- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Cisco ISE authentications for external domains users
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 03:18 AM - edited 03-11-2019 01:48 AM
Hi all,
I'd like to ask you about an scenario that I have on my network...
In my company we work with computers in my company domain "domainA", we authenticate users and computers in this domain by dot1x and we have other devices authenticated by mab (printers, IoT devices, not domainA computers, etc...)... our switches configuration is this:
authentication event fail action next-method
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
What the problem? sometimes I have users with external computers in "domainB", "domainC" or others... and these computers are configured with dot1x authentication and they're not "administrators" of this computers for disable the supplicant. These users work usually in the office of CompanyB... C, D.... (our customer with "domainB", "...C", "...D" ...) but sometimes have to work on my offices with my internal "domainA"... for the connection works correctly without problems I have to disable authentication on switchport or change the authentication priority/order on swithchport for authenticating mab first, and users dont's user always the same socket... or other internal user use this socket
For me this is a big problem, because I have more that 90.000 switchports with mobility and I don't want to configure statically the switchports for special users, maybe 800 users at the moment, I want to create an ISE policies with external domain computers/users rules to allow the connection... but I can't integrer my ISE with external Active Directory.
When I connect an external computer to my switches I see how the computer try to authenticate with and user ID, I can't compare the credentials with DomainB Active Directory, but... can I allow the connection if I know that user tries authentication with "domainB\user1" for example? If I can do it, I can create a policy condition similar to "identity contains = domainB\user1" ...¿?¿?
If you can help me with some example, it's very helpfull for me.
Thanks in advance!!
Best Regards!!
Marcos
Solved! Go to Solution.
- Labels:
-
AAA
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 12:36 PM
Sorry I misunderstood the scenario - You are describing a Contractor or Guest scenario.
If some users' 802.1X supplicants cannot be customized for your network, then I recommend allocating a username&password that they can use with WebAuth after 802.1X fails on your network with their credentials. This could done via your AD or via Sponsored Guest.
But the real issue below is that your end users do not trust your ISE certificate. Either it is self-signed or not part of a public CA chain so that the user's supplicant would trust it. That is why you get the failure in your screenshot. Since you cannot control the certificates on this user's computer, I recommend using using the Default Authorization (after they fail 802.1X) to redirect their web browser to do a WebAuth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 08:00 AM
This is not a switch configuration issue.
Users disabling or tweaking their supplicant configuration is a separate issue that you can handle by redirecting them to a WebAuth page by default if 802.1X does not work for any reason.
What you are trying to do is authenticate users via 802.1X on multiple AD domains.
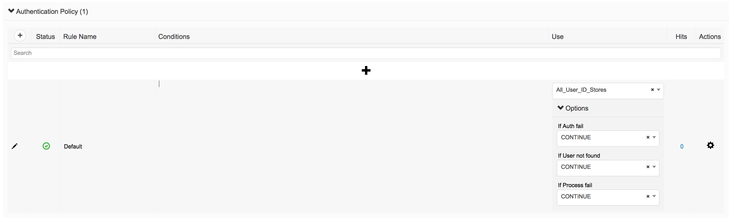
As long as you have joined ISE to each of the Active Directory domains @ Administration > Identity Management > External Identity Stores then you can easily do this on ISE using Administration > Identity Management > Identity Store Sequences. You may use the default All_User_ID_Stores and select all of your AD domains. Be sure to order them from most frequently used to least frequent to improve performance.
Then, in your Policy Set > Authentication Policy, verify that you have the following options chosen:
Using these settings tells ISE to run through all of the Identity Stores (domains) that you listed and If User Not Found to continue to the next Identity Store. I recommend using Continue on all of these so if there are any problems, the user can hit the Default Authroization Policy and ideally give the person an option to do WebAuth if their supplicant is unconfigured or misconfigured or they are a Guest.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 09:35 AM
Hi Thomas,
Thanks for your reply, I understand your reply but, as I tried to explaned in my first post, domainB is an external company domain, so I can't join my ISE to that domainB, but I want to allow authentications of users with "domainb\username" without check if password is correctly configured.
My last incident about this:
- My company is partner of Cisco for some projects
- Cisco configure a laptop with Cisco software and Cisco domain computer platform (windows + antivirus + anyconnect vpn + 802.1x supplicant, ... and others sw/config) and my company user uses this laptop with this configuration in Cisco office 3 days per week, but my user isn't local administrator in this laptop.
- My user comes to my office with this laptop the other 2 days per week and connects the computer in my company switches... my ISE isn't joined to Cisco AD, so I can't authenticate user/pass to Cisco AD... but I want to allow authentication if "identity" is equals to "cisco\username"... because in authentication log I can see the username...
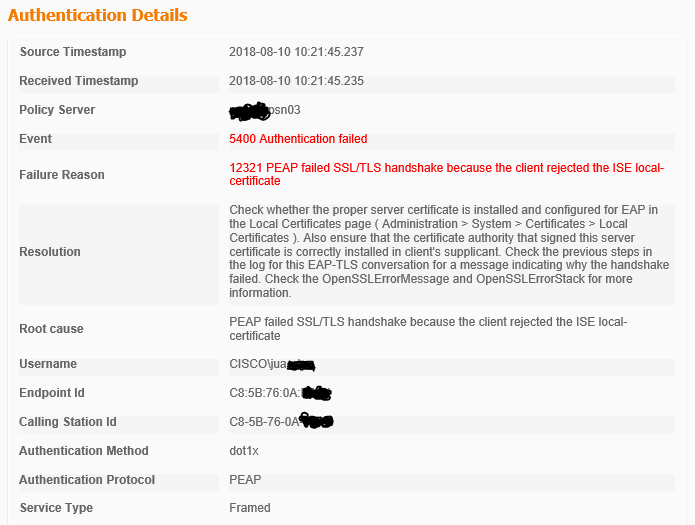
An example of my log:
Many thanks!!
B.R
Marcos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 10:49 AM - edited 08-14-2018 01:19 PM
The very first thing I would do is install the CA's certificates that signed the ISE cert into the Laptop Trusted Certificate list so the error that you are listing is gone (untrusted cert). The collect again the log and post it so we can check how to "tweak" the AUTHZ policy and make it work
If the Laptop MAC is in the ISE Endpoint Group DB (any endpoint group) then your MAB authentication should work so you can hit a customized AUTHZ policy that matches your requirements. If you DO NOT want the MAC in your ISE endpoint DB, you can enable CONTINUE on the MAB AUTHC Policy when it fails and then configure the AUTHZ policy accordingly. But be careful that allowing to continue does not break your security rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 12:36 PM
Sorry I misunderstood the scenario - You are describing a Contractor or Guest scenario.
If some users' 802.1X supplicants cannot be customized for your network, then I recommend allocating a username&password that they can use with WebAuth after 802.1X fails on your network with their credentials. This could done via your AD or via Sponsored Guest.
But the real issue below is that your end users do not trust your ISE certificate. Either it is self-signed or not part of a public CA chain so that the user's supplicant would trust it. That is why you get the failure in your screenshot. Since you cannot control the certificates on this user's computer, I recommend using using the Default Authorization (after they fail 802.1X) to redirect their web browser to do a WebAuth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 01:18 PM - edited 08-14-2018 01:19 PM
Based on my understanding when EAP authentication fails the process finishes there. You cannot reach the authorization part to make a redirect. I discussed this topic with Cisco guys because I wanted to use an AD attribute in the AUTHZ Policies for an AD Account with expired password so I could trigger a redirect (CoA) to a customized page for password update.
Unfortunately, the CONTINUE option when EAP Authentication fails does is not possible by RFC standards and indicated on ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 01:34 PM
Marcos,
Create a policy set with Network access or Radius dictionary and user-name attribute to filter out requests from from domainB/user. Then, use MAB to process your authentication policy.
IBNS 2.0 allows you to process dot1x and MAB concurrently and also you can determine what to do if authentication fails etc. You can also determine the action to do when dot1x fails.
Here is the doc for that
If MAB does not work for you you can do a Central web authentication with guest portal.
Thanks
Krishnan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2018 09:36 AM
Hi all!!
Thanks for your comments, now my test users're out of office, I'll do some test and I'll confirm you.
Thank!!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide