- Cisco Community
- Technology and Support
- Security
- Network Access Control
- how can i configure for running TACACS with ISE?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
how can i configure for running TACACS with ISE?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 02:05 AM
after i setup and check TACACS log , it display this error msg "22056 Subject not found in the applicable identity store(s)"
anything i miss to configure ? or which part i should adjust setting ?
ISE verison:2.4.0
detail steps like this :
Steps
| 13013 | Received TACACS+ Authentication START Request | |
| 15049 | Evaluating Policy Group | |
| 15008 | Evaluating Service Selection Policy | |
| 15041 | Evaluating Identity Policy | |
| 15013 | Selected Identity Source - Internal Endpoints | |
| 13045 | TACACS+ will use the password prompt from global TACACS+ configuration | |
| 13015 | Returned TACACS+ Authentication Reply | |
| 13014 | Received TACACS+ Authentication CONTINUE Request | |
| 15041 | Evaluating Identity Policy | |
| 15013 | Selected Identity Source - Internal Endpoints | |
| 24209 | Looking up Endpoint in Internal Endpoints IDStore | |
| 24217 | The host is not found in the internal endpoints identity store | |
| 15013 | Selected Identity Source - Internal Endpoints | |
| 24209 | Looking up Endpoint in Internal Endpoints IDStore | |
| 24217 | The host is not found in the internal endpoints identity store | |
| 22016 | Identity sequence completed iterating the IDStores | |
| 22056 | Subject not found in the applicable identity store(s) | |
| 22058 | The advanced option that is configured for an unknown user is used | |
| 22061 | The 'Reject' advanced option is configured in case of a failed authentication request | |
| 13015 | Returned TACACS+ Authentication Reply |
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 03:30 AM
Check your Authentication Policy for Device Admin. It appears that the matching rule is choosing the Internal Endpoints store, or may the Internal Endpoints store has been added to the ALL_User_ID_Stores identity sequence (Under Administration > Identity Management > Identity Source Sequences).
In short, TACACS+ should be authenticating USERS, not MAC Addresses, which is what the Internal Endpoints store is used for during MAB. Check and update Authentication rules to make sure you are selecting correct Allowed_Protocols (for example, Default Device Admin) and that ID store under Authentication Rules point to Internal Users or external user ID store.
Craig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 09:19 AM
You did not specify what network device you are using.
Please consult our many docs and videos on TACACS configuration to review the configuration steps for your network device :
ISE Design & Integration Guides > Device Administration (TACACS+) :
Configure and Troubleshoot External TACACS Servers on ISE - Cisco
Cisco CLI access using Radius and ISE
ISE 2.0 Adds AAA Device Administration with TACACS+ - YouTube
ISE 2.0: TACACS+ Command Authorization - YouTube
How To: ISE TACACS+ Configuration for ASA Network Devices
How To: ISE TACACS+ Configuration for IOS Network Devices
ISE 2.0: Configuring TACACS+ on IOS - YouTube
How To: ISE TACACS+ Configuration for Cisco NX-OS Network Devices
ISE 2.0: Configuring TACACS+ on NX-OS Devices - YouTube
How To: ISE TACACS+ Configuration for Wireless LAN Controllers (WLCs)
ISE 2.0: Configuring WLC Authentication with TACACS+ - YouTube
TACACS+ for WLC (ISE 2.2) — Networking fun [Video]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2018 01:58 AM
thanks for your reply , now user can auth via TACACS from ISE ,
but i have another issue for detail behavior , for example :
i want this user cannot config lldp via telnet , and i done configurations like below :
configure TACACS command like this :
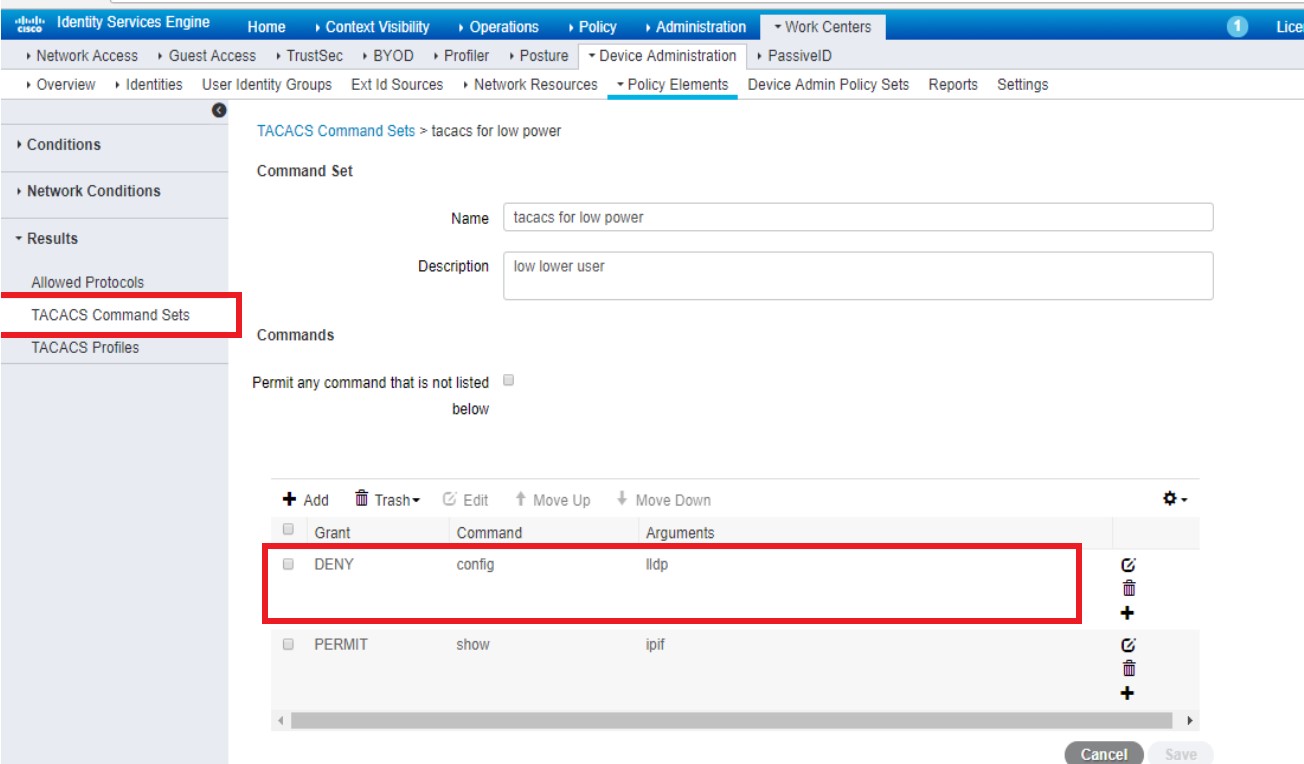
and configure authorization policy like this , and i am sure this rule be hit when this user login via telnet :
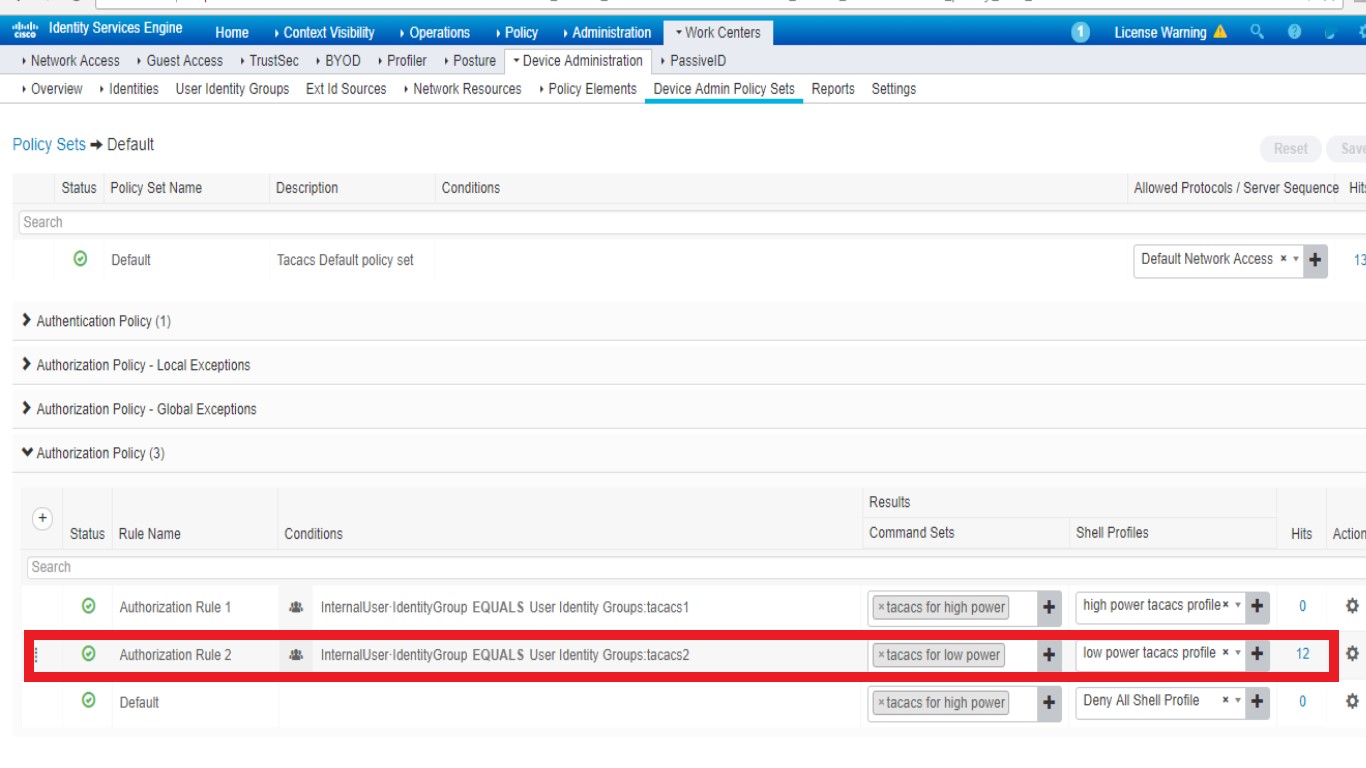
but user still can config lldp well via telnet :

this behavior is not my expectation , i do not know why ? any configurations i miss ? or some setting i need to adjust ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2018 08:59 AM
Please check T+ live logs and see whether your NAD sending command authorization requests to ISE and which rules are matched.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2018 07:02 PM
thanks for your reply , after i checked the logs , there is nothing in "matched command set"
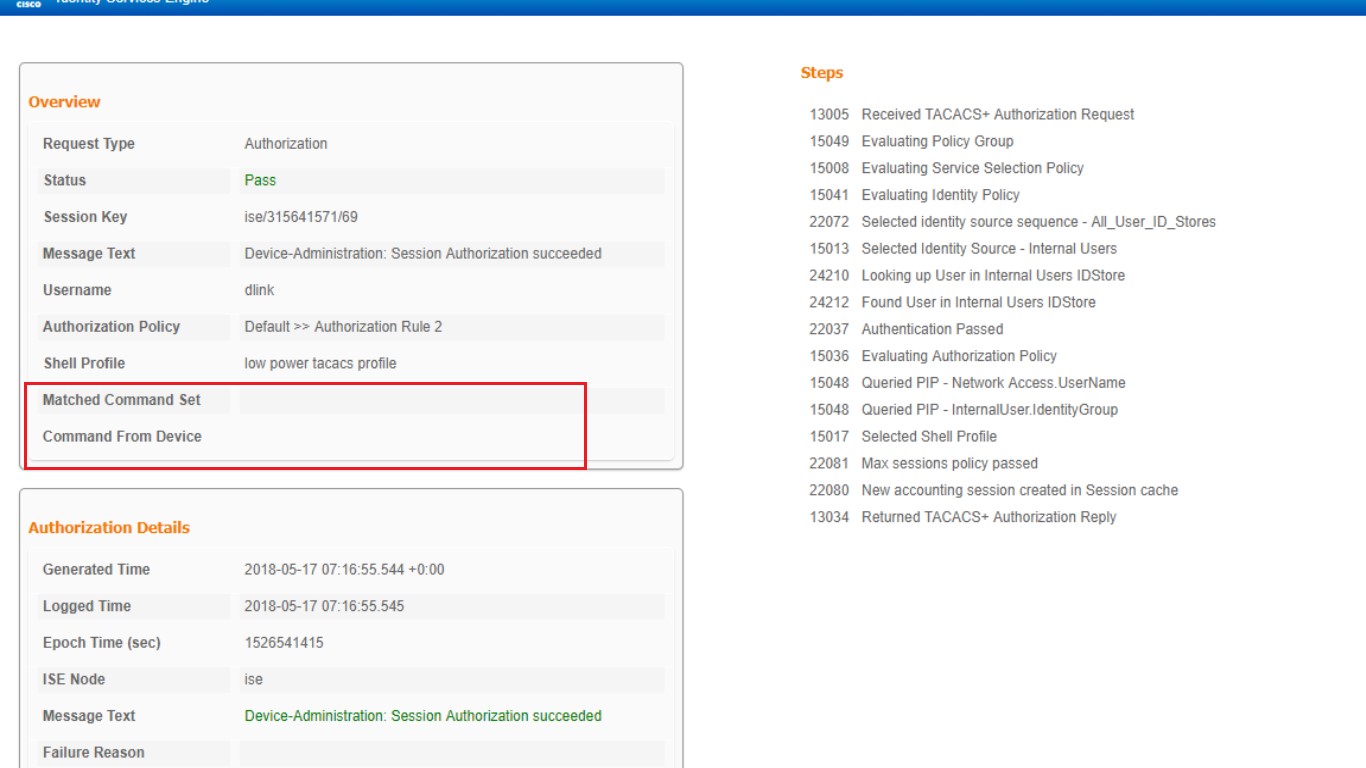
but i do configured the rule and make sure it be hit , it is called "tacacs for low power" :

why it cannot hit this command sets ? any setting i need to adjust ? or some configurations i miss ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2018 06:23 AM
The authorization you showed in your screenshot is one for a shell profile, because its overview has
| Message Text | Device-Administration: Session Authorization succeeded |
and one of the steps gives --
| 15017 | Selected Shell Profile |
Below shows T+ live logs with T+ authC, T+ shell authZ, and T+ command authZ.

Here shows the auth detail report of one of command authZ requests from the above.

Its overview has
| Message Text | Device-Administration: Command Authorization succeeded |
And, its steps have:
| 15018 | Selected Command Set | |
| 13024 | Command matched a Permit rule |
Thus, it does not appear your NAD sending command authorization at all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2018 10:51 AM
Please post additional or followup questions in a new question.
This helps ensure that each specific question is addressed, especially after we mark the question as Answered.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide