- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE Compliant Users - Can't access internal resources using HTTPs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2022 02:47 AM
Dears,
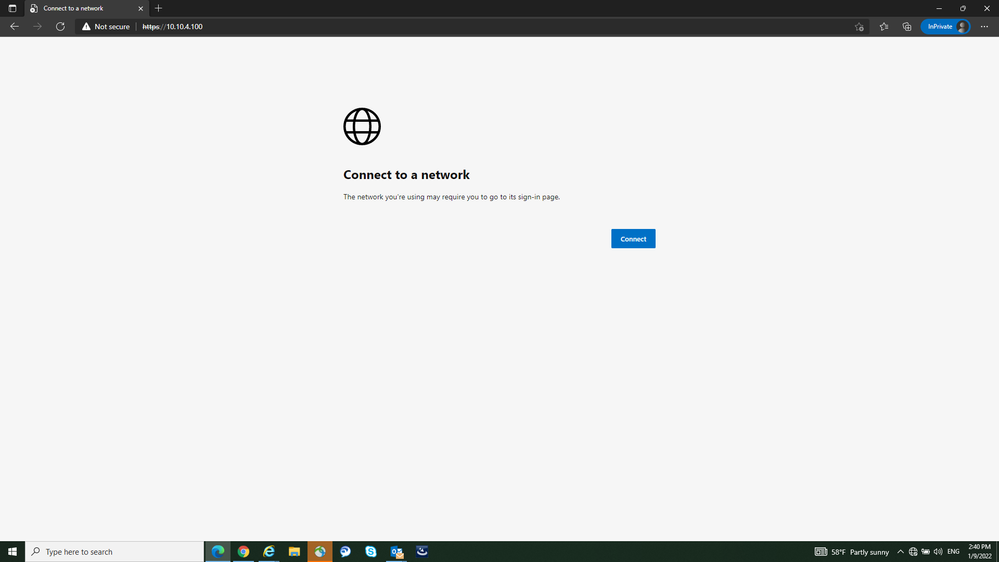
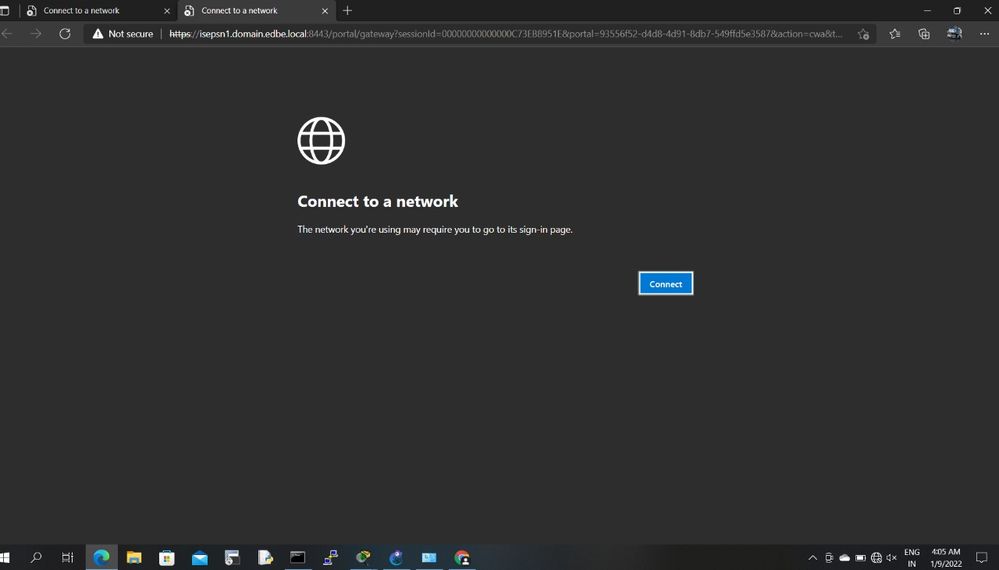
We have a new deployment of ISE, when users put in compliant state, the internet working normally, but when trying to accessing internal resources using HTTPs, the browser rather than displays certification warning and let users to continue, it displays the below page
"the network you 're using may require you to go to sign-in page"
when I press to connect button, it redirects may to page Like gstatic.com (in Chrome) and edge.microsoft (in Edge).
the issue happens with Edge and Chrome browsers only, internet explorer working fine.
Any HTTPs application that trusted to chrome or Edge, its working fine, but the issue is when the certificate is untrusted for the browser, it not displays the certification warning.
in addition to its happens with Compliant Users and Guest Portal.
We are using ISE 3.0 and Anyconnect supplicant 4.10
how can We resolve that issue ?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2022 02:04 PM
Hi
Is this for a Cisco switch?
Its sounds like there is still some URL redirection happening, because the switch is being instructed to do so.
It would be helpful to know what the config looks like on that port (see commands below) and also what the Authorization Profile looks like that ISE sends in the case of a "compliant" user session.
show derived-config interface gig x/y/z show access-session interface gig x/y/z detail
On switch ports there are three types of ACL that are at play (from what I have discovered)
- inherent ACL (at least a basic ACL to allow DHCP - ACL is configured on the interface)
- dACL (downloaded from ISE) used to allow/block user traffic
- redirection ACL (used to determine what will trigger a http interception/redirection)
I am not sure about the precedence of which ACL is processed in what order - but be aware that there is more than one ACL at play!
Good starting point for wired NAC is this guide.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2022 02:04 PM
Hi
Is this for a Cisco switch?
Its sounds like there is still some URL redirection happening, because the switch is being instructed to do so.
It would be helpful to know what the config looks like on that port (see commands below) and also what the Authorization Profile looks like that ISE sends in the case of a "compliant" user session.
show derived-config interface gig x/y/z show access-session interface gig x/y/z detail
On switch ports there are three types of ACL that are at play (from what I have discovered)
- inherent ACL (at least a basic ACL to allow DHCP - ACL is configured on the interface)
- dACL (downloaded from ISE) used to allow/block user traffic
- redirection ACL (used to determine what will trigger a http interception/redirection)
I am not sure about the precedence of which ACL is processed in what order - but be aware that there is more than one ACL at play!
Good starting point for wired NAC is this guide.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2022 08:00 AM
Hi Arne,
DACL for compliant users is "permit ip any any"
the below is port configuration
interface g1/0/1
ip access-group ACL_Default in
authentication event fail action next-method
authentication host-mode multi-auth
authentication open
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
authentication timer reauthenticate server
mab
snmp trap mac-notification change added
snmp trap mac-notification change removed
dot1x pae authenticator
dot1x timeout tx-period 10
spanning-tree portfast
spanning-tree bpduguard enable
We removed 443 redirection from redirection ACL, but the issue is the same
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2022 01:57 PM
Does your switch have the global config command to enable URL redirection?
ip http server
This must be there to allow the switch to intercept the HTTP traffic (URL redirection).
If you're concerned about securing the switch's web interface then you need to add the commands - below will disable TCP/80 and TCP/443 web access to the switch's web services
ip http active-session-modules none ip http secure-active-session-modules none
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2022 02:36 PM
Hi Arne,
yes, the switch is configured with ip http server
I disabled HTTPs as I thought that it is caused the issue, but after disabling it the issue still exist.
could you please help to solve this issue as a lot of users are suffering
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2022 02:58 PM
Need more details. When you have such a situation, have you looked at the session details on the switch? e.g. when the user gets this page, you need to check (using gig 1/0/1 as an example)
show access-session int gig 1/0/1 detail
Then also, verify the state of all ACLs applied. There is an ACL on the gig 1/0/1, and also, ISE is sending back a dACL - this is a dynamic ACL whose name changes all the time - you can get the exact name of the dACL from the access-session details
show ip access-list int gi 1/0/1 show ip access-list xxxxxxxxx<dACL_Name>xxxxxxx
Then, other basic checks to be performed on the workstation that is suffering - go to command line and check whether users can resolve the portal using DNS - and if you have telnet installed, see what is returned when you try a TCP connection to 443 and 8443 (ISE should re-direct your 443 to 8443)
nslookup isepsn1.domain.edbe.local telnet isepsn1.domain.edbe.local 443
telnet isepsn1.domain.edbe.local 8443
DNS must work. If it doesn't then investigate that first.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2022 05:47 PM
If users are suffering, then this is an urgent issue and you should contact TAC to investigate and help you resolve the issue.
This Community forum is not TAC and is not suited for this type of urgent support need or troubleshooting complex issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2022 11:20 AM
using any proxy for SSL interception/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2022 07:57 AM
We have 6 ISE nodes, 2 nodes are PAN and 4 nodes are PSNs.
we use the below redirection ACL, we removed 443 redirection, but the issue still occurs.
ip access-list extended ACL_REDIRECT
deny udp any eq bootpc any eq bootps
deny udp any any eq domain
deny ip any host <ISE-IP>
permit tcp any any eq www
deny ip any any log
exit
We have Proxy, but HTTPs internal resources are bypassed from proxy.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide