- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE Azure AD Groups
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE Azure AD Groups
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 02:29 AM
We have integrated Cisco ISE with Azure AD (Entra ID) via ROPC. Ise version 3.2 patch 2.
When an Azure AD user logs-in authentication is succesfull.
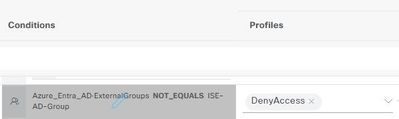
An Authorization policy is used to deny any user who does not belong to particular AD group.
Users are getting denied by this Auth policy even if they belongs to the group.
We changed deny access in Authorization policy to Permit access, still that policy is not being used. ISE picks the next policy.
We checked with all policy conditions - Equals, Contains, In, Not in etc still policy is not working.
Attaching a screenshot of the authorization policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 04:10 AM
Hello manvik,
could you please share the Radius Live Log? There should be something that is incorrectly configured or misspelled.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 04:58 AM
Radius live log says Authorization denied due to the policy screenshot I have attached.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 05:16 AM
Do a test authentication from the external identity store configuration page and see what it returns with respect to user group membership.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 05:19 AM
test authentication works, even for real world scenario authentication to Azure AD works, but Authorization fails when checked against AD groups. Tac has been checking this for a week, no conclusion yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 05:38 AM - edited 01-31-2024 05:39 AM
Did you verify the groups are being returned as expected when you tested authentication? Like shown below:
It can also be an issue if for any reason the group SID changed on the Azure AD (Entra ID) side and ISE did not realize it. In such a case you can have the same group name on both sides but actually not be referring to the same object. In such cases you have to remove and re-add the group in ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 02:26 PM - edited 01-31-2024 02:34 PM
The 'Test User Authentication' is only relevant to traditional AD. The Entra ID integration using RESTID/ROPC, so that tool is not relevant to this use case.
I'm using ISE 3.2p4 in my lab and the RESTID/ROPC flow works as expected with both authorization policies matching on NOT_EQUALS and EQUALS conditions.
Example:
In the detailed logs, I can see both the Monitor and Enabled rule being hit.
If you haven't done so already, I would suggest updating to patch 4 and checking your setup against this guide.
If the 'Test Connection' succeeds and you are able to retrieve the groups and attributes in the REST connection, then it should work. Also make sure that the Username suffix is configured correctly and that you are matching on a Security group type that is not nested (I don't believe ISE supports nested or O365 EntraID groups).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2024 10:17 PM
attached the ISE detailed authentication log. you can see the Authentication works fine and ISE is able to fetch the Group information too.
Traffic flow is Win laptop>Meraki WiFi>ISE>Azure AD
@Marvin Rhoads i think the screenshot you shared is for onprem AD. Anyways i tested the same for Azure AD (ROPC) too. Test connection is successful. As you suggested i deleted and readded groups in ISE, still no luck.
@Greg Gibbs when i tried with Patch 4, authentication was not working with error -"5441 Endpoint started new session while the packet of previous session is being processed. Dropping new session".
Anyways am awaiting TAC response on this. They have collected a ton of logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2024 11:46 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2024 04:53 AM
I think we moved to onprem AD instead of Azure AD.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide