- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: EAP-TEAP: First time user login/chicken & egg scenario
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 01:59 AM
Hi
Does EAP-TEAP solve the first time user login scenario when using EAP-TLS?
So, you image a new Windows PC, it gets the machine certificate and always authenticates fine. Then, a new user is given that device that's authenticated successfully and tries to login. The authentication fails because the User certificate isn't downloaded before network access is taken away.
I know you can put an ISE chaining policy with 'user failed, machine successful'. Will the device keep this access when the user auth fails so the certificate can be downloaded? And if the certificate has downloaded, will it attempt another User authentication so that SGTs/ACLs can be applied? Or would they need to log off/have the 'user failed, machine successful' policy force re-authentication?
Thanks
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2021 02:30 PM
From the testing I've done with TEAP-EAP-TLS and the 'user or computer' setting with expired/missing user certs, you can use the 'user failed and machine succeeded' chaining result to provide access when the user cert is not enrolled. After the certificate is enrolled, however, the native supplicant does not automatically trigger another authentication event. I have not tried pushing a short reauth period in that state, but it might be tricky as the cert is enrolled via GPO which uses it's own timers.
You might have a look at what windows logs trigger in this scenario to see if there is a specific event or set of events you could use to force a GPO update and cert enrollment, then force a restart of the Wired AutoConfig service.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2022 01:50 PM
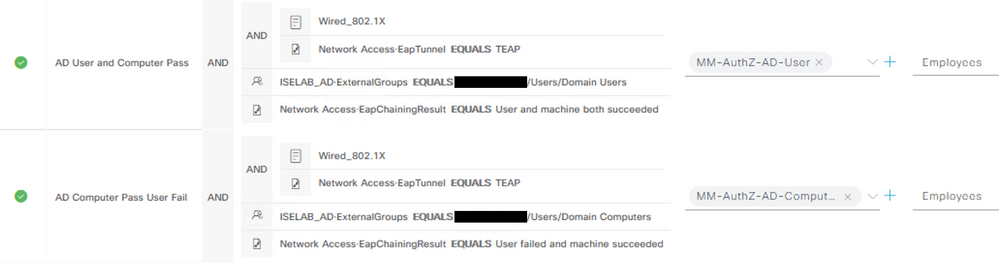
This is the AuthZ Policy for my TEAP use case described earlier. I'm just using the top-level Domain Computers and Domain Users, but you could use more specific AD group matches if you prefer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 05:08 AM
Yes, with chaining the user should logout and in to trigger CoA and get new
dacls or wait for reauthenticate timer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 05:12 AM
Thank you for clearing that up. It's kind of frustrating that this is the best option we have for this sort of thing at the moment.
What alternative is there that would mean the user doesn't need to relogin/have a very short reauthentication timer on Machine only auths? Use MS-CHAPv2 for the User authentication and EAP-TLS for the computer? I don't think MS-CHAPv2 is generally recommended anymore?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2021 11:03 PM
Hi @DanMN
As far as I know and have tested, if the native Windows supplicant is set to user or machine auth, and EAP-TLS is used (certificate based auth) then Windows doesn't perform a network authentication when a user logs in at the locked screen. AFAIK this actually only work with EAP-PEAP (AD machine account used at bootup and logoff, and user AD account used at login)
I have not yet tried EAP-TEAP but I believe that cert based auth can be used for both user and machine auth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2021 02:30 PM
From the testing I've done with TEAP-EAP-TLS and the 'user or computer' setting with expired/missing user certs, you can use the 'user failed and machine succeeded' chaining result to provide access when the user cert is not enrolled. After the certificate is enrolled, however, the native supplicant does not automatically trigger another authentication event. I have not tried pushing a short reauth period in that state, but it might be tricky as the cert is enrolled via GPO which uses it's own timers.
You might have a look at what windows logs trigger in this scenario to see if there is a specific event or set of events you could use to force a GPO update and cert enrollment, then force a restart of the Wired AutoConfig service.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2022 01:03 AM
Hey seen this thread. I would be interested to see your Authorization policy that allows a certain user in a AD group to get an SGT and to get authorized while using eap-chaining and teap.
Im trying to figure out the best Autz policy to create to authorize a user and push and SGT for that particular AD group.
any help appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2022 01:50 PM
This is the AuthZ Policy for my TEAP use case described earlier. I'm just using the top-level Domain Computers and Domain Users, but you could use more specific AD group matches if you prefer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2022 04:57 PM
thanks for that Greg that clears it up. I wasn't sure how particular you could get with the AD groups. As we will be pushing an SGT to a user , based on their AD group. The machine will do cert based authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2023 02:26 AM
Hello DanMN,
Could you please specify if you find some solution to solve chicken-egg issue for the first user's login?
I am stuck with the same issue and wondering if we have any good/effective solution to manage it...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide