- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Guest session is not being terminated
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Guest session is not being terminated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2021 04:13 AM
Version: 2.7.0.356
NAD: Non Cisco /Meraki
Steps:
1. Authenticate guest using CWA, there is no audit session-id attribute
2. Send radius session-timeout as 120 seconds in postauth radius accept packet
3. Send Radius Acct start after successful authentication ( post-auth mab ) with acct-session-id
4. After 120 seconds, NAD sends Radius acct-stop packet with same acct-session-id
5. Immediately trigger mac auth from NAD
Expected:
Redirect role from ISE since session is terminated
Reality:
Getting post auth role from ISE, Again after 120 seconds, when mab is triggered we get proper redirect role
Seeing same issue even if mac-auth is triggered after 1 min of session expiry.
If mab is triggered after 2 minutes of session expiry, then getting redirect role properly.
Note: If we don't send radius acct start and stop packet, the behavior is as expected. We get redirect role after session expiry.
Please help me to understand, if I am doing something wrong.
Attached screenshots and guest.log
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2021 05:21 PM
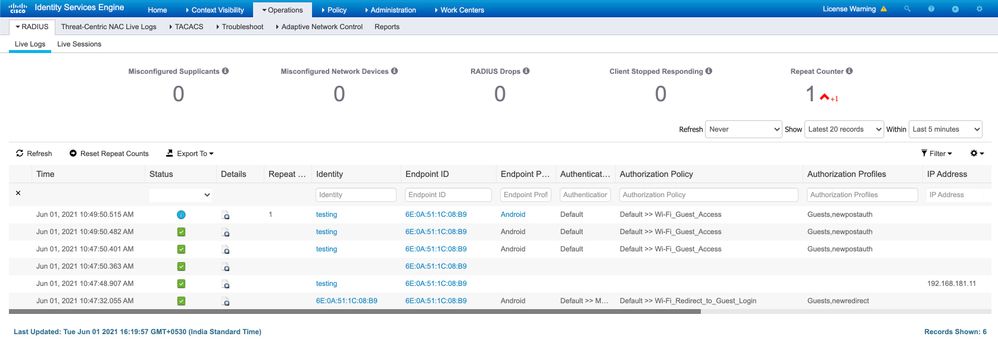
Everything looks good to me with your RADIUS log.
- Initial MAB defaults to Wifi_Redirect_to_Guest_Login.
- You login.
- After that, ISE recognizes the MAC address and puts you into Wifi_Guest_Access.
That's how Guest_Flow works because it recognizes the endpoint MAC for the guest account duration (Daily, etc.). You will need to wait the entire account duration or manually purge the endpoint info from ISE for it to be considered a new Guest Endpoint that gets redirected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2021 09:46 AM
Auth policy is set to 'Guest Flow', It is not 'Identity Group equals Guest EndPoints'. In the latter case, it will recognise until endpoint is purged right ? My use case is to force re-login of guest client after 30 minutes. How can I achieve that ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2021 02:25 PM
Please use ISE Guest Access Prescriptive Deployment Guide as your reference.
You have not specified what type of Guest portal you are trying to use: Hotspot, Self-Registered, or Sponsored. That changes your options. You said "Authenticate guest using CWA..." so I will assume Self-Registered.
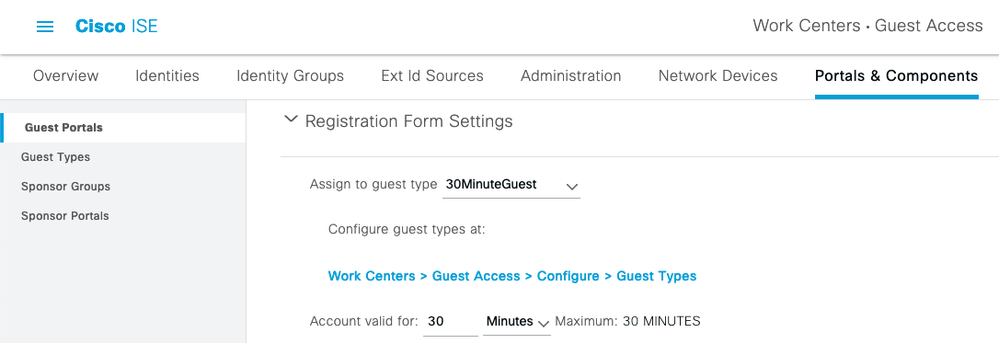
First, create a Guest Type with your 30-minute guest limit. Go to ☰ > Work Centers > Guest Access > Portals & Components > Guest Types and create a new 30MinuteGuest type with these values:
Then go to your Guest portal and assign your 30MinuteGuest Type:
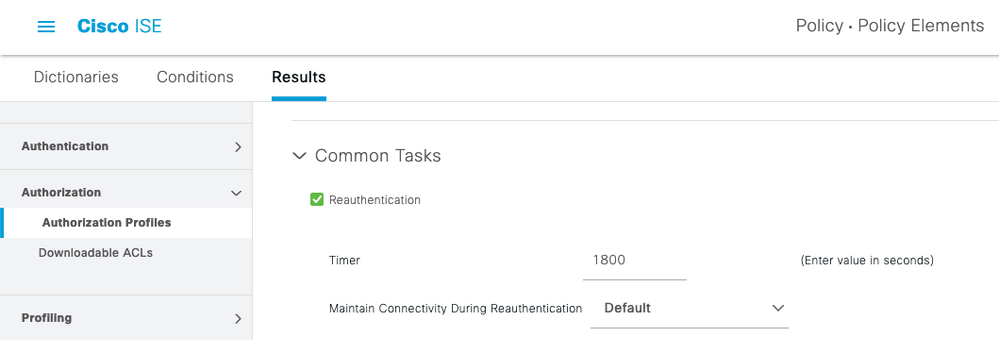
Create a new Authorization Profile for your 30MinuteGuest . I am only showing the 1800 second timeout but you will need to apply whatever ACLs or segmentation you would want for your Guest to limit their access to your internal network if not using an anchor-controller guest architecture.
ISE has a built-in Wi-Fi_Guest_Access policy and Wi-Fi_Redirect_to_Guest_Login (both disabled by default) in the Default Policy Set. You may simply customize with your 30MinuteGuest Authorization Profile :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2021 06:22 AM - edited 06-08-2021 06:22 AM
> If mab is triggered after 2 minutes of session expiry, then getting redirect role properly.
In order to support 3rd-party NADs that do not support CoA reauth, ISE uses this timer to determine whether to continue with the sessions.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide