- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE dotx1 - Outlook Security Alert(Untrusted Server Certificate)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2017 01:46 AM - edited 02-21-2020 10:38 AM
Hello Everyone,
We are integrating Cisco ISE in new environment to use radius AAA Services (dot1x, MAB...).
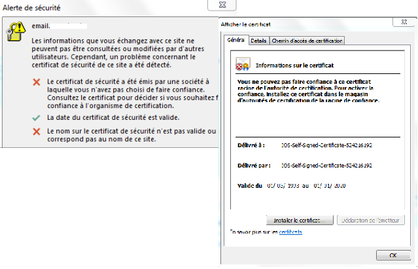
When we connect a windows domain machine to the network on a dot1x port, an Outlook Security Alert "Untrusted Server Certificate" appears. We have looked at the certificate we found the Self Signed Certificate of the switch on which we are connected.
Here some screenshots of the certificate error
Can you help me to know the root cause of this security alert and why the outlook is showing the Self Signed Certificate of the switch ?
Thanks
Anis GHARBI
Solved! Go to Solution.
- Labels:
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2017 02:55 AM
Yes, posture redirect could cause the same issue. One way of fixing this would be to modify your redirection ACL to exclude Outlook traffic from being redirected, if acceptable.
Not related to this issue, but I would suggest not to use local webauth (that third option in "authentication priority dot1x mab webauth" command), that is the old way of doing things. If you can use central webauth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2017 02:27 AM
This is probably because your endpoint is hitting Guest webauth redirection rule and confusing Outlook. What is the output of the show authentication sessions int <interface> detail when the issue happens? What are your port configs and ISE policies?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2017 02:34 AM
Yes we have webauth redirection configured on the switch port to redirect guests to captive portal as a third auth method.
Here the port config:
interface FastEthernet0/8
description dot1X/mab test port
switchport mode access
authentication event fail action next-method
authentication host-mode multi-domain
authentication open
authentication order dot1x mab webauth
authentication priority dot1x mab webauth
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication timer inactivity server
authentication violation restrict
mab
dot1x pae authenticator
dot1x timeout tx-period 10
spanning-tree portfast
spanning-tree bpduguard enable
!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2017 02:42 AM - edited 11-09-2017 02:47 AM
At the phase of 802.1x authentication and authorization the employees are redirected to the web posture portal to check the compliance. I think for that reason the there a redirection of the web traffic from Microsoft outlook to the Exchange server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2017 02:55 AM
Yes, posture redirect could cause the same issue. One way of fixing this would be to modify your redirection ACL to exclude Outlook traffic from being redirected, if acceptable.
Not related to this issue, but I would suggest not to use local webauth (that third option in "authentication priority dot1x mab webauth" command), that is the old way of doing things. If you can use central webauth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2018 05:54 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2018 10:53 AM
Hello,
have you found a solution how to prevent outlook 365 traffic to be redirected to ISE?
thanks,
Neil
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2018 07:45 AM
HI Dear,
can you please let me know how to make changes on posture rule?
i am having same issue and tried to allow mailserver IP address on posture but still same issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2018 05:52 AM
Cisco does not have an answer to this particular issue when an organization uses Office 365 since external Microsoft IP addresses and URLs are constantly evolving.
The workaround that was decided on for the enterprise I am working on was to only redirect traffic to the portal when a user attempts to access an internal website. The redirect ACL only includes the internal website address range and the dynamic ACL from ISE blocks external traffic until authenticated. This will prevent the Outlook certificate issue from occurring. This is far from ideal, but Cisco has yet to provide any information on a permanent fix to this issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2018 07:05 AM
Thanks for your reply
i dont have office 365. i do have exchange server on premises.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2018 07:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2018 07:13 AM
i do have ISE-Redirect ACL which is deny for bootpc , domain and ISE and allow for www and 443 then deny everything and i did allow exchange server on this list. the dynamic ip access list where i am confused.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide