- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Forcing a MAC on a specific port with MAB
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2018 01:40 AM
They have MPLS in place and different customers.
They have one switch and customer A on port 1, customer B on port 2. Both MAC addresses are in ISE, and they want do
Hello,
I have a customer that has a very paticular case. They provide connectivity to some customers (shops and other businesses) on their network controlled with ISE. They want to do simply MAB authentication, from a list of MAC addresses and guarantee that the customer A will ONLY connect to port 1, and is not allowed on port 2. MAC address is known to ISE.
What would be the best way to configure this in scalable way to enforce customer segregation?
They saw the feature „VLAN Radius Atributes in Access Requests” in IOS 15.2(3)E. However, their 16.6 Versions or even 15.X don’t know that functionality.
They have in VLAN name the VPN of the customer, to be able to differentiate. However, the issue is that each switch has to be verified if feature is supported.
Any other idea on how to do it?
Thanks a lot in advance
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2018 09:16 AM
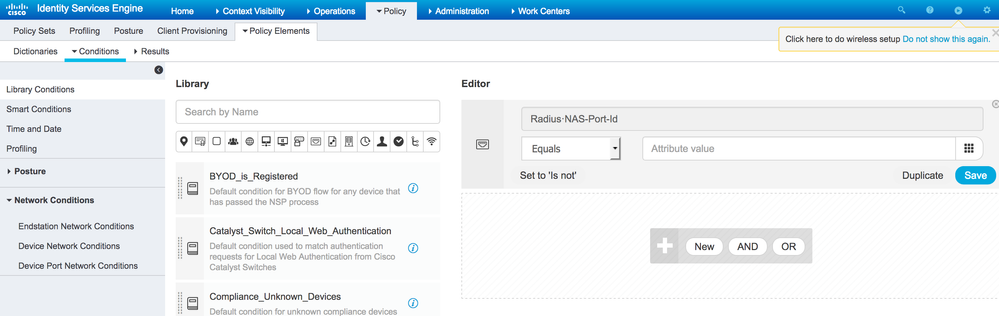
Create a custom attribute with name say "AssignedPort" and type as String.
Edit the endpoint at Context Visibility > Endpoints > Edit > Custom Attributes > AssignedPort. Enter the value as "GigabitEthernet1/0/2" (this is just an example).
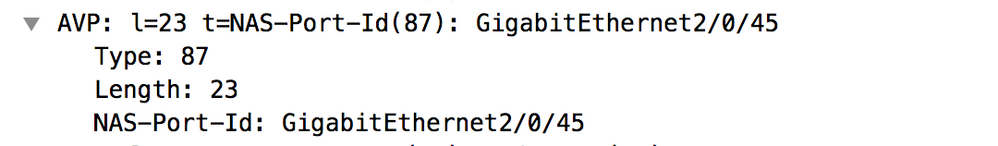
Create one authorization rule with condition as RADIUS:NAS-Port-Id equals Endpoints:AssignedPort
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2018 10:41 AM
RADIUS protocol send port number in radius attribute so you can use this attribute to configure a condition:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2018 02:11 PM
Thanks,
but the issue in doing it this way, would be that for every port they need to have a rule, so it would easily go out of hand in terms of scaling.
It should be done in a better way so that the number of rules can be contained.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2018 09:16 AM
Create a custom attribute with name say "AssignedPort" and type as String.
Edit the endpoint at Context Visibility > Endpoints > Edit > Custom Attributes > AssignedPort. Enter the value as "GigabitEthernet1/0/2" (this is just an example).
Create one authorization rule with condition as RADIUS:NAS-Port-Id equals Endpoints:AssignedPort
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2018 12:33 AM
That might definitively work, I will discuss with the customer !
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide