- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: CoA Terminate in Hotspot portal is not initiating DHCP refresh
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2017 03:17 PM
Hi,
I have configured my hotspot portal to send CoA terminate so that I could push guest on Wired to different VLAN but I dont see a session terminated of wired endpoint and the endpoint do not refresh their IPs in the new VLAN.
Is CoA Terminate same as CoA PortBounce ?
It does not look like from the packet capture as it does not have port-bounce cisco AVP attribute.
When I issue a CoA Port Bounce from ISE the endpoints come in the correct IP range.
I know that in the past Jason has mentioned that Vlan change is not recommended in guest portals due to inconsistency but I thought CoA Terminate should still be able to bounce the port.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2017 09:33 AM
Correct. Terminate will not trigger IP refresh as host without agent/supplicant will not detect without link state change. If willing to send port bounce in all cases where session terminate is normally sent, then it would be possible to manipulate the NAD profile used for these wired switches so that terminate always results in port bounce.
Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2017 08:29 AM
Investigating
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2017 08:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2017 09:33 AM
Correct. Terminate will not trigger IP refresh as host without agent/supplicant will not detect without link state change. If willing to send port bounce in all cases where session terminate is normally sent, then it would be possible to manipulate the NAD profile used for these wired switches so that terminate always results in port bounce.
Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2017 11:25 AM
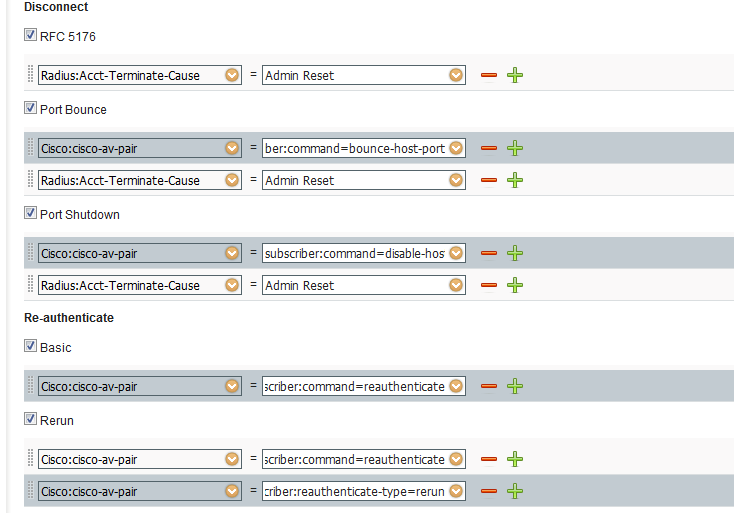
Thanks Craig. Which of the below options should I change for Terminate to send Port Bounce ?
Also do you think there are any disadvantages of making this change which could affect some other areas ?
It is for a big ISE/TrustSec customer so want to make sure that we dont break any working scenario.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2017 11:50 AM
You would need to duplicate the Cisco profile and assign it to the NAD in question. The tricky part is that you need to make sure you set this NAD Profile in the AuthZ Profile. AuthZ Policy Rule must then reference this profile. By disabling RFC5176 option under Disconnect you will cause all request for terminate to be sent using port bounce.
You would need to test your various use cases that entail CoA session terminate to assess impact. For wireless, session terminate should be sufficient to terminate connection and force DHCP. For wired you need bounce without supplicant to detect VLAN change. However, if port bounce all terminate, then need to expect client to start from square one on each terminate. That may be desired behavior, but need to test your wired use cases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2017 12:15 PM
I disabled the Disconnect option but the CoA request was sent using disable-host-port and the port was disabled.
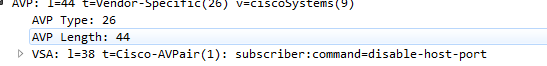
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2017 12:24 PM
There are three Disconnect options in sequence of priority:
1) RFC5176
2) Port Bounce
3) Port Shutdown
If #2 is properly configured and #1 unchecked, then Port Bounce should be sent on Session Terminate. If you properly see #1 when enabled but #3 occurs when #1 disabled, then sounds like a defect. You could just change the definition for #1 to include port-bounce.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2017 01:56 PM
Thanks for the logic Craig.
After playing around with it a couple of times I am able to send port bounce attributes (verified by packet captures) by disabling RFC5176 and also by having it identical to Port Bounce.
However the session is behaving as a normal disconnect/reauth and there is no port bounce
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2017 02:46 PM
Then sounds like an issue with switch not properly processing port-bounce request. If able to see port bounce with REST API or sending from Admin UI with exact same directive, then expect there may be some issue with your syntax under CoA config of NAD profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2017 04:16 AM
I am testing the similar scenario.
The switch I use is 3750V2-24PS.
What I see in ISE live log is:
Steps
| 11202 | Received disconnect and port shutdown dynamic authorization request | |
| 11217 | Prepared the disconnect dynamic authorization request | |
| 11100 | RADIUS-Client about to send request - ( port = 1700 , type = Cisco CoA ) | |
| 11101 | RADIUS-Client received response |
This makes me thin that the issue is in the ISE itself and not in the switch.
Could you comment?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2017 06:30 AM
Try and run debug CoA on the switch.
When I use the customization recommended by Craig I get the below output on the switch.
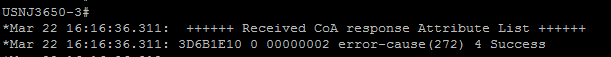
When I try to issue CoA Portbounce from Live sessions I get the below output
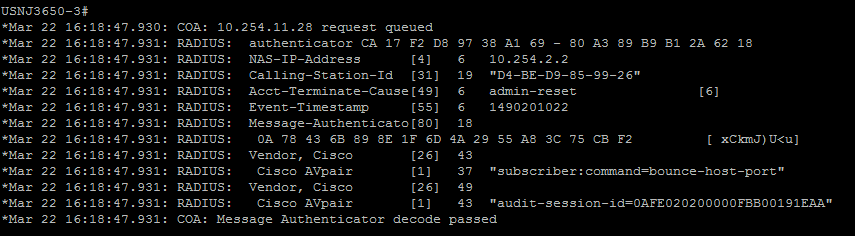
It looks like the switch is not able to parse the customized CoA port-bounce.
What's strange is both the packet captures show the same AVP.
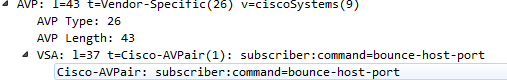
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2017 07:21 AM
May be time to open TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2017 08:55 AM
Craig,
I take back that both packets are same when I manually edit the RFC5176 to include 'disable-host-port' AVP.
What I missed is the difference in CoA Code.
The CoA port bounce form Live Sessions look like
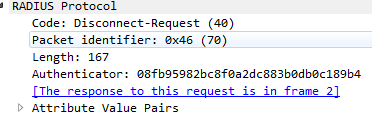
The CoA port bounce with customized AVP looks like
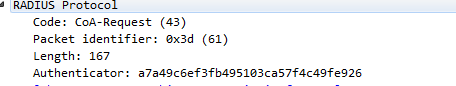
I think once the switch receives a CoA with code 40 it thinks it is a RFC disconnect-request and does not look into the Cisco AVP pairs to find the 'port-bounce' AV pairs.
I opened a TAC case who will recreate this in lab and probably file a bug.
I'll still try to make this work by disabling RFC5176 option.
However I am seeing inconsistency in this approach as the ISE is sending 'disable-port-host' sometimes instead of 'host-port-bounce' which could be very dangerous to implement in production.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 12:20 PM
hi utkarsh,
I am just exploring the situation you posted but I could not find the ISE configuration part with the "disconnect" options. Could you please provide the path to this option?
thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

