- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 1.3 certificate issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE 1.3 certificate issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2015 08:55 PM - edited 03-10-2019 10:19 PM
Hi experts,
I have tried to replicate an issue that my customer is having:
issue: when running client provisioning on default port 8905, the portal certificate shows that it's using the certificate created for the Admin. However, when visiting guest portal or running onboarding process (using port 8443 which is the default one), the certificate is presented with the correct one (the one used for the portal).
Here is what I have setup in my lab:
1. in ISE 1.3, installed two certificate: one for admin and the other for portal access:
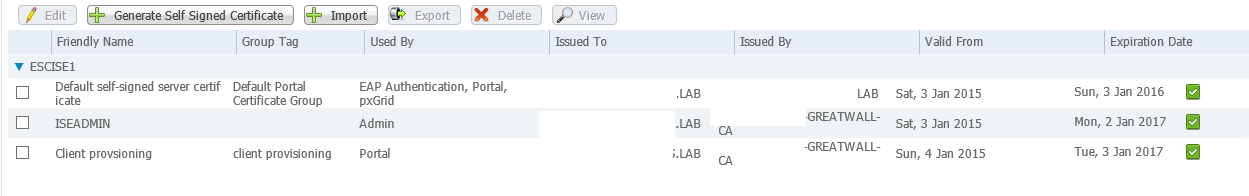
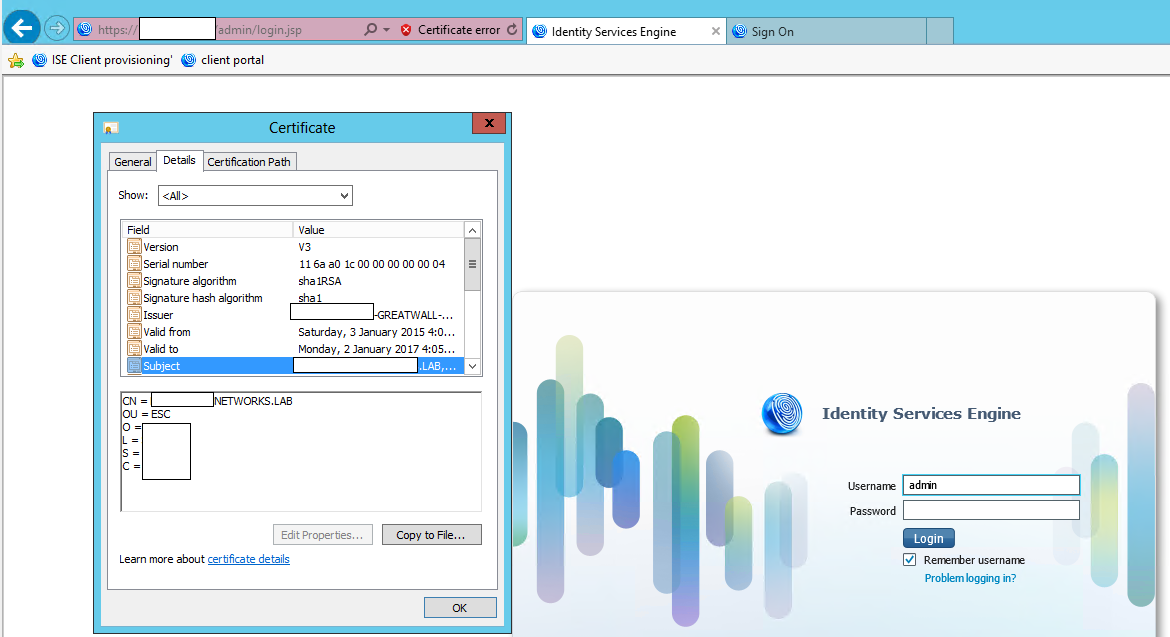
2. when accessing the admin page and the client portal, I can see that it's using the correct certificate. ( the OU=ESC one is the admin certificate and the OU=MS one is the portal certificate)

However, when accessing the test client provisioning portal on 8905, the certificate shows it's using the admin one:
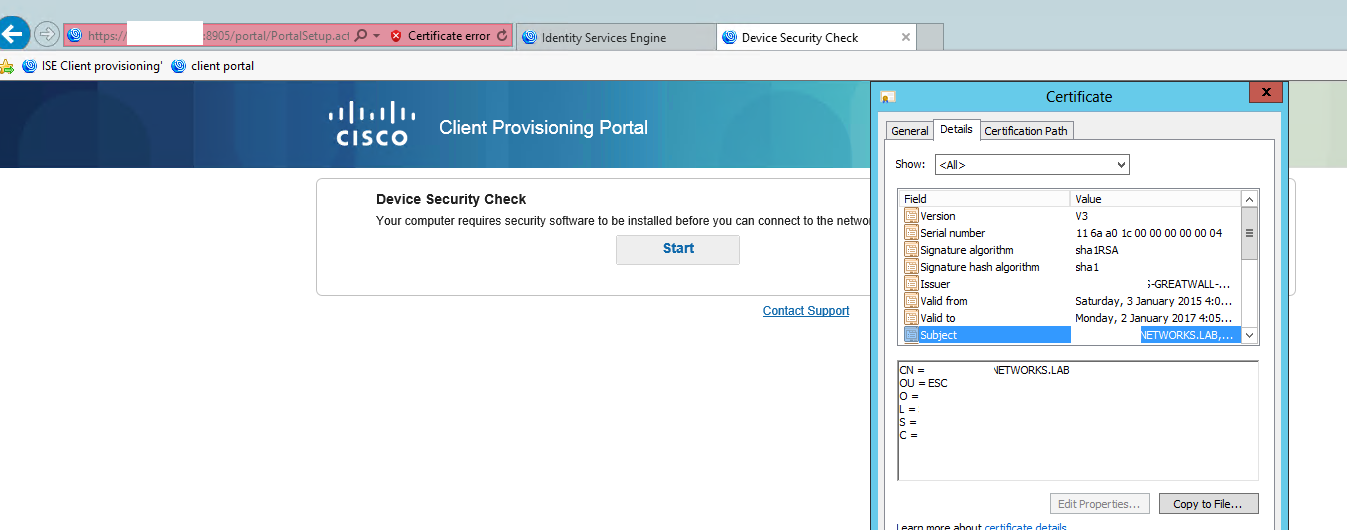
In the adminstration->device portal mgmt->client provisioning portal, the port is used as default 8443. It makes more sense it uses the client provisioning certificate rather than the admin certificate when the portal is redirected on to port 8905.
Is the issue an as-designed feature or is there additional configuration needs to be implemented?
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2015 03:39 PM
Hi guys,
Did my question make sense? Any thoughts?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2015 04:51 PM
Hello Meng, just to confirm that I understand your issue:
1. When going through the device provisioning flow - The incorrect certificate is presented?
2. When manually browsing the the client provisioning flow - The correct certificate is presented?
Thank you for rating helpful posts!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2015 05:06 PM
Hello Neno,
Thanks for the reply!
Let me clarify: when I access the client provisioning portal on default 8443 which URL is generated by the ISE, I can see the correct certificate (OU=MS) is presented. But when I manually change the port from 8443 to 8905 in the same URL and access, ISE brings me to the same portal page, but this time the incorrect certificate is presented (OU=ESC which I generated for the admin portal).
So it seems that ISE presents a wrong certificate (the one for admin) when user is redirected to the provisioning portal on a port other than port 8443. I believe ISE should present the portal certificate usage in this case. I am not sure if this is an as-designed feature, or some additional configuration should be done.
Let me know if you still have questions with this.
Many thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2015 06:56 PM
Thank you for the clarification Meng! This definitely sounds like a bug. Changing the port from the default one should not change the certificate. I would recommend creating a case with Cisco TAC to confirm this and if needed request that they file a defect/bug.
Please let us know what is the outcome!
Thank you for rating helpful posts!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2016 05:42 PM
It's a documentation bug and an enhancement request.
The certificate for client provisioning etc that is presented on 8905 is always the admin certificate so that certificate needs to have the FQDNs in it that systems will be hitting when connecting to that port. I believe this is being added to the documentation to explain.
An enhancement has been requested to configure the system to use the port specified for the portal (such as 8443/8444/etc) for provisioning and so present the same certificate.
As usual, the only real certificate configuration that works consistently is a single SAN certificate across all servers that has a wildcard in the SAN entries.
Eg.
CN= ise.example.com
SAN DNS= ise.example.com
SAN DNS= *.example.com
This covers all servers and all portals. The only thing generally missing is to be able to audit which server is being connected to based on the certificate.
You could however issue the same type of certificate for each individual server but just add the server name as a SAN entry per server so:
CN= ise.example.com
SAN DNS= ise.example.com
SAN DNS= *.example.com
SAN DNS= ise-svr-01.example.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2015 01:11 PM
Hi Meng,
I'm having the exact same issue that you described in your post. Have you managed to solve it by now?
Thanks,
Gabriel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2016 07:26 PM
Hi Meng,
Did this ever get resolved? I'm hitting the same issue on ISE 2.1 and if it's been around that long, I assume it's a configuration issue rather than a bug now.
Any updates?
Thanks
Ben
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2016 12:38 PM
I'm also experiencing the issue on 2.1 on the MyDevices Portal. Were you ever able to resolve it?
I entered a TAC case today and am awaiting a reply. I'll try to post the solution if anyone else is encountering this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2016 12:16 PM - edited 04-02-2018 02:06 PM
I have resolution to this issue in my environment.
I only receive the certificate error when I try to access the portal using https. When that happens, it hits the admin interface (on port 443) and redirects to the portal (port 8443).
If I try to access the portal using regular http, I do not get the cert error.
The workaround I'm going to use in my environment is to regenerate the admin cert with a SAN for the portal FQDN.
I hope this helps anyone else encountering this issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2016 05:00 AM
Hey, all.
I have this behaviour on the provisioning portal on ISE 2.1.
The portal shows up with the wrong certificate, therefore generates a certificate warning on all clients that use the anyconnect ise posture module ....
Is there any comment from cisco on your TAC case for this ??
Rgs
Frank
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide