP-TLS) with EAP Chaining on those endpoints and leverage the Network Access·EapChainingResult EQUALS User and Machine both succeeded condition in your AuthZ Policy to only permit corporate users on corporate machines.
If you're not familiar with TEAP, see EAP Chaining with TEAP.
I also discuss the usage and flow of TEAP in my ISE Integration with Intune MDM Webinar.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2022 11:45 PM
Hi Greg Gibbs,
Thank you so much for your quick response.
Whether MDM API "Ownership attribute" will be added in the future enhancement?
We are currently using EAP-FAST (Cisco AnyConnect) for EAP Channing. However, we are seeing few administrative challenges as we are migrating the services from ISE 2.2(EOL) to new platform ISE 3.1
Current platform (ISE 2.2) is using different intermediate certificate for Machine authentication.
We had to use new intermediate certificate on the ISE 3.1 as the old one is going to expire soon. This requires a mass client certificate rollout. Also, on the other hand we have time constraint as the new ISE is using Temporary licenses.
Hence, we thought to use MDM-MS Intune to authorize and permit the connection. By doing we can use PEAP (MS-CHAPV2) and get rid from certificate-based authentication/authorization.
However, the current attributes do not meet our requirement. So, thought to check in the community.
Please share if you know any news about adding the ownership attribute in the future release. Also, how would I place a request to Cisco on this requirement?
Appreciate your help.
Thank you.
Regards,
Puru
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2022 03:24 PM
Roadmap is not discussed on this public forum. Any updates to the MDM API would require moderate development effort not only from Cisco but from all 3rd party vendors that use the API. The API is generic across multiple vendors, so I'm not that updates specific to one vendor (Microsoft, in this case) would be likely.
You can use the Make A Wish form to provide feedback and suggest feature enhancements.
You should also be aware of this field notice. If you intend to continue using the Intune MDM check, you will need to move to certificate-based authentication to use the GUID for MDM lookups.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-16-2022 04:57 AM
Hi Greg Gibbs,
I understand, Thank you very much for the details. It is a great help!
Looks, the client certificate need to stay anyways as per the field notice.
Thank you.
Regards,
Puru