- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 09:48 PM - edited 02-21-2020 11:13 AM
I'm testing my wireless authentication.
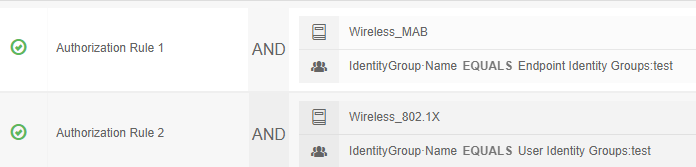
You have set policies for MAB and 1X.
Rule1 = MAB
Rule2 = 1X
Like the ACL, i know that policies are applied from top to bottom.
Wireless authentication performs 1X authentication after MAB authentication in order.
This is as I wish.
However, if you change the rule order, only 1X authentication is performed.
Why not perform the MAB certification of Rule1 when the order is changed?
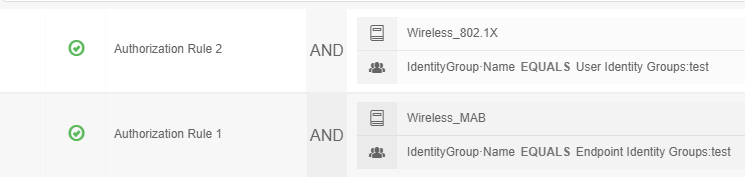
Rule2 = 1X
Rule1 = MAB
Is 1X authentication a higher priority than MAB?
Why not perform the MAB certification of Rule1 when the order is changed?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 10:04 PM
Now, if a switch is configured for both MAB and Dot1x, and the switch sees an eapol start frame, it will start dot1x with the client.
The order of your two authentication policy sets are irrelevant because they contain different flows. They are treated top down, but only if they match on the same criteria. Authorization rules within the policy set specific to MAB or dot1x are very important because of this but again come down to matching criteria first. In order to hit #1 you have to be doing MAB, in order to hit #2, you have to be doing dot1x. So again, this comes back to the network device configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2020 09:37 PM
You can't authenticate an endpoint with MAB on an 802.1x secured Wireless SSID. If the SSID is configured for 802.1x, the endpoint must authenticate using an 802.1x authentication method (PEAP, EAP-TLS, etc).
Unlike Wired switches, there is no concept of falling back to a MAB authentication if 802.1x fails for Wireless.
You can only authenticate an endpoint with MAB when using an Open or PSK (requires WLC 8.3 code or newer) SSID.
Cheers,
Greg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 10:04 PM
Now, if a switch is configured for both MAB and Dot1x, and the switch sees an eapol start frame, it will start dot1x with the client.
The order of your two authentication policy sets are irrelevant because they contain different flows. They are treated top down, but only if they match on the same criteria. Authorization rules within the policy set specific to MAB or dot1x are very important because of this but again come down to matching criteria first. In order to hit #1 you have to be doing MAB, in order to hit #2, you have to be doing dot1x. So again, this comes back to the network device configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2020 12:04 AM
Thank you for your reply.
But the infra here is wireless authentication in PC - WLC - ISE sequence.
Can you answer me again using wireless authentication as an example, not authentication on Switch
And please reply more easily. I'm using a translator.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2020 07:34 AM
1. With IBNS 1.0, you set the order directly on the switchport
2. With IBNS 2.0, you set the order in your control policy, which the policy then gets applied to the port.
On wireless, it's a bit different. The WLAN config dictates if the clients+WLC will do 802.1x or MAC filtering.
Typically the WLAN will be configured for WPA2 - 802.1x or MAC Filtering but usually not both. I would say it is not very common for WLANs to be configured for both, and it's not like a switch where you do one then the other. If you enable both on the same WLAN then the endpoints would need to be configured for 802.1x still.
There are two common use cases for MAC filtering on a WLAN.
1. Guest with an open SSID and web redirect
2. iPSK, where you define separate pre shared keys for different groups of predefined mac addresses in ISE. This mixes MAC filtering, wpa2, and PSK for the security mode. But it does not include 802.1x.
What are you trying to accomplish?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2020 09:04 PM
The current MAB rule is Permit if the client's MAC exists in the endpoint group.
But I would like to know why 1X authentication is Rule 1 and MAB authentication is Rule2 and does not go through MAB authentication.
Is there a problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2020 09:37 PM
You can't authenticate an endpoint with MAB on an 802.1x secured Wireless SSID. If the SSID is configured for 802.1x, the endpoint must authenticate using an 802.1x authentication method (PEAP, EAP-TLS, etc).
Unlike Wired switches, there is no concept of falling back to a MAB authentication if 802.1x fails for Wireless.
You can only authenticate an endpoint with MAB when using an Open or PSK (requires WLC 8.3 code or newer) SSID.
Cheers,
Greg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2020 02:35 PM
Rule 1 has the condition on Wireless MAB so only authentications matching that will report hits. The same goes for Rule 2 on Wireless 802.1X.