- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE BYOD handling of expired or expiring certs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2017 10:35 AM
Hi
I know we have the option since some time back to allow a client whose cert is expired/expiring to the onboarding portal.
I also remember some good slides (ISE techtorial or similar) that described the config to cover for different client OS...
Can anyone point me to those slides?
Regards
Hakan
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2017 11:08 AM
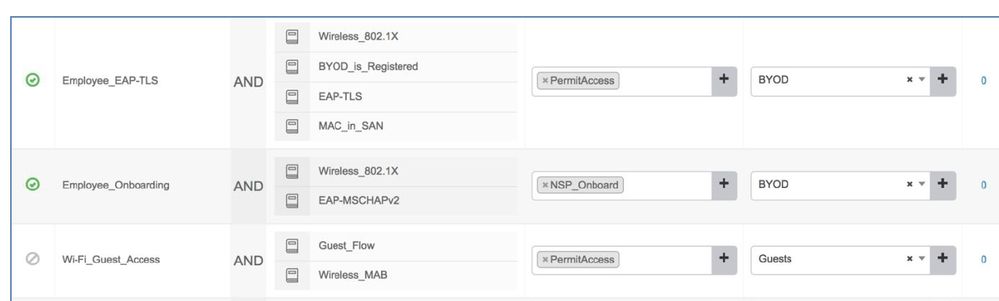
Maybe others can followup regarding the deck, but the configuration is same for any client OS. There is an attribute in the authorization condition called 'CERTIFICATE:Days to Expiry'. With that you can craft an Authorization policy rule that reads, 'If CERTIFICATE:Days to Expiry is less than 15 days, then assign BYOD flow' which forces user to go through the BYOD process again. Now if the certificate already expired, then the endpoint will not be able to associate to the secured WLAN as ISE will deny access due to invalid certificate, to cover that scenario, you can allow dual-SSID BYOD flow in the guest WLAN and force them through BYOD flow when employee user logs into the guest portal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2018 11:53 PM
Arne, actually you caught my error there. You should create a CWA portal that forces BYOD for employees instead of BYOD portal and use it during expired certificate flow on 802.1X WLAN. Quick step here:
1. Create CWA portal that forces employee to go through BYOD (You can reuse existing one if present already)
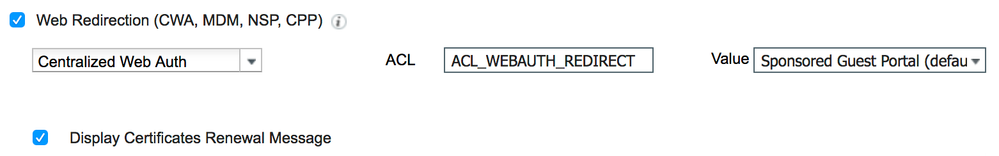
2. Create AuthZ profile for CWA, make sure to check 'Display Certificates Renewal Message' option
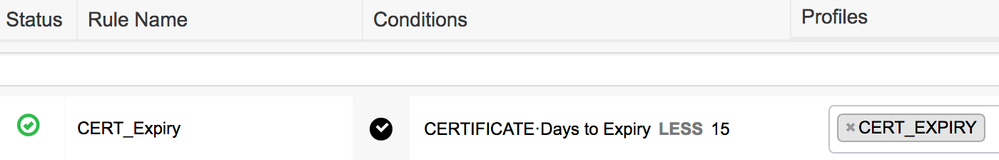
3. Create policy that gets matched for 802.1X WLAN that user connects to using the certificate as following: "If CERTIFICATE:Days to Expiry LESS X" then assign the AuthZ profile created above
Now, when the user connects to the 802.1X WLAN with the certificate nearing expiry, the user will get redirected per policy you created, and due to the 'Display Certificates Renewal Message' option used in the AuthZ profile, ISE will append 'daysToExpiry=Y' parameter at the end of the URL redirect string as shown below:
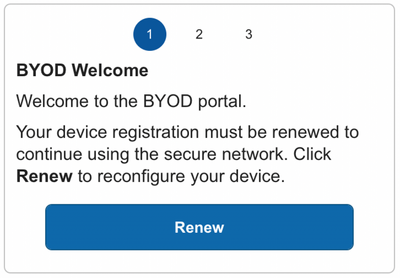
User will be forced to login to the portal and then the BYOD renewal process will start. Instead of seeing 'Start' button, user will see 'Renewal' button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2017 11:08 AM
Maybe others can followup regarding the deck, but the configuration is same for any client OS. There is an attribute in the authorization condition called 'CERTIFICATE:Days to Expiry'. With that you can craft an Authorization policy rule that reads, 'If CERTIFICATE:Days to Expiry is less than 15 days, then assign BYOD flow' which forces user to go through the BYOD process again. Now if the certificate already expired, then the endpoint will not be able to associate to the secured WLAN as ISE will deny access due to invalid certificate, to cover that scenario, you can allow dual-SSID BYOD flow in the guest WLAN and force them through BYOD flow when employee user logs into the guest portal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2017 11:19 AM
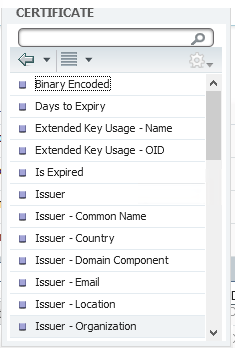
Here is the screenshot of what is supported as part of CERTIFICATE attribute that you can add as part of authorization condition in the authorization policy under BYOD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2018 09:59 PM
Hi @howon
I have ISE 2.4 patch 3 and I am testing what happens when a BYOD user is authenticated with a client cert that is about to expire.
I catch that condition in Authorization Policy, and I use an Authorization Profile as follows
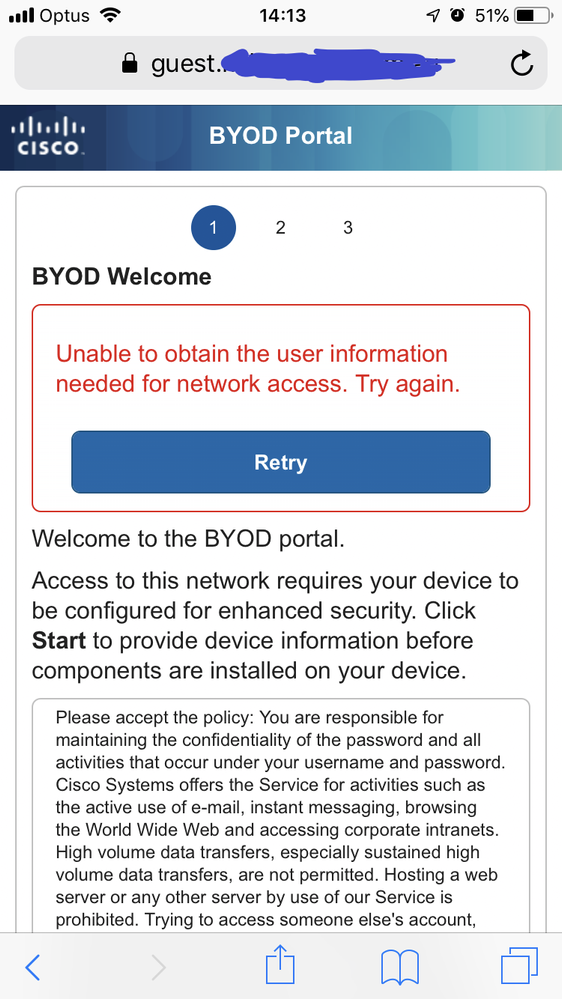
Web Redirection = Native Supplicant Provisioning
On the client, I can get redirected and I see the following screen - the error seems to make sense - how does ISE know the user's identity, when they immediately get redirected to the NSP Portal without any authentication?
When I initially on boarded this user, I did it via Guest Portal - and there I can of course authenticate the user. How does it work if I redirect directly to the NSP BYOD portal?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2018 11:53 PM
Arne, actually you caught my error there. You should create a CWA portal that forces BYOD for employees instead of BYOD portal and use it during expired certificate flow on 802.1X WLAN. Quick step here:
1. Create CWA portal that forces employee to go through BYOD (You can reuse existing one if present already)
2. Create AuthZ profile for CWA, make sure to check 'Display Certificates Renewal Message' option
3. Create policy that gets matched for 802.1X WLAN that user connects to using the certificate as following: "If CERTIFICATE:Days to Expiry LESS X" then assign the AuthZ profile created above
Now, when the user connects to the 802.1X WLAN with the certificate nearing expiry, the user will get redirected per policy you created, and due to the 'Display Certificates Renewal Message' option used in the AuthZ profile, ISE will append 'daysToExpiry=Y' parameter at the end of the URL redirect string as shown below:
User will be forced to login to the portal and then the BYOD renewal process will start. Instead of seeing 'Start' button, user will see 'Renewal' button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2018 11:01 AM
Is there an update on this issue?
Is the only way to renew a BYOD certificate is through CWA?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2018 11:03 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2018 11:11 AM
no other way to renew without redoing the onbooarding process?
no difference in dual or single SSID?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2018 11:41 AM
Page 36 - https://community.cisco.com/t5/security-documents/cisco-ise-byod-deployment-guide/ta-p/3641867
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2018 02:02 PM
And with this setup (single SSID):
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 12:54 PM
After a few thoughts and tries, I think my question was not really understandable. In this scenario, i think the renouncement is also done by CWA !?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2018 01:06 PM
We force CWA as we need to confirm the user credential for the re-issuance of certificate. This is a way of making sure the user is indeed the user who was issued the certificate. Without this, any user who has access to the certificate pair would be able to gain access indefinitely. If this is not desired, then recommend extending the validity date.
With your policy, when the certificate expires, user will be denied access to the secure SSID unless ISE is configured to allow expired certificates. If you want to allow renewal flow then follow my example above where you are forcing CWA for secured SSID. Alternatively, user can connect to open/guest SSID to renew certificate provided that BYOD is enabled on open/guest SSID flow.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide