- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.4 Integration with Qualys - VA Scan Not Running
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE 2.4 Integration with Qualys - VA Scan Not Running
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2018 07:05 PM - edited 02-21-2020 11:01 AM
Hi,
I'm trying to perform a VA scan with Qualys and ISE when a workstation executes a 802.1x authentication.
I can see that the authorization profile for the VA Scan was called and I've integrated Qualys via the Threat Centric NAC portion of the ISE Web GUI.
I've checked the Qualys dashboard and no scan was initiated.
Any insights provided are deeply appreciated.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2018 12:30 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2018 04:02 PM
Have you followed the integration steps in
http://cs.co/ise-guides > Qualys > How To Integrate ISE and Qualys for Threat-Centric NAC using STIX Technology ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2018 07:12 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2018 08:15 PM
John,
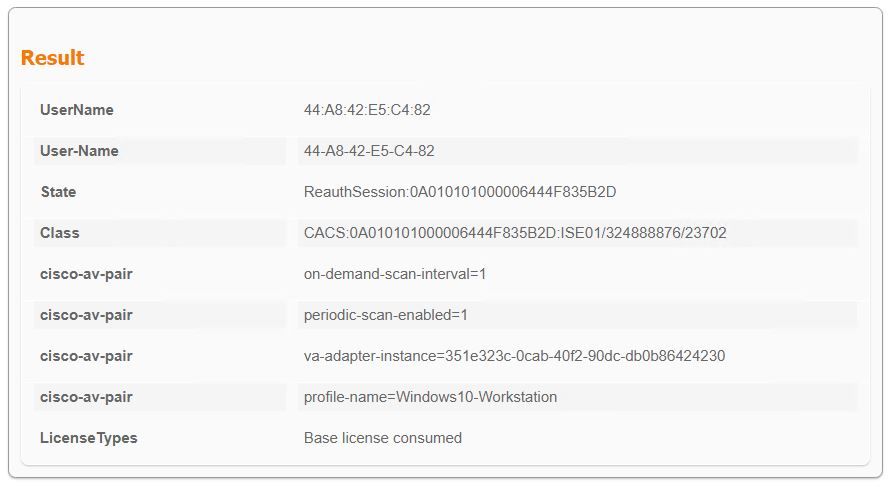
The Qualys documents are missing a very key setup piece. In the Qualys setup after you define everything and assign it to a PSN. There is a field marked Option Profile. That Option profile needs to exactly match the profile name defined in the Qualys cloud that should be used for the scan. Your Qualys admins will know what that means. I think it default to Default. If you debug things you will see the scan being submitted but you don't have the right Option profile and the Qualys cloud never executes.
I have told this to the BU in the past to update the documentation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2018 08:55 PM
Paul,
On the Qualys setup in ISE, I've indicated the same Option Profile name on the configuration which is the same as the one in the Qualys Option Profiles tab.
I've waited for few hours now and the scan still does not start.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2018 09:11 PM
John,
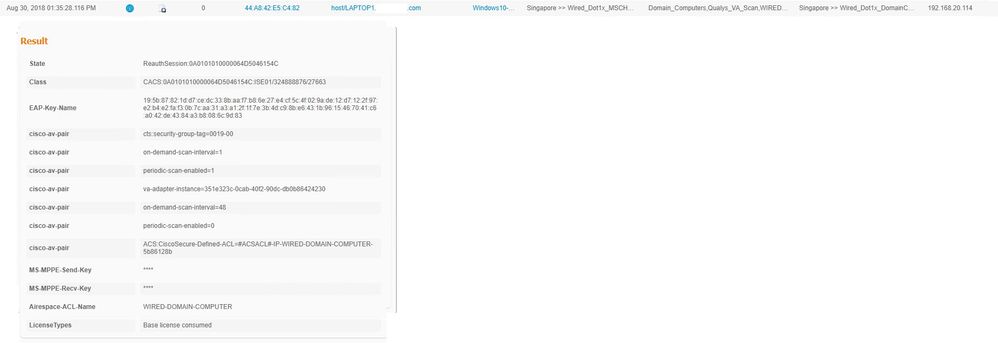
Are you correctly learning the IP of the device? I didn't see the IP in the RADIUS log you posted, but you may have cut it off. Also the log entry you posted was definitely not a Dot1x session. It was a MAB authentication. Did you mean to apply it to a Dot1x rule? Not that it should matter I think.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2018 10:40 PM
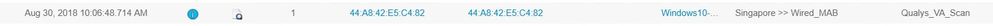
Yes the IP address is recognized. And I've applied the profile to both MAB authorization and Wired 802.1x authorization.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2018 04:23 AM
Well you hit my limits on this topic. :)
Turn on TC-NAC debugs on the PSN you are running this on and verify the request is being submitted to Qualys. That way you know which side you need to troubleshoot. I think there is a way to see the received request on the Qualys side as well.
FYI, after spending time working on this at a customer here are my notes I sent to the BU on my thoughts.
- Currently there is no way on the Qualys cloud TC-NAC definition in ISE to specify the priority of the scan request. The requests all come in with a priority of 0 which means the scan will run after all the other scan jobs run. The customer’s scan priority for their normal scan jobs is 5. There should be an option to set scan priority in the connector.
- Why can’t ISE take in CVSS score data from scans ISE did not request? ISE can take in AMP threat data as soon as it connects to the AMP cloud, but CVSS score data will only show up on scan submitted by ISE. Is it a correlation to endpoint issue?
- ISE doesn’t appear to use/receive the composite CVSS score from Qualys or have the ability to use the composite score. I had a rule setup to quarantine a device if the CVSS score was 7 or higher (high and critical). ISE quarantined the device if any single QID was scored at a 7 or higher even though Qualys gave the device an overall CVSS score of 5. Is there any way to use the composite score?
- Right now the option profile is tied to the Qualys adaptor definition. There is no way to specify the option profile in the authorization profile. This won’t work in a hospital environment because you can’t VA medical equipment as aggressively as you would a domain joined device. Would be ideal to specify the Option Profile as part of the authorization profile. The other thought we were going to try was to see if we could create multiple Qualys adapter definitions to the same cloud but with different Option Profiles, but that is clunky.
- Qualys has the ability to specify the installation of a dissolvable agent as part of the scan process. That can be done at the Option Profile level or specified as part of the scan request. We don’t have that option in ISE.
- This one may be something I am missing. Is there any option to tell ISE to rescan a device other than deleting the endpoint from ISE and having it authenticate again? Say a device gets quarantined and they fix the issue. The only way I can see to get ISE to issue a new Qualys scan reliably is to delete the endpoint from ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2018 09:05 AM
Under Context Visibility > Endpoints > Vulnerable Endpoints, there is a button "Clear Threats & Vulnerabilities" if the previous data is preventing the re-auth to match the correct authorization policy rule.
I would also suggest to check this report under Operations > Reports > Reports > Threat Centric NAC > Vulnerability Assessment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2018 07:11 PM
As I've posted, the scan are not being triggered even when the right profile is triggered during authorization. So there's nothing on the Context Visibility / Endpoints / Vulnerable Endpoints.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2018 04:44 PM
Since the comments so far not helping resolving your issue, please enable DEBUG, generate a support bundle to include all the debug logs, open a Cisco TAC case, and ask TAC to analyze the log files.
In the past, some of our no-scan occurrences were due to API access limits with our demo account and worked with Qualys support team to address it. Therefore, you might want to check with Qualys and verify your account has proper API access privileges and entitlements, too
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide