- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.4 tries to authenticate domain computer as a domain user
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2019 10:50 PM - edited 08-25-2019 10:30 PM
Hey everyone,
I ran into a weird issue yesterday on a ISE 2.4 patch 8 deployment in which ISE is (for some reason) trying to authenticate a domain computer (which is using EAP-TLS) as a domain user. The computers are configured to only use machine authentication using EAP-TLS as there are no user certificates in this environment.
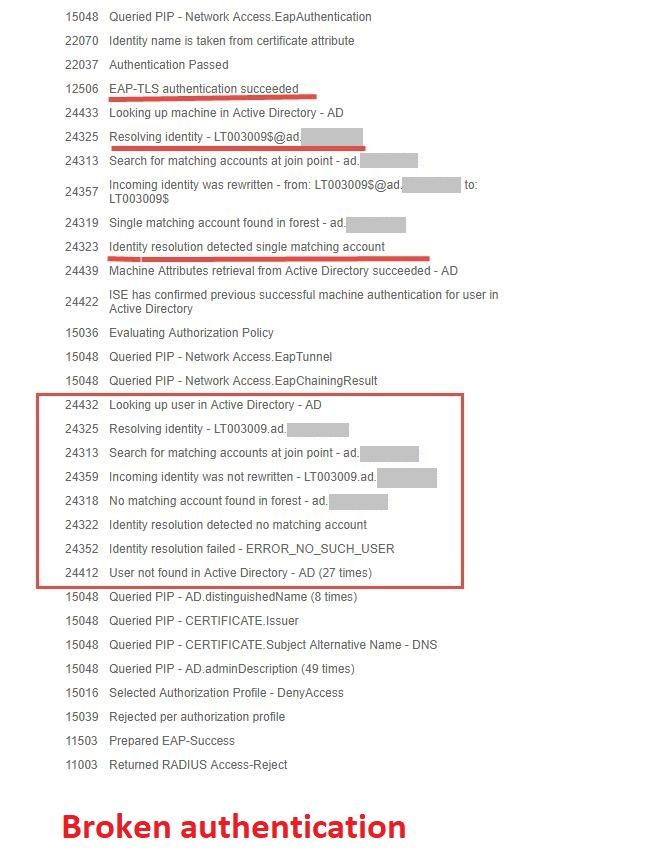
Looking at the detailed log (image below) it seems that ISE authenticates the computer just fine, but it then continues on to look up if the computer name is a domain user. Since there is no domain user with that computer name, ISE tells us the user could not be found and the login attempt is rejected.
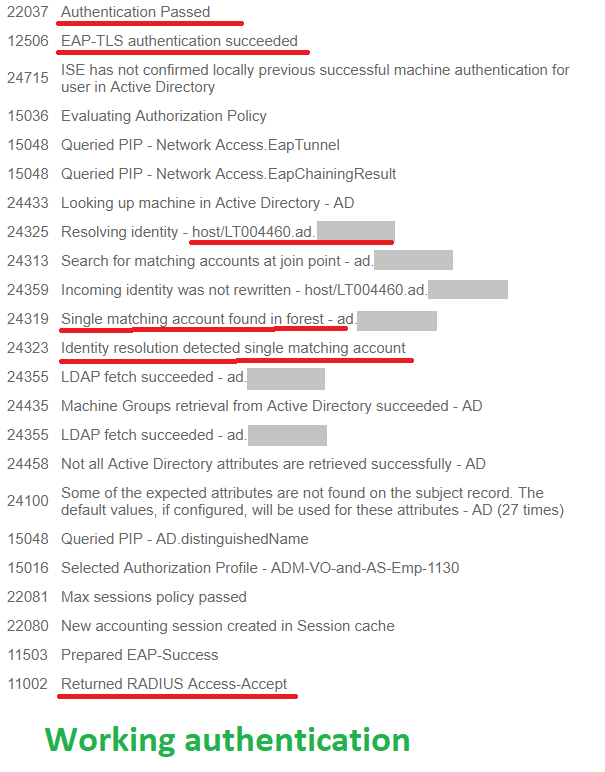
The only differens between the broken machine authentication and a working one is how the username of the machine presents itself in ISE. A machine that goes through a successful authentication shows it's computer's name as host/<computername>.<domain>
The problem only seems to be happening on a few computers (less than 1% of the total computers that are only using machine authentication) but we've yet to find a solution to fix this.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2019 05:53 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2019 03:58 PM
is the AD clean? I mean, are the affected AD accounts looking exactly as they should be? Does the host/identity exist in more than one account attribute? Sometimes ISE has to deal with ambiguity resolution and it's described in a the document below - maybe some hints there
In the interim, you could test how ISE performs its external ID lookups by going to Administration/External ID Sources and then select the AD Joint point, select a server and Test User. Type the combinations of username and host/username to see what the result is.
You may find that you need to perform an Identity Rewrite under Advanced Settings to always prefix the "host/" to the username - but you'd want to perform that re-write only for machine accounts - that might be challenging.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2019 11:40 PM
Thank you Arne for taking a look at this.
I've been doing lookups from inside ISE on several machines that work and comparing them to the non-working one and unfortunately I haven't been able to find anything that looks out of order. The computers' usernames shows up in several attributes in AD, sometimes as host/<computername> and sometimes as <computername>.domain but it all looks the same for every computer.
As the images show, there is an identity rewrite happening in the broken authentication that does not happen in the working authentication. We have never had to resort to identity rewrites before to make things work. I am not sure why the "incoming identity" is different between the broken and working authentications. Unfortunately I cannot make too many changes in this environment as it may affect other production devices.
We have checked and there is no user account with the same name either. This deployment is connected to only a single Active Directory.
I've being trying to wrap my head around this but I simply cannot understand why ISE continues to try to authenticate this computer name as a domain user after it has already says that "a match was found" for the computer name.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2019 12:32 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2019 07:39 AM
Hello ,
Can you share with us authentication rule and authorization rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2019 09:08 PM
Hello,
when you doing a certificate why you not point is to AD because on pictures i see active directory no applicable. Second in authentication rule you can add 1 more row with certificate ou containt your ou than use this cert profile
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2019 05:53 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2020 04:15 PM
For some reason we cannot see the solution to this question. It is very similar to an issue we are seeing. Can some one re-post the solution?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide