- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE limit vpn access by client source ip
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE limit vpn access by client source ip
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 08:04 AM
Hello,
Is it possible to use client ip address to limit vpn access
i.e write authorization policy which would use Cisco-AVPair = "ip:source-ip=ip.add.re.ss"
or Calling-Station-ID to match against defined subnet
As per documentation both are of type string and i am not sure how to write these rules
or is it even possible
https://community.cisco.com/t5/security-documents/ise-network-access-attributes/ta-p/3616253
cisco-av-pair 1 The Cisco RADIUS implementation supports one vendor-specific option using the format recommendedin the specification. Cisco’s vendor-ID is 9, and the supported option has vendor-type 1, which is named“cisco-avpair.” The value is a string
Calling-Station-ID 31 string 1.0 Authentication
This Attribute allows the NAS to send in the Access-Request packet the phone number that the call came from, using Automatic Number Identification (ANI) or similar technology. It is only used in Access-Request packets.
For sure we can debate on whether this would be an optimal solution, but I'd still like to get an answer.
Thnx
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 08:54 AM - edited 11-27-2019 08:56 AM
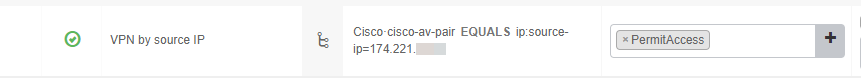
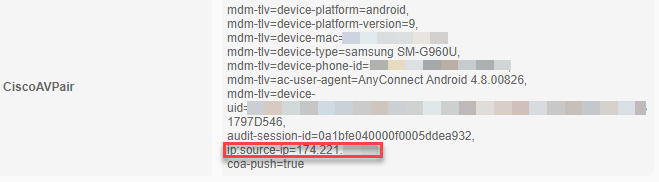
I assume your VPN client is AnyConnect? It should send over the source IP as you described as an av-pair attribute.
I just tested this use-case in my lab and it was successful. The policy looks like this:
Attributes sent are:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 12:39 PM
Thnx, but
Maybe I wasn't that clear or overlooked your answer somehow
Anyway, ASA (vpn gatewa) is indeed sending those attributes that is not in question.
What's puzzling me is how can I match src ip to a known subnet say /21
Obviously it is impossible to write rules with all those ip addresses and use
EQ string operator
Probably one would neet to cast it to address type and somehow match if it belongs to
a subnet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 01:05 PM
Hi
You can specify the subnet you want to match in an Endstation Network Condition under Policy > Policy Elements > Conditions > Network Conditions.
I've used this method in the past as a Policy condition - not sure if Endstation Network Conditions can be used as an Authorization condition.
hth
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 01:26 PM
You could probably match using a RegEx in the condition. What is the subnet you are trying to match on?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2019 09:04 AM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide