- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE authorization policy for ASA VPN user certificates
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE authorization policy for ASA VPN user certificates
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2020 09:19 AM
Hi
I'm looking at ISE authorization policies for ASA AnyConnect VPN client certificates.
Initially, I tried the following:
- ASA authenticate/validates the AnyConnect VPN client certificate
VPN group is configured to use ISE for authorization and AAA server-group is configured as "authorize-only" - ASA then sends a RADIUS request to ISE with the username attribute set to the cn of the user's certificate and with no password field
- ISE doesn't attempt an authentication for this "authorization-only" request but can authorize - the only attributes that ISE can use for this authorization policy is the username in the request.
I had a look at the method in the thread below that would allow ISE to gather attributes from AD for the user on which to base the authorization policy. This method involves ISE attempting to authenticate the VPN client with a common password set by the ASA - this authentication fails but ISE ignores the failure and uses AD attributes learnt on which to base authorization:
The above method works fine but I was wondering if there was another way of doing this without the failed authentication. Cisco ISE documentation mentions an LDAP User lookup feature which looked useful:
LDAP User Lookup
Cisco ISE supports the user lookup feature with an LDAP server. This feature allows you to search for a user in the LDAP database and retrieve information without authentication. The user lookup process includes the following actions:
Searching the LDAP server for an entry that matches the username in the request
Retrieving a user’s group membership information for use in policies
Retrieving values for specified attributes for use in policies and authorization profiles
I reverted back to the "authorize-only" setup and configured an ldap external identity store on ISE. I tried referencing ldap attributes in the authorization policy but ISE doesn't seem to query ldap when going through the authorization policies. Can the ISE "LDAP User Lookup" feature be used for this scenario?
Thanks
Andy
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-12-2020 09:21 AM
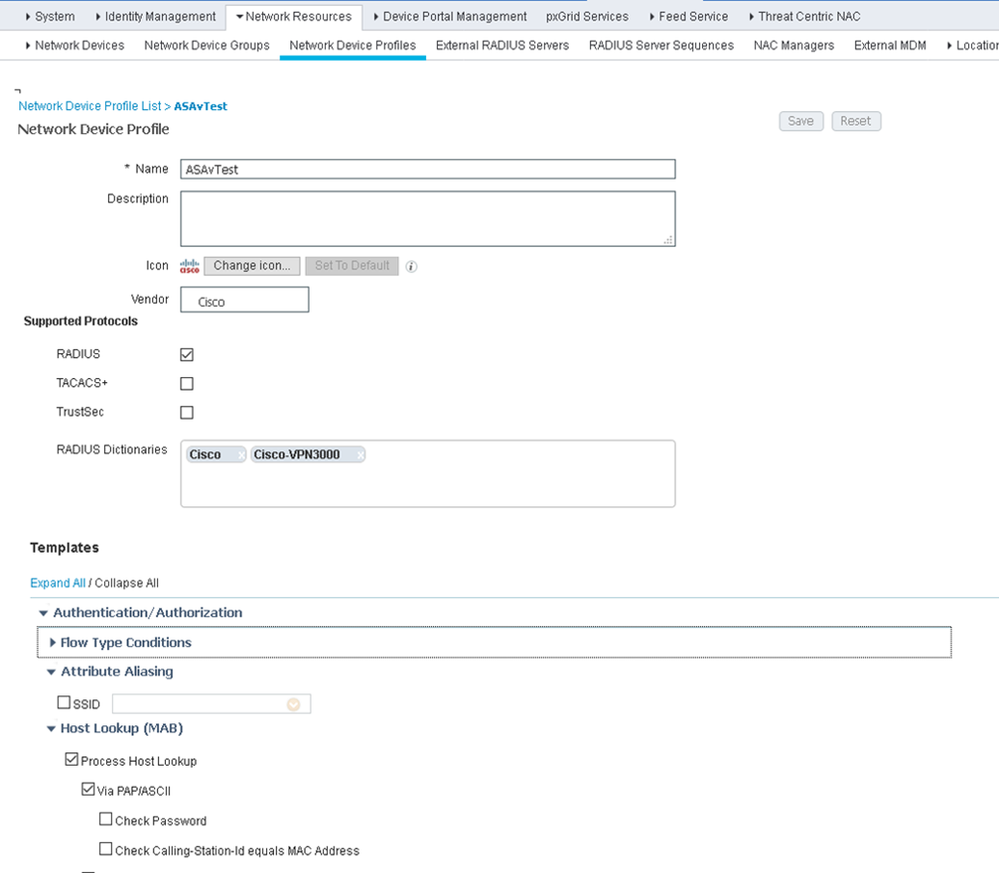
I think I may have resolved this. I created an ISE Network Device Profile and configured it to detect PAP/ASCII requests as a Host Lookup request. I then applied this profile to the ASA's ISE Network Device setup.
With this in place:
- ASA sends "authorization-only" request to ISE with VPN user certificate cn as the username
- ISE treats this request as a lookup and queries ldap - this query returns AD groups on which I can base authorization.
I'm testing this in a dev environment so I've still a bit of testing to do to see what this will impact in the production environment.
Screenshot of Network Device Profile I used is below.
Cheers
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2020 08:52 AM
Applying that modified Network Device Profile to the ASA was a bad idea as it broke the vpn tunnel groups that use username/password as opposed to certificates.
I switched to having different Policy Sets for certifcate and username/password tunnel groups with different "allowed protocols":
- For certificate based tunnel groups, allowed protocols is set to Authentication Bypass - Process Host Lookup
- For Username/password tunnel groups, allowed protocols is set to Authentication - Allow PAP/ASCII
Cheers
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2021 11:24 AM
Hi ANdy
in our 2.1 cube we just use builtin Cisco profile (which differs from yours with few not significant details - SSID, Check Calling-Station* are filled). & that's it. AuthC policy results in user-lookup in AD with AuthZ profile enforced according AD-group membership.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2020 08:24 AM
I don’t understand why you tried to change your initial setup as I think it was perfect with the AuthZ-only request. AuthZ-only requests can be used with AD-group-based authz rules too. Did you have problems with that? If yes, you might have skipped setting up the Certificate Authorization Profile properly. If you need AD lookup (without password), you must choose the domain in the CAP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2020 01:46 AM
Hi
As far as I'm aware, the ISE Certificate Authentication Profile can only be used if ISE is presented with the user certificate (e.g. EAP-TLS). With the VPN setup, the client certificate is presented to the ASA which validates the certificate before sending an authorization request to ISE.
The ASA is still configured to send authz only requests (with a username field derived from a certificate field) to ISE.
ISE would only perform AS/LDAP lookups during authorization if I configured the policy to treat the ASA request as a lookup. Seems to work well so far.
Cheers
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2023 01:59 AM
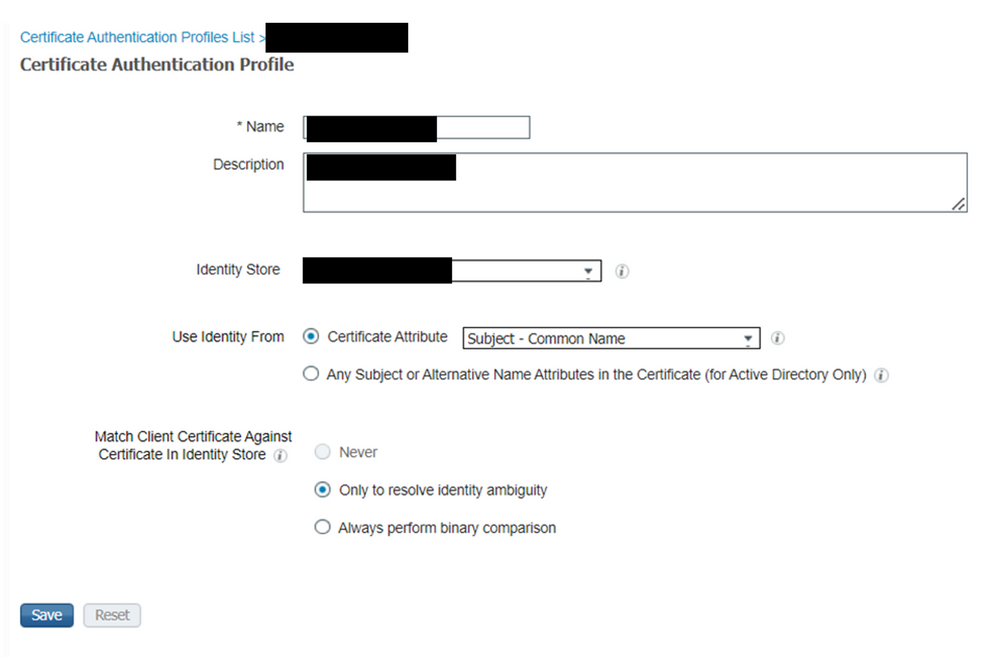
Hi Druv - if you re using "process host lookup" for certificate authorization on ISE, ensure you have a certificate authorization profile configured for your AD - see below for screenshot of profile that I used. (its configured under Administration > Identity Management > External Identity Services > Certificate Authentication Profile). Cisco documentation is here:
hth
Andy
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide