- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE intune integration question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2019 06:21 AM
Hi,
I would like to integrate ISE into intune and will be following the following guide:
We have a 2 node cluster setup and the guide indicates you have to use the default self-signed server certificate.
What do you have to do for adding the 2 node ?
Just add the values to the keyfile?
"keyCredentials": [
{
“customKeyIdentifier“: “$base64Thumbprint_from_ISENODE1”,
“keyId“: “$keyid_from_above“,
"type": "AsymmetricX509Cert",
"usage": "Verify",
"value": "Base64 Encoded String of ISE PAN cert"
}
{
“customKeyIdentifier“: “$base64Thumbprint_from_ISENODE2”,
“keyId“: “$keyid_from_above“,
"type": "AsymmetricX509Cert",
"usage": "Verify",
"value": "Base64 Encoded String of ISE PAN cert"
}
]
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2020 07:01 PM
Hi Fred,
Your efforts have been the most helpful, as you stated the Azure Portal has changed considerably from any official documentation.
I have just managed to pull the integration together with the help of many articles So I thought I might put my procedure up as I have to do this again in production.
I also hope it helps others.
Disclaimer, I have not actively tested that this works with an ISE authorization or authentication policy and additional permissions and policies may have to be added.
***** Install the Azure Certificate into ISE *****
Download the Baltimore Certificate from https://portal.azure.com
Click the Padlock Icon on address bar
Click Certificate (valid)
Change to Certification Path Tab
Select the Baltimore Certificate
Click View Certificate
Change to the Details Tab
Click Copy to File...
Save the Certificate and close all Certificate windows.
login to ISE Portal
Navigate to Administration -> System -> Certificate
Navigate to Trusted Certificates
Import the Downloaded Baltimore Certificates
Proceed through the SHA1 Warning and Duplicate warning to complete the install.
***** Generate ISE Key for upload to Azure *****
Login to ISE Portal
Navigate to Administration -> System -> Certificates
Navigate to System Certificates
Select the Default Self Signed or other Signed Certificate
Export the certificate
***** Generate and record the base64 Certificate details *****
Open Powershell ISE
Add the following power command to the script pane:-
$certpath = "<<Path to certificate>>"
$cer = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2
$cer.Import("$certpath")
$bin = $cer.GetRawCertData()
$base64Value = [System.Convert]::ToBase64String($bin)
$bin = $cer.GetCertHash()
$base64Thumbprint = [System.Convert]::ToBase64String($bin)
$keyid = [System.Guid]::NewGuid().ToString()
"KeyThumbprint: $base64Thumbprint" | Out-Host
"keyID: $keyid" | Out-Host
"keyValue: $base64Value" | Out-HostReplace <<path to certificate>> with you certificate and path like C:\Certs\ISE.cer
Record the KeyThumbprint, KeyID and KeyValue
Note: when used the keyValue need to be on a single line without line breaks.
***** Create New Azure Application *****
Login to Azure
Navigate to Azure Active Directory
Navigate to App registrations
Add New Registration
Name: ISE
Supported Account types: Single Tenant
Redirect URI: Web
URI: "blank"
***** Upload ISE Certificates into ISE Application *****
Navigate to Azure Active Directory
Navigate to App registrations
Select ISE Application
Navigate to Manifest
Download Manifest (Do not rename)
Modify Line:
From:
"keyCredentials": [],
To:
"keyCredentials": [
{
"customKeyIdentifier": "<<KeyThumbprint>>",
"keyId": "<<KeyID>>",
"type": "AsymmetricX509Cert",
"usage": "Verify",
"value": "<<KeyValue>>"
}
],Replace <<KeyThumbprint>> with ISE Certificate KeyThumbprint recorded earlier
Replace <<KeyID>> with ISE Certificate KeyID recorded earlier
Replace <<KeyValuet>> with ISE Certificate KeyValue recorded earlier
If a 2nd Certificate is needed download and obtain the base64 values and modify the Manifest file with an additional customKeyIdentifier
"keyCredentials": [
{
"customKeyIdentifier": "<<KeyThumbprint1>>",
"keyId": "<<KeyID1>>",
"type": "AsymmetricX509Cert",
"usage": "Verify",
"value": "<<KeyValue1>>"
},
{
"customKeyIdentifier": "<<KeyThumbprint2>>",
"keyId": "<<KeyID2>>",
"type": "AsymmetricX509Cert",
"usage": "Verify",
"value": "<<KeyValue2>>"
}
],Finally Upload New Manifest File to ISE App
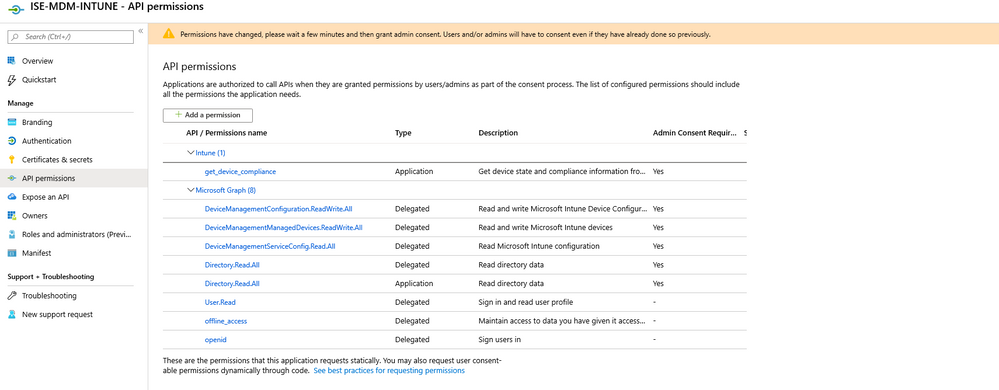
***** Configure Azure Permissions *****
Navigate to Azure Active Directory
Navigate to App registrations
Select ISE Application
Navigate to API Permissions
Remove existing - Microsoft Graph - Delegated - User.Read
Add the Following Permissions
Microsoft Graph
Delegated
offline_access - Maintain access to data you have given it access to
openid - View users basic profile
Application
Directory.Read.All - Read directory data
Intune
Application
get_device_compliance - Get device state and compliance information from Microsoft Intune
Grant admin consent if required.
***** Record Required Values for ISE *****
Navigate to Azure Active Directory
Navigate to App registrations
Select ISE Application
Navigate to Overview
Record Values for Application (client) ID:
Select Endpoints
Copy Values for:
Microsoft Graph API endpoint:
OAuth 2.0 token endpoint (v1):
***** Create External MDM In ISE *****
Login to ISE Portal
Navigate to Administration -> Network Resources -> External MDM
Add New MDM Server
Name: Azure_Intune_MDM
Server Type: Mobile Device Manager
Authentication Type: OAuth - Client Credentials
Auto Discovery: Yes
Auto Discovery URL: Use the Value from Microsoft Graph API endpoint
Client ID: Use the Value from the Application (client) ID
Token Issuing URL: Use the value from the OAuth 2.0 token endpoint (v1)
Token Audience: Leave at default (prepopulated - https://api.manage.microsoft.com/)
Description: Azure Intune MDM
Polling Interval: 240
Time Interval for Compliance Device ReAuth Query: 1
Status: Enabled
Notes: Microsoft Graph API endpoint may need to be adjusted if not working with recorded value.
Use https://graph.windows.net/<<tenant-id>>
<<tenant-id>> can be found on OAuth 2.0 token endpoint (v1) URL
https://login.microsoftonline.com/<<tenant-id>>/oauth2/token
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2019 07:41 PM
Please review the info at ISE MDM integration with Azure/Intune
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2019 03:28 AM - edited 11-09-2019 03:30 AM
Hi,
Tnx for the update, the certificate I have covered now.
Is there an update version of the ISE integration guide, the microsoft portal has completely changed and I don't seem to find the correct permissions I need to assign.
The official documentation doesn't include this:
Kind regards
Frederik.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2019 08:46 AM
I will check with our team. Please also check with your MS Intune support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2019 08:47 AM
Tnx I will check with microsoft intune also.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2019 07:52 AM
Our DE team asking which API permissions not seen in the Azure portal.
DE said we had no a new list for this. The main permissions are:
· Read Microsoft Intune Device Configuration and Policies
· Read Microsoft Intune Configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2019 11:29 PM - edited 11-12-2019 11:50 PM
Hi Hslai,
Following the guide on TechNet post:
I mapped the permission to the new ones using:
https://docs.microsoft.com/en-us/graph/permissions-reference
Can you confirm this is all that I need? Or do I need less. In the TechNet article they are talking about the Azure Active Directory API but this has been discontinued I believe and now integrated in the Graph API.
Would be good to have exact instructions inside the general Admin Guide of ISE , the admin guide doesn't even talk about permissions or did I mis something.
Also the admin guide states the following:
ISE MDM Support for Microsoft Intune and SCCM
Microsoft Intune- MDM-ISE supports Microsoft's Intune device management as a partner MDM server managing mobile devices.
You configure ISE as an OAuth 2.0 client application on the Intune server managing mobile devices. ISE gets a token from Azure to establish a session with that ISE Intune application.
See https://msdn.microsoft.com/en-us/library/azure/dn645543.aspx for more information about how Intune communicates with a client application.
Desktop Device Manager (Microsoft SCCM) - ISE supports Microsoft's System Center Configuration Manager (SCCM) as a partner MDM server for managing Windows computers. ISE retrieves compliance information from the SCCM server using WMI, and uses that information to grant or deny network access to the user's Windows device.
In my situation we are running Co-Management solution so intune and SSCM. Can I read the compliancy status of windows 10 devices using only intune?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 03:22 AM
Hi Hslai,
I have not heard back from you: I am still not able to add Intune as MDM server.
First I got an error about unable to connect I had to add the Microsoft IT TLS CA1 to the trusted certificate:
After doing this I got the error:
Failed to acquire auth token from Azure AD. Error validating credentials. Client assertion contains an invalid signature. [Reason - The key was not found., Thumbprint of key used by client: 'AC33728EAE517ECCEFEIJFE7CE49298538F8E66F1C5CAD',
Configured keys: [Key0:Start=09/21/2016, End=09/21/2017, Thumbprint=7DF7384DEFE7FDB62123310C1DAE2A9563
5016513A;]] Check if either ISE certificates not being uploaded or problem with certificates already uploaded to App on Azure A
My ise was no using the default self signed certificate to connect. so i exported all certifiates and found the thumprint.
After fixing this i am nog getting the following error:
sun.security.validator.ValidatorException:
PKIX path building failed: sun.security.provider.certpath.SunCertPathB
uilderException: unable to find valid certification path to requested target
What am i doing wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 04:14 AM
So it seems like I was till missing certificates from Microsoft, did a pcap and extracted the certificate info from there.
The certificates is was missing.
Microsoft IT TLS CA 1
Microsoft IT TLS CA 2
Microsoft IT TLS CA 5
After importing this I got a new error message :)
I had to change the graph.microsoft.com to graph .net
so I have the following now in MDM
Auto discovery URL: https://graph.windows.net/tenant-id
Client ID : Application ID from Azure
Token issueing URL: https://login.microsoftonline.com/tenant-id/oauth2/token
Now my connection to ISE intune is valid. I will post a full manual on what I did if I have some time.
Really bad documentation on this integration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2020 07:01 PM
Hi Fred,
Your efforts have been the most helpful, as you stated the Azure Portal has changed considerably from any official documentation.
I have just managed to pull the integration together with the help of many articles So I thought I might put my procedure up as I have to do this again in production.
I also hope it helps others.
Disclaimer, I have not actively tested that this works with an ISE authorization or authentication policy and additional permissions and policies may have to be added.
***** Install the Azure Certificate into ISE *****
Download the Baltimore Certificate from https://portal.azure.com
Click the Padlock Icon on address bar
Click Certificate (valid)
Change to Certification Path Tab
Select the Baltimore Certificate
Click View Certificate
Change to the Details Tab
Click Copy to File...
Save the Certificate and close all Certificate windows.
login to ISE Portal
Navigate to Administration -> System -> Certificate
Navigate to Trusted Certificates
Import the Downloaded Baltimore Certificates
Proceed through the SHA1 Warning and Duplicate warning to complete the install.
***** Generate ISE Key for upload to Azure *****
Login to ISE Portal
Navigate to Administration -> System -> Certificates
Navigate to System Certificates
Select the Default Self Signed or other Signed Certificate
Export the certificate
***** Generate and record the base64 Certificate details *****
Open Powershell ISE
Add the following power command to the script pane:-
$certpath = "<<Path to certificate>>"
$cer = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2
$cer.Import("$certpath")
$bin = $cer.GetRawCertData()
$base64Value = [System.Convert]::ToBase64String($bin)
$bin = $cer.GetCertHash()
$base64Thumbprint = [System.Convert]::ToBase64String($bin)
$keyid = [System.Guid]::NewGuid().ToString()
"KeyThumbprint: $base64Thumbprint" | Out-Host
"keyID: $keyid" | Out-Host
"keyValue: $base64Value" | Out-HostReplace <<path to certificate>> with you certificate and path like C:\Certs\ISE.cer
Record the KeyThumbprint, KeyID and KeyValue
Note: when used the keyValue need to be on a single line without line breaks.
***** Create New Azure Application *****
Login to Azure
Navigate to Azure Active Directory
Navigate to App registrations
Add New Registration
Name: ISE
Supported Account types: Single Tenant
Redirect URI: Web
URI: "blank"
***** Upload ISE Certificates into ISE Application *****
Navigate to Azure Active Directory
Navigate to App registrations
Select ISE Application
Navigate to Manifest
Download Manifest (Do not rename)
Modify Line:
From:
"keyCredentials": [],
To:
"keyCredentials": [
{
"customKeyIdentifier": "<<KeyThumbprint>>",
"keyId": "<<KeyID>>",
"type": "AsymmetricX509Cert",
"usage": "Verify",
"value": "<<KeyValue>>"
}
],Replace <<KeyThumbprint>> with ISE Certificate KeyThumbprint recorded earlier
Replace <<KeyID>> with ISE Certificate KeyID recorded earlier
Replace <<KeyValuet>> with ISE Certificate KeyValue recorded earlier
If a 2nd Certificate is needed download and obtain the base64 values and modify the Manifest file with an additional customKeyIdentifier
"keyCredentials": [
{
"customKeyIdentifier": "<<KeyThumbprint1>>",
"keyId": "<<KeyID1>>",
"type": "AsymmetricX509Cert",
"usage": "Verify",
"value": "<<KeyValue1>>"
},
{
"customKeyIdentifier": "<<KeyThumbprint2>>",
"keyId": "<<KeyID2>>",
"type": "AsymmetricX509Cert",
"usage": "Verify",
"value": "<<KeyValue2>>"
}
],Finally Upload New Manifest File to ISE App
***** Configure Azure Permissions *****
Navigate to Azure Active Directory
Navigate to App registrations
Select ISE Application
Navigate to API Permissions
Remove existing - Microsoft Graph - Delegated - User.Read
Add the Following Permissions
Microsoft Graph
Delegated
offline_access - Maintain access to data you have given it access to
openid - View users basic profile
Application
Directory.Read.All - Read directory data
Intune
Application
get_device_compliance - Get device state and compliance information from Microsoft Intune
Grant admin consent if required.
***** Record Required Values for ISE *****
Navigate to Azure Active Directory
Navigate to App registrations
Select ISE Application
Navigate to Overview
Record Values for Application (client) ID:
Select Endpoints
Copy Values for:
Microsoft Graph API endpoint:
OAuth 2.0 token endpoint (v1):
***** Create External MDM In ISE *****
Login to ISE Portal
Navigate to Administration -> Network Resources -> External MDM
Add New MDM Server
Name: Azure_Intune_MDM
Server Type: Mobile Device Manager
Authentication Type: OAuth - Client Credentials
Auto Discovery: Yes
Auto Discovery URL: Use the Value from Microsoft Graph API endpoint
Client ID: Use the Value from the Application (client) ID
Token Issuing URL: Use the value from the OAuth 2.0 token endpoint (v1)
Token Audience: Leave at default (prepopulated - https://api.manage.microsoft.com/)
Description: Azure Intune MDM
Polling Interval: 240
Time Interval for Compliance Device ReAuth Query: 1
Status: Enabled
Notes: Microsoft Graph API endpoint may need to be adjusted if not working with recorded value.
Use https://graph.windows.net/<<tenant-id>>
<<tenant-id>> can be found on OAuth 2.0 token endpoint (v1) URL
https://login.microsoftonline.com/<<tenant-id>>/oauth2/token
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2020 12:08 AM
Nice Tnx! For helping out the community.
maybe cisco can give us some free ISE licenses because god it is expensive :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2020 08:53 AM
HI
we are planning to integrate our ISE as well to to Azure AD, so we can use our endpoint to use Cert based authentication insted of password to ISE. Is there a step by step guide on the a) ISE side to configure CERT based authentication for end points. b) Azure side configuration c) end point side configuration and d)any configuration needs to be done on the NAD side.
thanks
karthik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2020 09:48 AM
Hi Karthik,
I am assuming you want to authenticate your users on your company WIFI infrastructure. I don't know of any step by step guide but for certificates you will have to look at SCEP
https://docs.microsoft.com/en-us/mem/intune/protect/certificates-scep-configure
You are looking at EAP-TLS for you wifi then using device authentication.
http://www.labminutes.com/sec0274_ise_22_wireless_dot1x_eap_tls_peap_1
Firs step is getting you certificates on your devices. You wan also use ISE for this with BYOD.
Maybe if you explain your use case a little more somebody can help you out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2020 10:03 AM
Hi Federek
currently we have, a)WIFI - PEAP with password based authentication we are now, from this we are looking for EAP-TLS with certificate based authentication so it will be password less. b) WIRED - .1x authentication we are using. we are looking to completely migrate certificate based authentication.
Thanks
karthik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2021 11:26 PM
Agree, That is a lot of certificate not publish on the documentation.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide