- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE authentication based on the client IP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2023 02:03 PM
Need some advice. We use ISE for authentication for the Cisco anyconnect VPN. The default authentication is to use a Identity store that uses Windows AD for authentication. I want to add an authentication policy based on the client IP address so if the client connecting the VPN has the IP 1.1.1.1, I would do local authentication with a local stored credential.
I checked my radius log and I see that the client IP is in the following fields
- Endpoint Id
- Calling Station Id
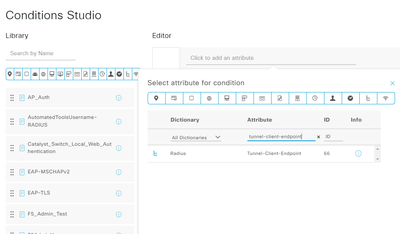
- Tunnel-Client-Endpoint
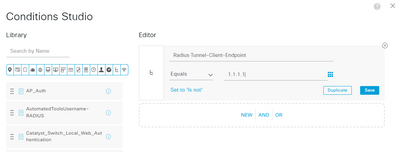
Which one should I use for the condition for the authentication policy? In the condition search, I can't find the first two. The only one I can find is the Tunnel-Client-Endpoint. Should I be using that one? Does my config below look correct? Thanks!
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2023 12:32 PM
The tunnel-endpoint one didn't work... reviewed the radius log and it doesn't match my connection. the calling station ID one works fine though. I think I will stick to that. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2023 07:56 AM
Tunnel-Client-Endpoint should work since that is your RADIUS log. What is your use-case though? Why not just create that account within AD? What happens if the user connecting changes IP addresses or connects from a different location?
Why not use an ID source sequence with AD first and local second? Then add the necessary Authz rules for the local user?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2023 09:16 AM
Thanks Hollifield. I will give it a try today and let you know how it goes.
I guess we could create an AD account for that. I might be just too lazy to engage the AD team for that haha... This is for a probe to monitor the webtop. I have created a static NAT for the probe to always be behind the public IP and no other users will be behind the same IP.
We need the probe because we ran into an issue that the webtop would lose all its shortcuts from time to time. Cisco can't help us because the version we are on is too old and the new version doesn't support the webtop (or something similar). Therefore, I need to figure out a way to log in the webtop and monitor the shortcuts and generate alerts when they are gone.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2023 12:32 PM
The tunnel-endpoint one didn't work... reviewed the radius log and it doesn't match my connection. the calling station ID one works fine though. I think I will stick to that. Thanks!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide