- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE Azure REST/ROPC for Device Admin
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-19-2023 02:20 AM
Hi All,
I have been testing ISE with Azure ROPC for EAP-TTLS and AnyConnect VPN authentication. Both of these work ok. As both of these use-cases support PAP, I'm assuming that it is also supported to use Azure ROPC for RADIUS and TACACS device administration?
I have been doing some testing and RADIUS admin works ok as we can use Azure ROPC for user authentication and then use the Azure AD identity source within an authorisation policy to map Azure AD group to the required authorisation profile (such as Priv15 for switches)
With TACACS, authentication works ok, however there doesn't seem to be an option to select the Azure AD Identity source as a condition within the TACACS authorisation policy so we cant use Azure AD groups for allocating granular command sets/shell profiles.
Has anyone else looked into this?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2023 01:38 PM
Neither the Authentication nor Authorization Policies for Device Admin (TACACS+) currently support REST ID/ROPC Identity Sources or attributes in any shipping version of ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2023 01:38 PM
Neither the Authentication nor Authorization Policies for Device Admin (TACACS+) currently support REST ID/ROPC Identity Sources or attributes in any shipping version of ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2023 06:56 AM
Thanks @Greg Gibbs. I'm assuming that Network/Device Admin with RADIUS is fully supported then?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2023 03:46 PM
That is not a documented use case for ROPC, but both use cases would use simple password-based authentication. The endpoint auth use case would use EAP-TTLS(PAP) and the device admin use case would use simple PAP.
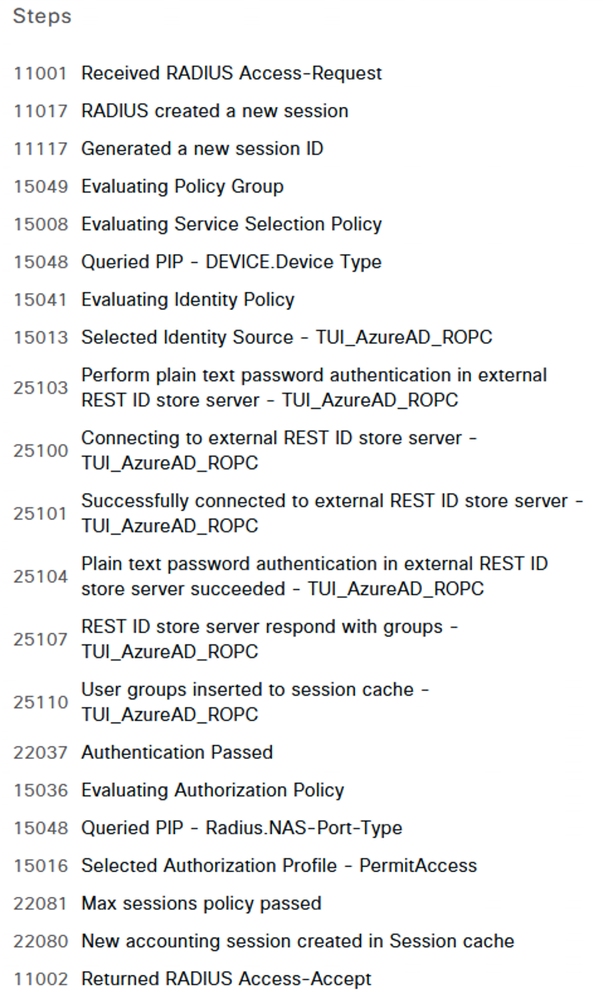
I did a basic test using a CSR1000v configured for RADIUS and authentication using AzureAD via ROPC did work. My authorization policy used a group membership check against AzureAD and the condition matched as expected.
Detailed log:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2025 05:38 AM
Hi Greg
I'm facing this error while trying to perform device administration. Could you please share the document you followed to integrate Azure AD with Cisco ISE via REST ID?(like URL)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2025 03:41 PM
If you're talking about the use case for REST ID / ROPC for RADIUS, it can be found here:
https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/216182-configure-ise-3-0-rest-id-with-azure-act.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2025 10:07 PM
Hello Greg,
Thank you for your reply. The information you provided is helpful, but I am still facing the same issue.
However, the issue does not occur when calling the on-premises AD instead of Azure AD.
If possible, could you please share the document where you tested this in your environment? I have already completed all the configurations provided in the url you previously shared.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2025 06:44 PM - edited 06-01-2025 06:47 PM
There is no source documentation for this and my basic lab testing was over 2 years ago, so I cannot recall much detail on how I tested this.
The first thing you should look at is the fact that the log detail shows 'Username = USERNAME' which means it is invalid. You should enable this setting the Admin > System > Settings > Security Settings page to determine what actual Username ISE is getting.
The Username that ISE sees should be the User Principal Name (UPN) in Entra ID without the '@domain.com' suffix. When ISE sends the Username to Entra ID for Authentication (using ROPC), it will append the Username Suffix you have configured in your REST ID settings. If the full UPN is used for the login (user@domain.com), then the resulting username ISE would send to Entra ID would be 'user@domain.com@domain.com' which would result in an error.
Example:
If all else fails, you might try opening a TAC case to investigate further. As this is not a documented use case, the level of support TAC can provide may be limited.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2024 01:52 PM - edited 06-16-2024 02:02 PM
i'm looking exactly at this use case since we want to move away from On Prem Active Directory due to a merger, among other reasons...
i can authenticate using an identity source sequence referencing REST/ROPC but in the authorization policy i can't select the dictionary.
Our use case is really to authenticate and authorized based on Entra ID membership, and later, using NPS radius proxy, enable 2FA via Entra/Microsoft ...
unfortunately with authorization not working, this is not a viable solution, but it looks like it would be easily supportable .
authentication detailed log
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2024 03:05 PM
@andrea-florio, as I stated in the earlier response...
"Neither the Authentication nor Authorization Policies for Device Admin (TACACS+) currently support REST ID/ROPC Identity Sources or attributes in any shipping version of ISE."
This statement is still true. The example screenshot I shared was when using RADIUS for device admin (which does not use the Device Admin Policy Sets) rather than TACACS+
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2024 12:08 AM
Absolutely, that is clear.
i guess that my post should have been written differently as:
1. even if you said that Authentication for tacacs isn't supported, here are the logs proving that work
2. i am running ise 3.3 path 2 and i wonder if and when such support would be added for authorization
3. is there any alternative that would allow us to use Entra ID users for Device Admin / TACACS+ since we plan to get rid completely of traditional AD?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2024 02:49 PM
Roadmap is not discussed on this public forum.
The only current alternative would be to look into using Entra Domain Services. You would sync your Entra ID user accounts with Entra DS, and ISE would integrate with Entra DS using the same mechanism as traditional AD Domain Services.
I have not had the ability to test it myself, but it should work in theory.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide