- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE / OKTA as Radius Token server - Authorization group okta
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE / OKTA as Radius Token server - Authorization group okta
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2022 02:38 PM
Hello,
I added OKTA to ISE as a Radius Token server, and it works fine
OKTA return RADIUS attribute "25 Class" for each group, example class attribute :
- ou=group1
- ou=group1;ou=group2
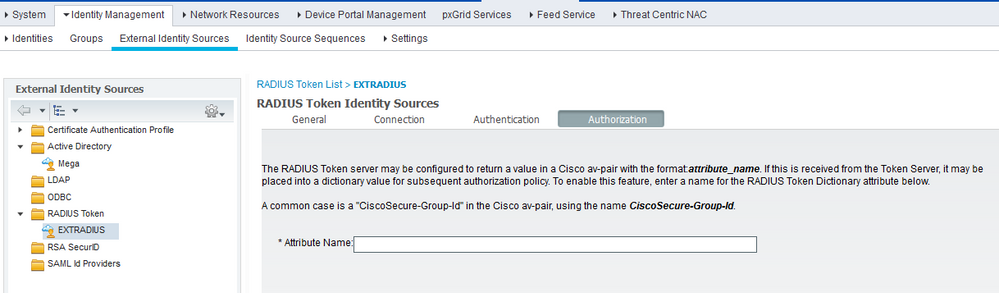
I see on Radius token server / authorization, I can configure CiscoSecure-Group-Id attribute or specify another (Class ?),
How can I exploit it so that I can use it during authorization (allow only if a user is in a specific group) ?
Thank you
- Labels:
-
AAA
-
Identity Services Engine (ISE)
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2022 08:11 PM
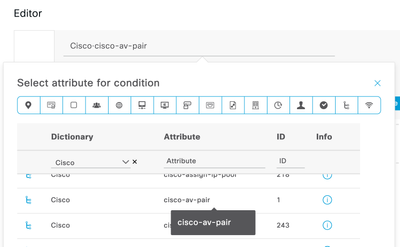
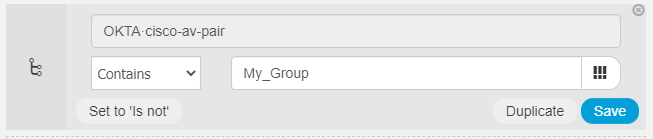
In your ISE Policy's Authorization Rule, create a condition with
Cisco:cisco-av-pair CONTAINS <group>
and see if that works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2022 04:52 AM
Hello @thomas
No work with Cisco:cisco-av-pair CONTAINS <group> !
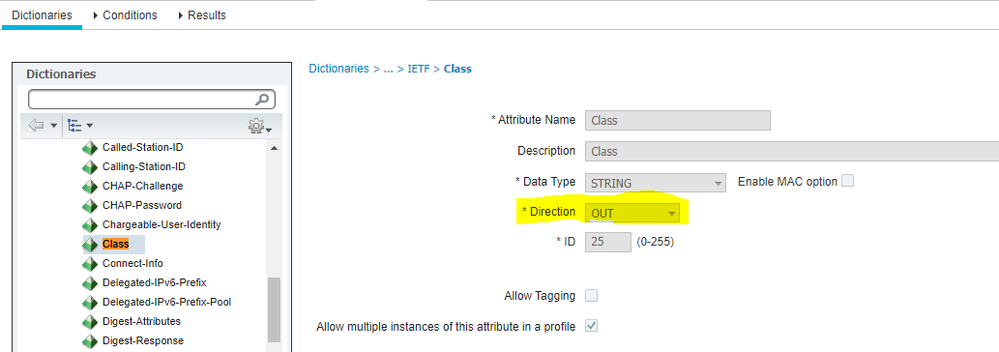
in ISE, Class is OUT attribute, I changed it to cisco-avpair in okta, but still not working!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2022 07:42 AM
Sorry, I don't know what "Class is OUT" means.
You need to provide some actual details for the community to help you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2022 08:03 AM
Hello @thomas
Thank you for your reply
"Class is OUT" => Direction
Here is my configuration
AuthZ rule :
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2022 07:45 PM
OKTA seems to have an LDAP interface. Could you not use that, instead?
Otherwise, Arne's reply in ISE as RADIUS Proxy and Attribute "Reply-Message"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2022 10:12 PM
It's been a while since I have used a token server in ISE but I recall that the reply message (from the token server) to ISE has to contain a Cisco AVPair that is formatted in such a way, that ISE can understand. From my research some years back, the reply has to contain Cisco AVPair as such
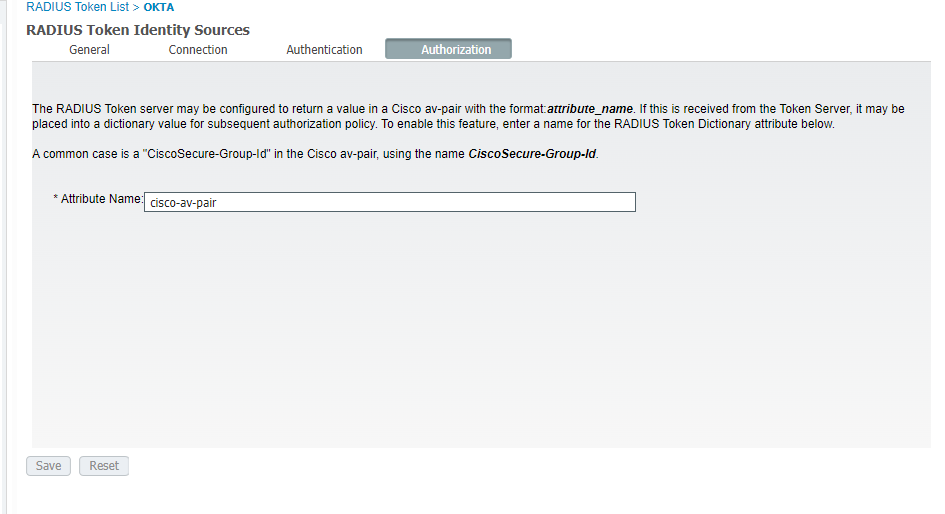
ACS:<whatever_attr_name_you_want>
Then you define that under RADIUS Token Identity Sources 'Authorization'. You will have the <whatever_attr_name_you_want> available in your AuthZ policies. If you don't use a custom name, then ISE defaults to CiscoSecure-Group-Id.
That means your external radius server needs to return a Cisco AVPair that looks like this (the User is in GroupXYZ) - you can't use anything other than a CiscoAVPair containing ACS...
So in your particular example, you have used Attribute Name of "cisco-av-pair" - this means, that OKTA has to reply to ISE with RADIUS attributes as shown below (two separate scenarios)
Cisco-AVPair = ACS:cisco-av-pair = Super-User
Cisco-AVPair = ACS:cisco-av-pair = Monitor-User
If this is the case, then your ISE Authorization rules will work - I explained it a bit more in the link that hslai shared.
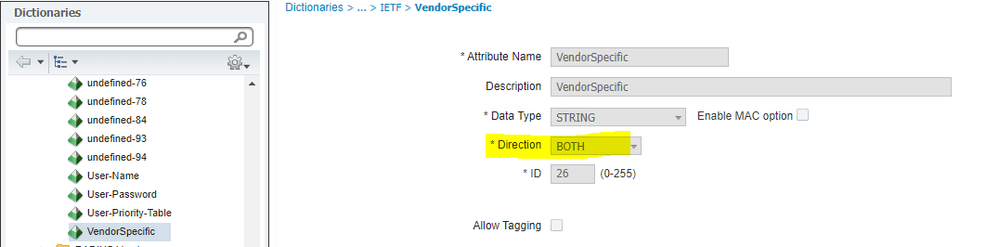
The question is whether OKTA will let you manipulate the RADIUS attributes sent to ISE? This OKTA link seems to imply that they support Vendor Specific (which is what Cisco-AVPair is using) - so hopefully you can make it work by pre-pending the ACS:blah to it?
Select the Vendor Specific option from the drop down and then see how you get on. Share the screenshot please since I don't have OKTA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2022 03:49 AM
Hello,
Thank you for your reply
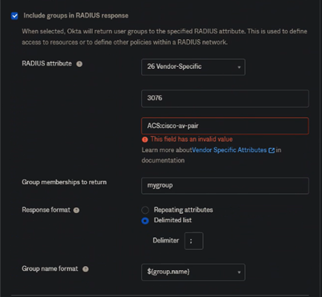
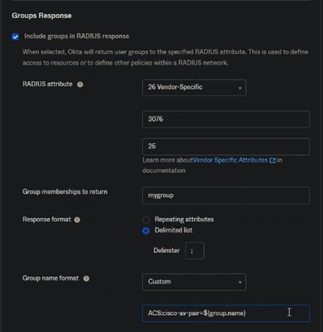
In OKTA, I have :
26-Vendor specific
25-Class
11-Filter-ID
I can specify "ACS:cisco-av-pair" only in "Group name format" which returned to ISE (check ok with wireshark)
Thank you very much
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2024 08:27 AM
Hi Sir,
I have recently integrated ISE's RADIUS TOKEN with OKTA. After entering the username and password on the Cisco switch, OKTA shows successful authentication, but I still see "% Authentication failed" on the switch.
OKTA shows the authentication was successful, and on ISE, I only see Authentication success, but there is no information regarding Authorization.
Could you please share your ISE and OKTA configurations for reference? Thank you.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide