- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE Guest Flow with Multiple Endpoint Identities
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2016 10:19 AM
Customer has guest wireless controlled via ISE. Employees are allowed to use the guest wireless with their personal devices when they log in through active directory. Once the employee logs in via the portal page, they are registering the device so the system does a MAB on the second and subsequent logins for that device. What they are asking is to be able put certain users in separate identity groups. This is to be able to purge the registered devices at specific intervals. For example, Executives would log in one time and not have to enter credentials again for 365 days (after the device is purged). Employees would log in from the guest portal and their device would be purged out after 30 days. In the guest portal and byod portals it only shows 1 identity group to assign the user. Can I assign more then one identity group in a guest flow? I think what I am looking for is DRW with multiple identity groups.
Is there another way to be able to assign guest users to different policies and then purge them at a specific interval?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2016 10:26 AM
Since both of these type of users are in the same Identity store and considered employees to the guest portal thank I think you could do it the following way.
This would assume you have an AD group for execs vs employees or perhaps LDAP attribute?
- Create endpoint groups for employees and another for execs. Purging policy as needed.
- Create a hotspot portal for employee devices and another for executives and choose the corresponding endpoint groups.
- Setup authorization rule above the standard redirect rule to say if guest flow and employees then redirect to employee hotspot portal. Make another rule above that for Executives group.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2016 10:26 AM
Since both of these type of users are in the same Identity store and considered employees to the guest portal thank I think you could do it the following way.
This would assume you have an AD group for execs vs employees or perhaps LDAP attribute?
- Create endpoint groups for employees and another for execs. Purging policy as needed.
- Create a hotspot portal for employee devices and another for executives and choose the corresponding endpoint groups.
- Setup authorization rule above the standard redirect rule to say if guest flow and employees then redirect to employee hotspot portal. Make another rule above that for Executives group.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2016 10:07 AM
Followed your instructions below. I have three rules plus the CWA. Hotspot 1, Hotspot 2 and a Guest Access depending on the Hotspot assigned identity.
I've enabled the policy - user hits CWA then is redirected to appropriate Hotspot portal. The hotspot portal is set up to put the endpoint in a specific endpoint identity. Flow goes through hotspot but the endpoint assignment does not happen. The endpoint identity stays as Unknown and I loop back to CWA.
What am I missing ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2016 10:27 AM
What version of ise ?
I have heard something similar where endpoint is not being registered into group
Is regular hotspot working?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2016 10:36 AM
ISE 2.0 no patch. Will have to test regular hotspot functionality.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2016 10:42 AM
I know there was a problem with ISE 2.0 with no patch not registering correctly
Can you apply latest patch and then make sure you are sending to an AUP page where they have to hit accept?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2016 04:15 AM
Upgrading to 2.0.1.130 seems to have fixed the issue.
Thanks.
Sam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2016 01:41 PM
This is a very interesting setup. Could you share a quick screen capture of your Auth policies? I am looking at applying the same method.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2016 12:03 PM
scamarda can you share
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2016 02:16 PM
Usernames are loaded in AD. Originally the use CWA. The different AD user types are directed to their respective hotspot portal. Once they hit the portal there are assigned a unique identity. There is an AUP in between CWA and the Hotspot. Other than that, not interaction. The identities are defined with different purge times.
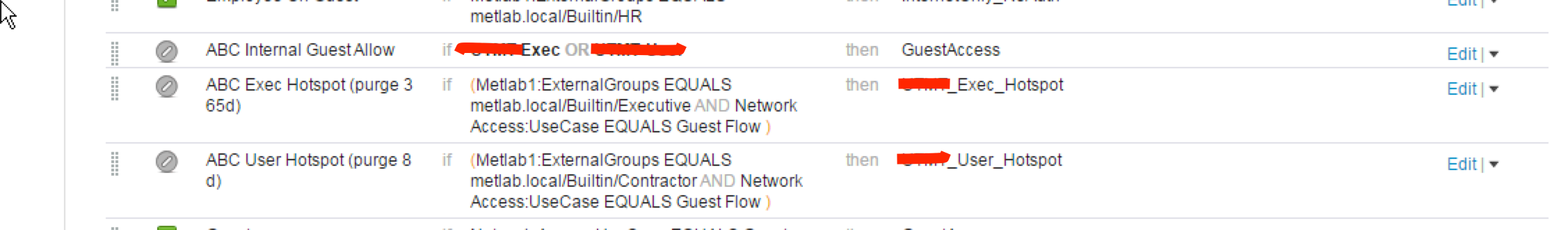
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2016 02:23 PM
ok assuming you have authz rules above that with the different endpoint groups
if executiveEndpoint then permitExecutive permissions
if UserEndpoint then permitUser permissions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2016 02:29 PM
This was on the guest network so no permission differences. Customer wanted to have execs renew AUP every 365 days and Employees using the Guest Wifi every 8 days. Needed a way to purge devices that were using the Guest WiFi. Once purged, AUP was redisplayed. Also a way to clean up the DB clutter.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2016 12:42 PM
Thanks for sharing! I am working on setting up the same scenario for a customer as well. We are now trying to configure identity mapping to identify the users on these open connections.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

