- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE - IP Phone 802.1X | AuthC Errors
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2022 02:43 PM
Hello Team,
I hope you all are very well.
I'm trying to authenticate a SIP-T31G (Yearlink IP Phone) with ISE via 802.1X, but I'm facing some issues. The IP Phone didn't authenticates and ISE shows error logs as failed TLS handshake.
Config in the IP Phone side:
- AuthC via PEAP-MSCHAPv2;
- User and Passwd inserted;
- I have selected the option to accept untrusted certificate, just to discard the possibility of the Phone didn't trust the ISE presented cert;
Config in the ISE side:
Allowed Protocols:
- Allowed Protocol allowing PEAP with MSCHAPv2;
- Allowing EAPv0 (I have testes with and without this option);
- Allowing Weak Ciphers (I have testes with and without this option);
- I also have tested with the default Allowed Protocols, but the same result
Authz Profile
- Just configured to send the voice vlan to the switch;
AuthZ Policy
- Conditions: Wired_802.1X and AD Group;
- Result: Voice Vlan AuthZ Profile
This same policy is working okay with a Grandstream IP Phone, but with the Yalink occurs the erros about the handshake. Other dot1x policies for User or Machine authentication is also working okay.
The Yalink IP Phone is authenticating normal, with the same config described above, with the Windows NPS Server. I saw the NPS policies and its the same I have configured in ISE.
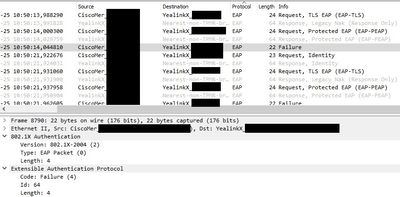
In a packet capture, we can see that ISE tried to request EAP-TLS response for IP Phone, but the IP Phone answered with a "Legacy NAK". After that, a new request is sent with PEAP, the endpoints returns with the response, but in the sequence, the switch/ISE sends a failure message as reply.
PS.: The switch used in this environment is a Meraki MS210.
Can it be compatibility problem between ISE and Yalink?
Please, see below the ISE log and a snippet of the packet capture.
SSL alert: code=0x246=582 ; source=local ; type=fatal ; message=" protocol version.ssl/statem/statem_srvr.c:1686 error:14209102:SSL routines:tls_early_post_process_client_hello:unsupported protocol [error=337678594 lib=20 func=521 reason=258
140188854318848:error:14209102:SSL routines:tls_early_post_process_client_hello:unsupported protocol:ssl/statem/statem_srvr.c:1686
Thanks in advanced.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2022 08:40 PM - edited 07-25-2022 08:40 PM
Depending on your version of ISE, the phone may be trying to negotiate an older TLS version that ISE does not support by default.
I would suggest having a look at the Administration > System > Settings > Security Settings page and enabling any TLS versions that might be disabled by default (like TLS 1.0 in ISE version 3.x).
If that doesn't solve the issue, you might need to open a TAC case to investigate in more detail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-25-2022 08:40 PM - edited 07-25-2022 08:40 PM
Depending on your version of ISE, the phone may be trying to negotiate an older TLS version that ISE does not support by default.
I would suggest having a look at the Administration > System > Settings > Security Settings page and enabling any TLS versions that might be disabled by default (like TLS 1.0 in ISE version 3.x).
If that doesn't solve the issue, you might need to open a TAC case to investigate in more detail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-26-2022 08:03 AM
Hello, @Greg Gibbs !
I have analyzed the entire flow in the packet capture and can see that the endpoint was sending hello via TLSv1 and Cisco ISE was rejecting. So, as you suggested, I have enabled the TLSv1 in the ISE's Security Settings and the authentication works okay.
Thank you for your reply!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide