- Cisco Community
- Technology and Support
- Security
- Network Access Control
- iOS Wireless Users Being Prompted to Trust Public Certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2019 12:24 PM - edited 03-26-2019 07:43 AM
Hi,
I'm using ISE 2.3 P5 and a Cisco WLC 5508 8.5.140.0.
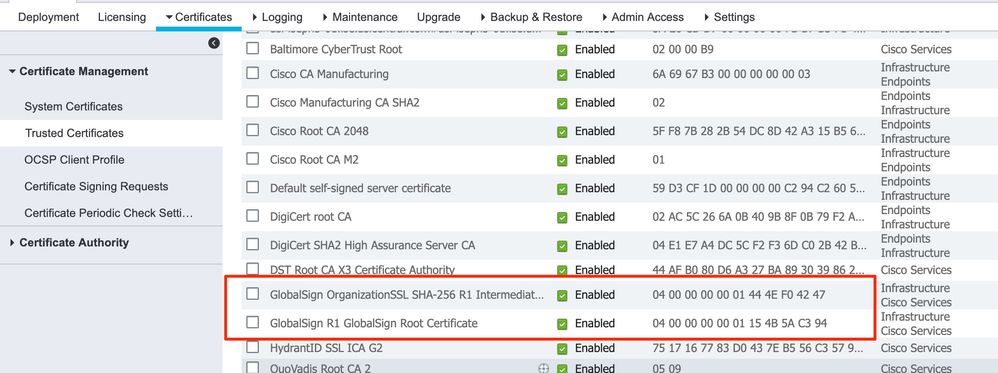
I have two ISE PSNs. Both PSNs have a wildcard cert with *.ise.mydomain.com in the CN field. This certificate was issued by Globalsign. I've installed the Globalsign Root CA Cert & the Globalsign Intermediate Cert into my Trusted Certificate Store in ISE.
I recognize Wildcard certificates are an issue while performing EAP on Windows clients. That is a separate issue and I will be obtaining a new cert to fix that issue, I would like to make sure the new cert fixes this other issue too.
To my issue....
The wildcard certificate is a Globalsign cert. My iPhone iOS 12.1.4 has Globalsign's Root CA in the Trust Store. I've verified this by reviewing the Serial Number of the Root CA cert on Globalsign's website, then looking at Apples list of available trusted root certificates webpage. The serial numbers match up.
https://support.apple.com/en-us/HT209501
My assumptions and reading...
Being that Globalsigns Root CA cert is preinstalled on my iPhone, my iPhone should accept identity certificates issued by the Globalsign Intermediate CA. However, the document How to Implement Cisco ISE Server Side Certificates on page 17, it states "When an iOS client first communicates to a PSN it will not explicitly trust the PSN certificate, even though a trusted Certificate Authority has signed the certificate."
My question is how to get around the iOS device not trusting the PSN certificate? I don’t believe end users should have to trust an already trusted certificate.
Thanks for any tips.
Tim
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 07:43 AM
I believe this is the answer to the question "Why do Apple iOS devices force a user to Click Trust on a trusted certificate".
Note 28 of this document it states:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-3/compatibility/ise_sdt.html#pgfId-141382
When Apple iOS devices use Protected Extensible Authentication Protocol (PEAP) with Cisco ISE or 802.1x, certificate warnings might be displayed even for publicly trusted certificates. This usually occurs when the public certificate includes a Certificate Revocation List (CRL) distribution point that the iOS device needs to verify. The iOS device cannot verify the CRL without network access. Click Confirm or Accept in the iOS device to authenticate to the network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2019 02:08 PM
Sometimes the ISE node does not send the intermediate certificate along with its certificate during TLS handshake. It causes a warning on mobile devices. After a node reboot, the behavior may change and the browsers do not complain any more.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2021 03:59 AM
Except iPhones...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2019 01:57 AM
First things first, there are known issues with Windows clients when the wildcard is in the CN of a certificate. The recommended approach to this that we know works fine is to nest the wildcard in the SAN fields. Aaron Woland covers this in the Cisco Live session BRKSEC-3697, Advanced ISE Services, Tips and Tricks. I would recommend reviewing it and cutting a new cert to avoid issues.
Now your iPhone issue sounds like one we ran in to with the Digicert High Assurance EV signing authority. Since certificate trust relies on a chain of issue, missing the intermediate that issued the certificate should always result in a prompt to trust. This is by design from a security stand point, and also a pain in the butt. The phone trusts the root, but it still doesn't trust the intermediate signing CA. We were able to push the intermediate cert down inline with the MDM wifi profile to managed iphones, and got rid of the prompt.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 06:11 AM
Thank you, I understand the issue on the Windows computers and can deal with that.
I’ve installed the Root CA and the Intermediate CA Certificate into the ISE trusted store.
Is there any way to configure ISE to send both of these certificates while preforming PEAP, the same way that a web server can, if configured? I don’t have an MDM and most of these devices are personal devices so pushing the Intermediate cert is impossible.
As I have a public certificate installed on the PSN, I’m hoping there is a way for end users to connect to 802.1x Enterprise networks without having to click Trust in order to ‘trust’ an already publicly trusted certificate.
Thank you,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 02:47 AM
Thank you for this article , it is very helpful. I have the same issue where we have ipads introduced on our network and keep. New devices could not connect as the certificate would not issue to the devices. It is believed or assumed to be the issue with issuing certificate related to the SCEP service.
How do you install GlobalSign OrganisationalSSL.
Your help is greatly appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 03:32 AM
You can visit the website of the GlobalSign website and then download their CA certificates.
The trick is to know WHICH ONE to download.
In ISE you simply install them under Administration > System > Certificates > Trusted Certificates
Click the Import button and then make sure you tick Trust for Authentication within ISE and Trust for client authentication and SYSLOG. Just for good measure, also tick the Validate Cert box. Enter friendly name etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2019 01:17 PM
The only way I know of to get phones to stop prompting to trust certs the first time they client connects is install the WLAN settings via an MDM. If you are having the users manually connect to the SSID they will always have to trust the certificate the first time. That is the nature of mobile devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2019 10:51 AM - edited 03-23-2019 06:57 AM
@paul ,
Thanks for the tip.
Can you help me understand the technical reason behind this. I've been reading about PEAP auth and cannot find an answer.
Specifically, I wonder if the certificate exchange over PEAP works differently than the certificate exchange over HTTPS.
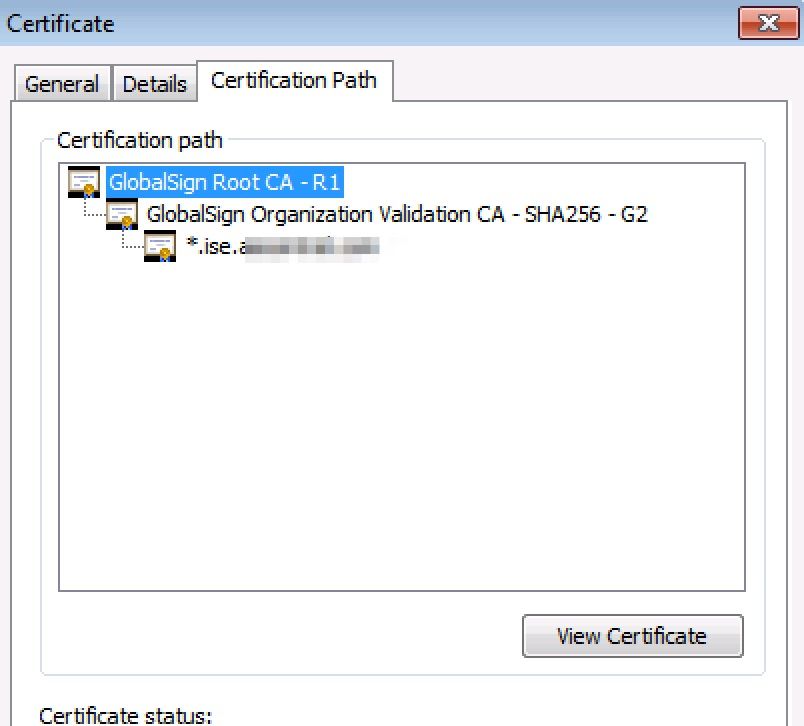
The ID cert installed on the ISE node looks like this.
I've checked the serial numbers on all 3 of the certificates in this certificate chain. My iPhone has the GlobalSign Root CA R1 certificate in its Trusted Store. My iPhone does not have the GlobalSign Organizational Validation certificate in the Trusted Store and obviously, it doesn't have the wildcard in the Trusted Store.
So when I go to the ISE Admin Portal page I get to it and I do not receive any errors. My iPhone trusts the wildcard certificate because it Trusts the Root. When I connect to the wireless SSID and attempt PEAP I get the prompt to Trust the cert.
I'd like to understand the technical details about why, when using PEAP, the certificate chain isn't trusted.
Thanks very much, I appreciate any insight.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 07:43 AM
I believe this is the answer to the question "Why do Apple iOS devices force a user to Click Trust on a trusted certificate".
Note 28 of this document it states:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-3/compatibility/ise_sdt.html#pgfId-141382
When Apple iOS devices use Protected Extensible Authentication Protocol (PEAP) with Cisco ISE or 802.1x, certificate warnings might be displayed even for publicly trusted certificates. This usually occurs when the public certificate includes a Certificate Revocation List (CRL) distribution point that the iOS device needs to verify. The iOS device cannot verify the CRL without network access. Click Confirm or Accept in the iOS device to authenticate to the network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2021 02:13 AM
Looks like the latest android versions are having the same behavior.
Can anyone confirm?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide