- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Cisco ISE 3.2 Secure Wired Access with Catalyst 1000 Series Switches
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2023 11:51 PM
Hi, community,
we are trying to do PoC with the following requirement and environment
Requirement/PoC Success Criteria
- Port-based Authentication using IEEE 802.1X
- Posture assessment and remediation of Windows 10 endpoint using AnyConnect
- If the machine is non-compliant then the machine should not get any access except remediation resources like the WSUS server, and AV Server to remediate noncompliant conditions
- If the machine is compliant then the machine should get normal access,
- if the machine posture status is unknown then redirect it to the client provisioning portal to download AnyConnect Agent
Environment for PoC
- Cisco Identity Services Engine (ISE) Release 3.2
- End user machine - Windows 10
- User Access Switch - Catalyst 1000 Series Switch C1000-8T-E-2G-L with IOS Release 15.2.7E7
- No DHCP in the environment.
- Endpoint Patch Management Solution - Windows Server Update Services (WSUS)
- Endpoint AV Solution - eScan
Challenge for PoC
- Since there is no DHCP how can I create an Authorization profile to quarantine the machine ?
- If I try to achieve Authorization using dACL but then I came to know from IOS Release 15.2.7E7 Guide that dynamic ACL are not supported
Can anyone guide me on how can I proceed for Cisco ISE PoC with the above-mentioned requirement of PoC?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 06:35 PM
As per the Security Configuration Guide for the Cat1000, it does support downloadable per-user ACLs. There are very specific limitations with this platform that are also described, including this important one:
"Only one 802.1X-authenticated user is supported on a port. If the multiple-hosts mode is enabled on the port, the per-user ACL attribute is disabled for the associated port."
The configuration required for the dACLs, however, relies on the 'ip device tracking' feature. The IP Source Guard section of the configuration guide states the following, so applying a per-user dACL (1 user per port) should work as long as you have 'ip device tracking' enabled and the host initiates some traffic on the network when connected.
"IP or MAC bindings are learned from static hosts by ARP and IP packets. They are stored in the device tracking database."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 09:05 PM
Hi Greg,
Thanks for sharing the link where it says support for "• IEEE 802.1x authentication with downloadable ACLs and redirect URLs to allow per-user ACL downloads from a RADIUS server or Cisco Identity Services Engine (ISE) to an authenticated switch."
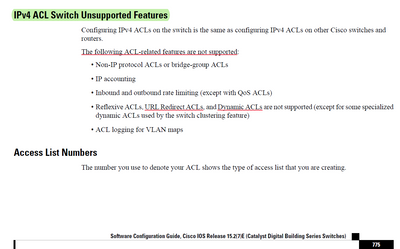
I was referring Software Configuration Guide, Cisco IOS Release 15.2(7)E (Catalyst Digital Building Series Switches) where under IPv4 ACL Switch Unsupported Features topic it is mentioned that
Reflexive ACLs, URL Redirect ACLs, and Dynamic ACLs are not supported (except for some specialized dynamic ACLs used by the switch clustering feature)
Just look at the screenshot that i was referring.
Not sure which document i should refer to check the support of dACL for Catalyst 1000 Series Switches C1000-8T-E-2G-L with IOS Release 15.2.7E7
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 11:46 PM
Downloadable ACLs are not the same thing as Dynamic ACLs (also known as "Lock-and-Key" ACLs). These serve completely different functions.
See the following document for an example of Dynamic ACLs.
https://www.cisco.com/c/en/us/support/docs/security-vpn/lock-key/7604-13.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2023 12:36 AM
Hi Greg,
Thanks for correcting my understanding of Downloadable ACLs and Dynamic ACLs.
Really appreciate your efforts in the Cisco community.
I will update PoC result
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 12:54 PM
You can do Posture without DHCP. Are dACLs not supported on Catalyst 1000s?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 01:06 PM
If you can't do dACL, you could try to define an ACL on the switch, and then refer to that ACL by name as part of the Access-Accept. Not sure which RADIUS Attribute that is exactly, but it might be the Filter-ID attribute, or a Cisco AVPair. If this works, then great but, it's an extra burden on the switch admin, who would have to define this ACL on all switches. Perhaps you can push a template via NMS/script to reduce that effort. But if the switch doesn't support dACL, then who knows if it even supports a per-user ACL.
I saw a blog posting where the following attributes were sent back to the NAS:
cisco-avpair="ip:inacl#1=deny ip any x",
cisco-avpair="ip:inacl#2=deny ip any x",
cisco-avpair="ip:inacl#3=deny ip any x",
cisco-avpair="ip:inacl#4=deny ip any x",
cisco-avpair="ip:inacl#5=deny ip any x",
cisco-avpair="ip:inacl#6=permit ip host x any",
cisco-avpair="ip:inacl#7=deny ip any any"Does that switch/IOS support URL redirection? That might be another hurdle to overcome.
Sounds like a bit more lab work is required
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 06:35 PM
As per the Security Configuration Guide for the Cat1000, it does support downloadable per-user ACLs. There are very specific limitations with this platform that are also described, including this important one:
"Only one 802.1X-authenticated user is supported on a port. If the multiple-hosts mode is enabled on the port, the per-user ACL attribute is disabled for the associated port."
The configuration required for the dACLs, however, relies on the 'ip device tracking' feature. The IP Source Guard section of the configuration guide states the following, so applying a per-user dACL (1 user per port) should work as long as you have 'ip device tracking' enabled and the host initiates some traffic on the network when connected.
"IP or MAC bindings are learned from static hosts by ARP and IP packets. They are stored in the device tracking database."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 09:05 PM
Hi Greg,
Thanks for sharing the link where it says support for "• IEEE 802.1x authentication with downloadable ACLs and redirect URLs to allow per-user ACL downloads from a RADIUS server or Cisco Identity Services Engine (ISE) to an authenticated switch."
I was referring Software Configuration Guide, Cisco IOS Release 15.2(7)E (Catalyst Digital Building Series Switches) where under IPv4 ACL Switch Unsupported Features topic it is mentioned that
Reflexive ACLs, URL Redirect ACLs, and Dynamic ACLs are not supported (except for some specialized dynamic ACLs used by the switch clustering feature)
Just look at the screenshot that i was referring.
Not sure which document i should refer to check the support of dACL for Catalyst 1000 Series Switches C1000-8T-E-2G-L with IOS Release 15.2.7E7
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 11:46 PM
Downloadable ACLs are not the same thing as Dynamic ACLs (also known as "Lock-and-Key" ACLs). These serve completely different functions.
See the following document for an example of Dynamic ACLs.
https://www.cisco.com/c/en/us/support/docs/security-vpn/lock-key/7604-13.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2023 12:36 AM
Hi Greg,
Thanks for correcting my understanding of Downloadable ACLs and Dynamic ACLs.
Really appreciate your efforts in the Cisco community.
I will update PoC result
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2023 07:24 AM
Hi @jitendrac
I would like to check with you if Catalyst 1000 is working with Cisco ISE Anyconnect Posture?
Because I plan to test the Cisco Switch C1000 with Cisco ISE Posture too. Please help to share.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2023 09:40 AM
15.2.7 is still the latest version of IOS available for Catalyst 1000. So nothing should have changed from this link previously shared in this thread: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst1000/software/releases/15_2_7_e/configuration_guides/sec/b_1527e_security_c1000_cg.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2023 07:50 AM
Yes, it worked perfectly without any issues. Our POC was successful.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide