- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: EAP-TLS Authentication and Active Directory Group Authorization
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2021 11:31 AM
Hello community,
We will Implement Network Access Control with ISE server and EAP-TLS Protocol for Endpoints Authentication using the Windows native client and Machine Certificates generated from the Internal CA of the company (Windows). We also configured Active directory as an External Source for ISE and we want to grant authorization using different ACLs depending on Active Directory Groups.
Is it possible to apply the following configuration in ISE Policies?
Authentication: EAP-TLS inner protocol, PEAP outer protocol
Authorization Condition: Active Directory User Group, Result: DACL
Any suggestion or comment is well appreciated.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2021 02:03 PM
Yes.
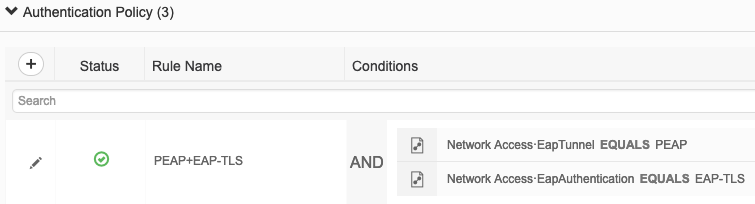
Authentication Policy:
For Authorization Policies with AD, see examples @ Microsoft Active Directory Groups Authorizations
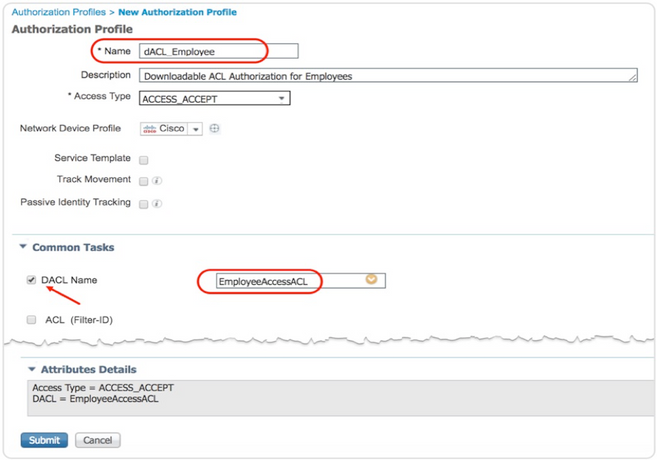
For dACL:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2021 12:32 PM - edited 01-11-2021 12:35 PM
You can absolutely accomplish this with your ISE policies. In order to meet the two wishes you can utilize several different conditions. Here are a few ideas:
Is it possible to apply the following configuration in ISE Policies?
Authentication: EAP-TLS inner protocol, PEAP outer protocol
-Inside your policy you can create an authc condition that looks like this: NetworkAccess:EAPAuthentication EQUALS EAP-TLS. You can also create a global allowed protocols list that gets referenced at the global level that is only referenced for hosts onboarding to the network via EAP-TLS.
Authorization Condition: Active Directory User Group, Result: DACL
-Assuming you have several unique networks in your environment you will want to create separate authz profiles (under: Policy->Policy Elements->Results->Authorization->Authorization Profiles) so that you can apply respective DACLs to each host and their unique AD group (since the assumption will be different levels of access). Your authz condition to reference unique AD groups would look like this: <name>ExternalGroups EQUALS abc.def/OU/OU/<group>
There are some great examples and resources found here: Cisco ISE & NAC Resources - Cisco Community
Good luck & HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 12:41 PM
Hi Mike,
Thank you for your reply.
So to accomplish my goals my authorization condition would only have to include the external groups of each domain group we want to give a specific DACL? And the 802.1x native client would only need to be configured to send authentication for computer, not user right?
Thank you in advanced.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 01:01 PM
So to accomplish my goals my authorization condition would only have to include the external groups of each domain group we want to give a specific DACL?
-Yes. Along with any other conditions you wish to utilize to make onboarding more secure. My suggestion is to test capabilities to meet your unique needs in your environment.
And the 802.1x native client would only need to be configured to send authentication for computer, not user right?
-This depends on what you are trying to accomplish. If you wish to onboard via comp cert with EAP-TLS that will work just fine. In that case your authz condition will match against external security groups in AD that contain the computer objects. If you wish to look into something such as eap-chaining it is a bit more complex, and in order to rely on native supplicant (no AnyConnect) you have to meet a few requirements. Take a peek here: Using TEAP for EAP Chaining – Cisco ISE Tips, Tricks, and Lessons Learned (ise-support.com)
HTH!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2021 02:03 PM
Yes.
Authentication Policy:
For Authorization Policies with AD, see examples @ Microsoft Active Directory Groups Authorizations
For dACL:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide