- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Dynamic VLAN Assignment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2018 07:23 AM
HI
I'm trying to setup vlan assignment via wireless, have followed Dynamic Attribute with ISE: VLAN Assignment.
Running on 2.2
Certain devices and users can only go to certain vlans.
The WLC has the VLANs and able to connect to them.
Only thing that have changed are the domain and attribute.
Everything looks fine, can see on radius logs it the user connects to vlan 631, but the actual device connects to vlan 630.
Screen shots attached and steps below.
Steps
| 11001 | Received RADIUS Access-Request |
| 11017 | RADIUS created a new session |
| 15049 | Evaluating Policy Group |
| 15008 | Evaluating Service Selection Policy |
| 15048 | Queried PIP - DEVICE.Device Type |
| 15048 | Queried PIP - Normalised Radius.RadiusFlowType |
| 15004 | Matched rule - Dot1X |
| 11507 | Extracted EAP-Response/Identity |
| 12300 | Prepared EAP-Request proposing PEAP with challenge |
| 11006 | Returned RADIUS Access-Challenge |
| 11001 | Received RADIUS Access-Request |
| 11018 | RADIUS is re-using an existing session |
| 12302 | Extracted EAP-Response containing PEAP challenge-response and accepting PEAP as negotiated |
| 12318 | Successfully negotiated PEAP version 0 |
| 12800 | Extracted first TLS record; TLS handshake started |
| 12805 | Extracted TLS ClientHello message |
| 12806 | Prepared TLS ServerHello message |
| 12807 | Prepared TLS Certificate message |
| 12808 | Prepared TLS ServerKeyExchange message |
| 12810 | Prepared TLS ServerDone message |
| 12811 | Extracted TLS Certificate message containing client certificate |
| 12305 | Prepared EAP-Request with another PEAP challenge |
| 11006 | Returned RADIUS Access-Challenge |
| 11001 | Received RADIUS Access-Request |
| 11018 | RADIUS is re-using an existing session |
| 12304 | Extracted EAP-Response containing PEAP challenge-response |
| 12305 | Prepared EAP-Request with another PEAP challenge |
| 11006 | Returned RADIUS Access-Challenge |
| 11001 | Received RADIUS Access-Request |
| 11018 | RADIUS is re-using an existing session |
| 12304 | Extracted EAP-Response containing PEAP challenge-response |
| 12305 | Prepared EAP-Request with another PEAP challenge |
| 11006 | Returned RADIUS Access-Challenge |
| 11001 | Received RADIUS Access-Request |
| 11018 | RADIUS is re-using an existing session |
| 12304 | Extracted EAP-Response containing PEAP challenge-response |
| 12305 | Prepared EAP-Request with another PEAP challenge |
| 11006 | Returned RADIUS Access-Challenge |
| 11001 | Received RADIUS Access-Request |
| 11018 | RADIUS is re-using an existing session |
| 12304 | Extracted EAP-Response containing PEAP challenge-response |
| 12318 | Successfully negotiated PEAP version 0 |
| 12812 | Extracted TLS ClientKeyExchange message |
| 12813 | Extracted TLS CertificateVerify message |
| 12804 | Extracted TLS Finished message |
| 12801 | Prepared TLS ChangeCipherSpec message |
| 12802 | Prepared TLS Finished message |
| 12816 | TLS handshake succeeded |
| 12310 | PEAP full handshake finished successfully |
| 12305 | Prepared EAP-Request with another PEAP challenge |
| 11006 | Returned RADIUS Access-Challenge |
| 11001 | Received RADIUS Access-Request |
| 11018 | RADIUS is re-using an existing session |
| 12304 | Extracted EAP-Response containing PEAP challenge-response |
| 12313 | PEAP inner method started |
| 11521 | Prepared EAP-Request/Identity for inner EAP method |
| 12305 | Prepared EAP-Request with another PEAP challenge |
| 11006 | Returned RADIUS Access-Challenge |
| 11001 | Received RADIUS Access-Request |
| 11018 | RADIUS is re-using an existing session |
| 12304 | Extracted EAP-Response containing PEAP challenge-response |
| 11522 | Extracted EAP-Response/Identity for inner EAP method |
| 11806 | Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge |
| 12305 | Prepared EAP-Request with another PEAP challenge |
| 11006 | Returned RADIUS Access-Challenge |
| 11001 | Received RADIUS Access-Request |
| 11018 | RADIUS is re-using an existing session |
| 12304 | Extracted EAP-Response containing PEAP challenge-response |
| 11808 | Extracted EAP-Response containing EAP-MSCHAP challenge-response for inner method and accepting EAP-MSCHAP as negotiated |
| 15041 | Evaluating Identity Policy |
| 15006 | Matched Default Rule |
| 22072 | Selected identity source sequence - All_User_ID_Stores |
| 15013 | Selected Identity Source - Internal Users |
| 24210 | Looking up User in Internal Users IDStore - host/3Q6DZ72.someplaceelse.com |
| 24216 | The user is not found in the internal users identity store |
| 15013 | Selected Identity Source - All_AD_Join_Points |
| 24431 | Authenticating machine against Active Directory - All_AD_Join_Points |
| 24325 | Resolving identity - host/3Q6DZ72.someplaceelse.com |
| 24313 | Search for matching accounts at join point - someplaceelse.com |
| 24319 | Single matching account found in forest - someplaceelse.com |
| 24323 | Identity resolution detected single matching account |
| 24344 | RPC Logon request failed - STATUS_UNSUCCESSFUL,ERROR_RPC_NETLOGON_FAILED,3Q6DZ72$@someplaceelse.com |
| 24303 | Communication with domain controller failed - uhlad01.someplaceelse.com,ERROR_RPC_NETLOGON_FAILED |
| 24343 | RPC Logon request succeeded - 3Q6DZ72$@someplaceelse.com |
| 24470 | Machine authentication against Active Directory is successful - All_AD_Join_Points |
| 22037 | Authentication Passed |
| 11824 | EAP-MSCHAP authentication attempt passed |
| 12305 | Prepared EAP-Request with another PEAP challenge |
| 11006 | Returned RADIUS Access-Challenge |
| 11001 | Received RADIUS Access-Request |
| 11018 | RADIUS is re-using an existing session |
| 12304 | Extracted EAP-Response containing PEAP challenge-response |
| 11810 | Extracted EAP-Response for inner method containing MSCHAP challenge-response |
| 11814 | Inner EAP-MSCHAP authentication succeeded |
| 11519 | Prepared EAP-Success for inner EAP method |
| 12314 | PEAP inner method finished successfully |
| 12305 | Prepared EAP-Request with another PEAP challenge |
| 11006 | Returned RADIUS Access-Challenge |
| 11001 | Received RADIUS Access-Request |
| 11018 | RADIUS is re-using an existing session |
| 12304 | Extracted EAP-Response containing PEAP challenge-response |
| 15036 | Evaluating Authorization Policy |
| 15048 | Queried PIP - EndPoints.LogicalProfile |
| 15048 | Queried PIP - Network Access.AuthenticationStatus |
| 15004 | Matched rule - Basic_Authenticated_Access |
| 15016 | Selected Authorization Profile - PermitAccess |
| 22081 | Max sessions policy passed |
| 22080 | New accounting session created in Session cache |
| 12306 | PEAP authentication succeeded |
| 11503 | Prepared EAP-Success |
| 11002 | Returned RADIUS Access-Accept |
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2018 09:13 AM
To add to Tim's comment, you are matching PermitAccess Authorization Profile which cannot be modified, which also means that you cannot be returning a new VLAN assignment. First make sure you match correct authorization.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2018 07:36 AM
Hi,
At first glance, it appears that an incorrect authorization rule is being applied. Please verify that the correct rule is being matched.
Regards,
-Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2018 07:56 AM
Hi, the laptop is authenticating and getting the IP.
Looks correct, which part are you referring to?
cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2018 08:06 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2018 09:13 AM
To add to Tim's comment, you are matching PermitAccess Authorization Profile which cannot be modified, which also means that you cannot be returning a new VLAN assignment. First make sure you match correct authorization.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2018 02:29 AM
Hi
Thanks for replying, I see what you mean, it's only hitting the default Profile, need to try and figure this out logically, I work better from looking at examples
cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2018 04:51 PM
The steps does not seem matching your word doc.
== Steps ==
...
15004 | Matched rule - Basic_Authenticated_Access | |
| 15016 | Selected Authorization Profile - PermitAccess |
...
== Word doc ==
No authorization policy rule with a name "Basic_Authenticated_Access"
Assuming your word doc is correct, your endpoint is giving the authz profile "vlan", and the screenshot of tunnel attributes, including Tunnel-Private-Group-ID, is from the auth detail report, then I think VLAN 631 not configured on your WLC or some configuration issue. Please check whether your WLC has an interface and IP configured for this VLAN. You may debug further on WLC with WLC CLI commands -- "debug client <mac>" and "debug aaa event enabled"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2018 05:53 AM
hi
All VLANS are trunked on the WLC, this is a mirror image of our live system. I disabled the default policy, so only would connect if hits the correct one.
What have found is the devices is connecting, but authenticating now under PC host name and not AD User Name which the but still not applying the vlan still.
Just trying to get my head round it again
cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2018 06:28 AM
Please ensure an interface created in WLC with VLAN 631.
For instance, I wanted to overwrite a WLAN default to VLAN 50 to 51 so I created a new interface for VLAN 51 in the screenshot below.
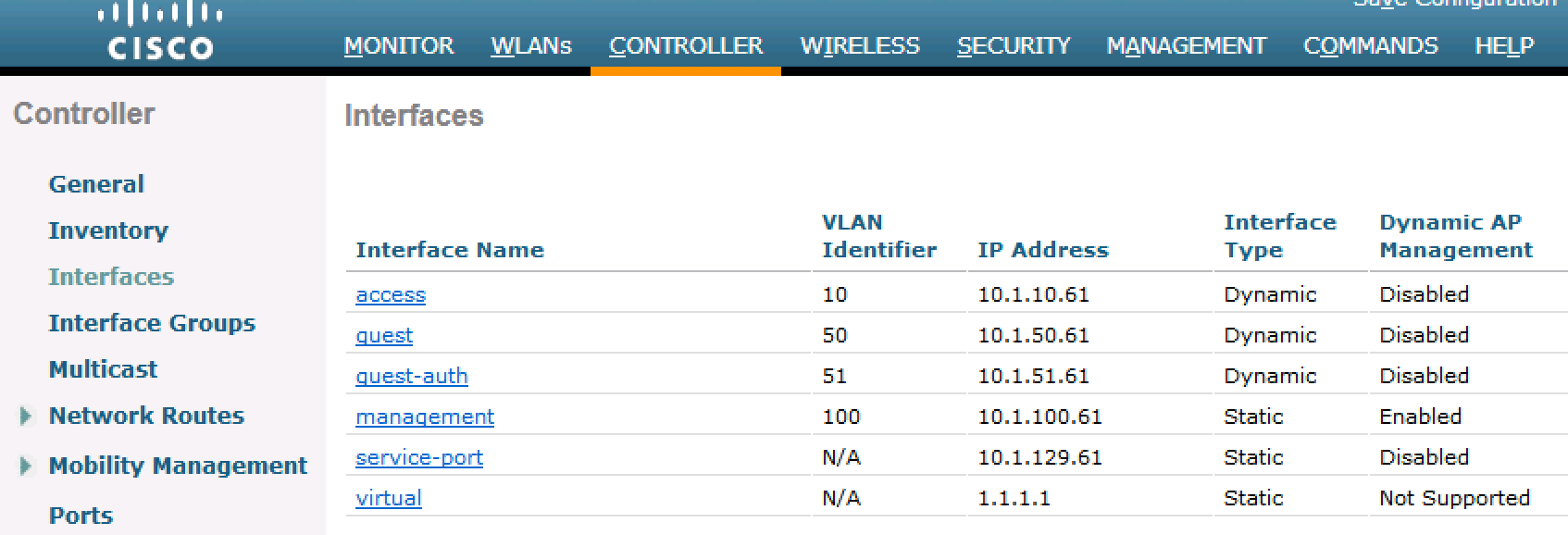
Anyhow, the WLC debug should tell why it's not working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2018 06:44 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2018 07:18 AM
Thanks for all reply's, now got it working.
Not quiet how the video showed
cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2018 07:29 AM
If possible, please update us what was the missing piece and how you figured it out.
I believe Hosuk's video emphasizing the configurations on the ISE side, but not the network device side..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2018 01:04 AM
Hi
In the end I removed and started from scratch, tested how it was done in the video again, didn't work. So instead added users in Identity Management, created User ID Group and then created Auth Policy for vlan631. then built the policy set.
cheers
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide