- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.6 patch 2 not sending certificate chain to guest portal clients
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 12:46 PM
Good evening.
I have a problem similar to CSCvp75207 - "2.4 P8/P9 Certificate chain does not get imported to Patch 8 and Patch 9"
The ISE appliance (3695) running 2.6.0.156 with patch 1 and 2 doesn't transfer the complete certificate chain to the clients, even though the installed portal certificate was complete with root and intermediate certificates.
I have mapped the root and intermediate certificate trust, but still the complete chain isn't sent.
Anyone using the same platform and has found a working solution?
Sincere Regards
Solved! Go to Solution.
- Labels:
-
Guest
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 05:07 PM
Hi mate,
I have this experience before that the whole chain doesn't work after install of guest cert.
What I did was to reboot the ISE box.
Though guest certs doesn't require you to reload it, it seemed to have worked only after I restarted ISE.
Thanks.
Cheers,
Raffy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2019 05:07 PM
Hi mate,
I have this experience before that the whole chain doesn't work after install of guest cert.
What I did was to reboot the ISE box.
Though guest certs doesn't require you to reload it, it seemed to have worked only after I restarted ISE.
Thanks.
Cheers,
Raffy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2019 05:42 AM
Thanks Raffy.
Very strange. I had started and stopped ISE service, but the trust mappings in the root and intermediate certificate didn't take effect until the servers had been rebooted.
Installing the certificate and rebooting isn't enough. You must check the box for "Trust for certificate based admin authentication" for each root and intermediate certificate before rebooting.
Well If any Cisco Employees read this please note that ISE is affected of the same bug as mentioned in CSCvp75207.
As I understand in release 2.4 a patch 9 is scheduled, and I really hope for a third patch for 2.6 release.
Mapping all these certificate trusts seems to be a strange security implementation...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2019 05:15 AM - edited 09-10-2019 06:09 AM
If anyone is still follows this thread.
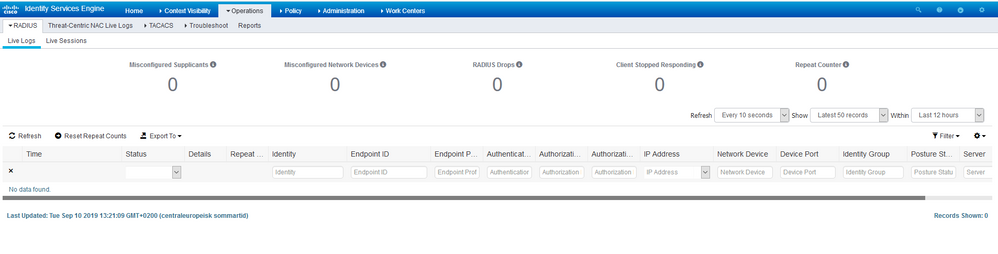
I rebooted the servers last week and everything seemed OK, but suddenly I noticed that the Radius live log and Live sesions are stating "No data found"
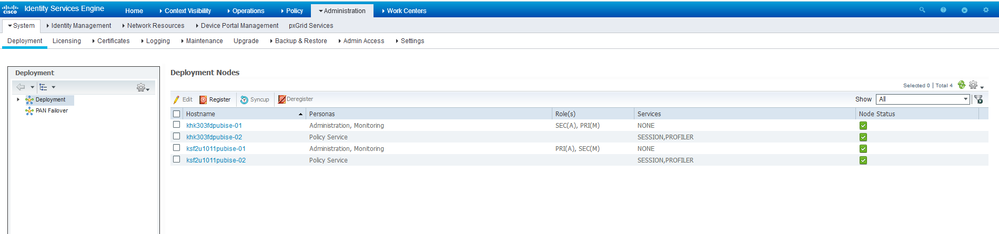
Deployment status is still OK
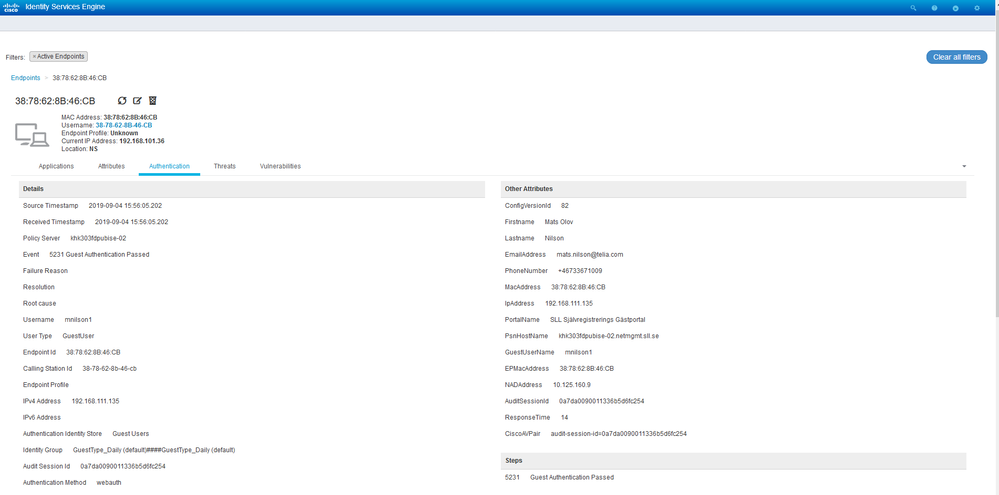
Somehow these logging windows are not presenting any data, but authentication details can be obtained from the Metrics window at the Home screen.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2019 02:24 PM
Hi mate,
that should be a bug right there.
I had similar experience with no live logs back when i was running 2.2
Cisco TAC contacted developers and they had to do root access to ISE vault and somehow cleared the database.
They will provide you the steps on how to generate key for that root access to ISE.
Just raise a high priority case with TAC.
cheers,
Raffy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2019 02:33 PM
Hi mate,
Btw, i remembered they asked me to clear cache on browser.
Relaunch the browser after that.
Also, ISE works best only on mozilla.
See if this works for you.
If not, then try to raise with TAC as I mentioned on my prev post.
cheers,
Raffy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2019 02:20 AM - edited 09-12-2019 08:40 AM
Hi Raffy.
Thanks for your advise, but clearing the cache didn't help a bit.
Actually the page is blank in the data fields until the output "no data available" is shown.
Also I tried anothe browser and another station. Same issue.
- I found this bug on 2.6: CSCvo80516 - ISE 2.6 LiveLogs not seen and false Health Status is Unavailable alarm
I have opened a TAC case for the initial error, but have also found another bug - "Queue Link Error" (CSCvp45528)
I'll post whatever outcome of this TAC case. (opened on monday, but no action yet)
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2019 04:58 AM
Hi @Mats Nilson
I was about to advise a customer to patch their new ISE 2.6 deployment and looks like patch 2 is a bad idea? What I don't understand is why a reboot fixes this issue, since applying a patch will result in a reboot anyway. So it's a reboot after a reboot?
Queue Link error is present in the vanilla version of ISE 2.6 - I regenerated the internal CA store in ISE to try stop that error. I have not checked in recently to see whether it's fixed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2019 06:40 AM
Hi Arne.
I must clarify.
The portal certificate complete with the chain was installed before the both patch 1 and 2.
Reboot didn't solve this issue alone.
I had to mark trust for authentication within ISE for both root and intermediate certificate AND then reboot.
Stopping ISE service didn't help. Only Reboot efter changing trust.
You say regenerating internal CA store should fix the Queue Link Error?
Haven't done that before - do you have any guidelines?
I don't wast to mess up this installation any more than today... ;-)
Sincere Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 11:04 PM
Hi @Mats Nilson
The Queue Link Error was caused due to a bug
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvp45528/?rfs=iqvred
Relating to the internal CA cert. The recommended fix was to re-generate the internal CA structure. Non service impacting, assuming that the ISE does not use internal CA (for BYOD)
It seems to have fixed the issue in my customer's ISE 2.6 (no patch applied).
regards
Arne
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2019 11:43 PM
I would just do it under a change management ticket just in case ;)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2021 10:09 PM
Hi RaffyLingodan,which version of ISE you were using?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2019 12:01 AM
Hello,
I had the same problem, but on VPN with Posture.
The System Scan always failed because ISE did not sent the whole cert chain.
The workaround is to edit each ISE Trust Certificate that is used in the trust chain of an active ISE System Certificate, and check the "Trust for certificate based admin authentication" check box, as it is said in the bug CSCvp75207.
After that i had to reboot the PSN.
Regards,
Norbert
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide